I have participated in EG-CTF which is organized by EG-CERT and this a writeup for Process Enumeration a reverse engineering CTF challenge.
Download CTF binary executable Here
Enumeration
First I tried to run the Process_Enum.exe file and this is the output i got.
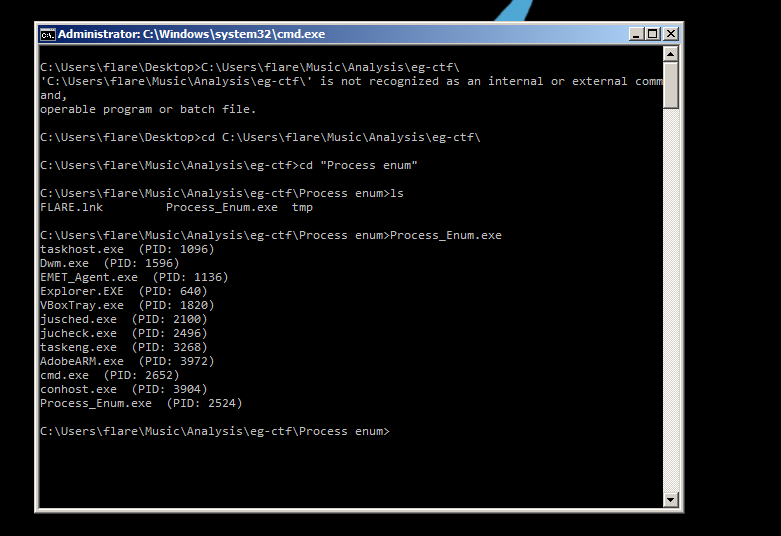
So what i get here is that executable file enumerating the running processes in my machine nothing else, so i have opened it in IDA to analyze what it is doing exactly.
So it’s just a PE file, and let us see the binary strings first.
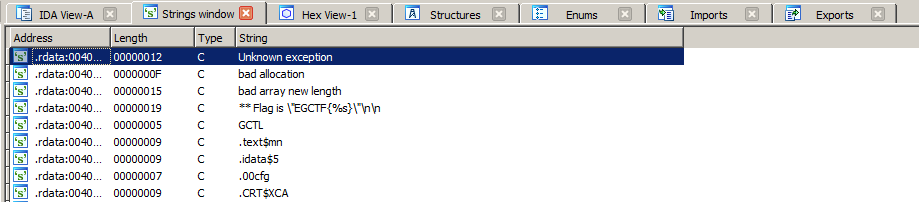
There is an interesting string right here:
** Flag is \"EGCTF{\%s}\"\n\n
So our flag will go right there, i clicked it to see it in .rdata section.
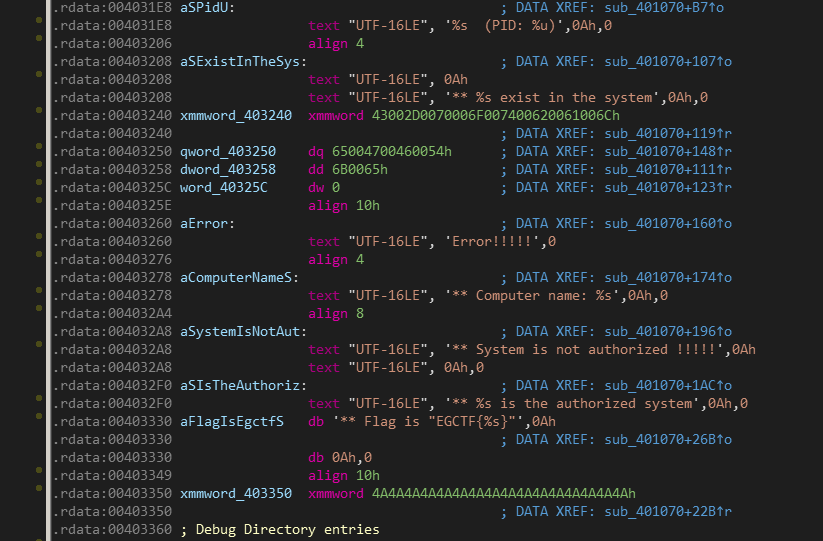
There is more interesting strings right here that we should go for each one of them.
** %s exist in the system
Error!!!!!
** Computer name: %s
** System is not authorized !!!!!
** %s is the authorized system
now lets see the data XREF for these strings by double clicking the DATA XREF: sub_401070+B7 to see what are these strings being used.
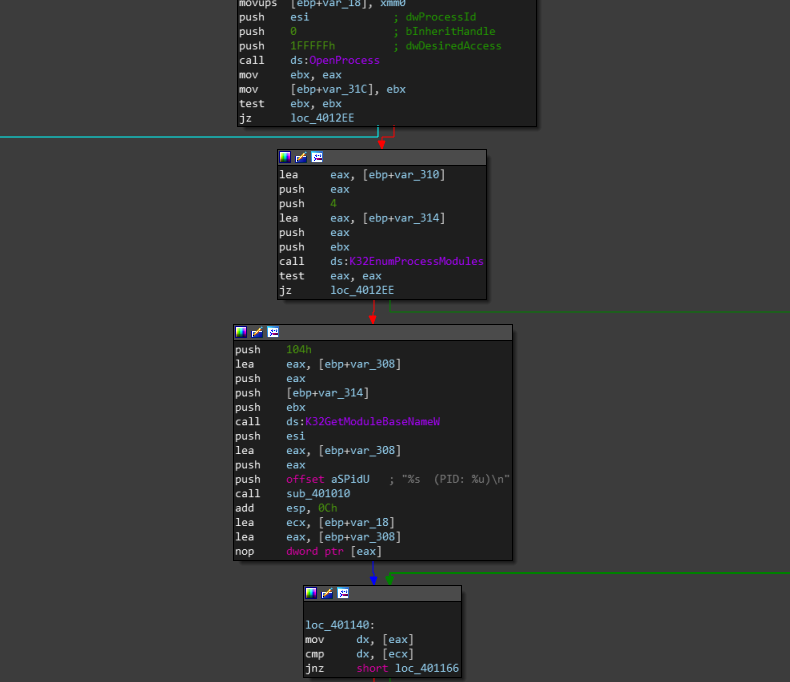
this is the instructions for getting running processes with its PID.
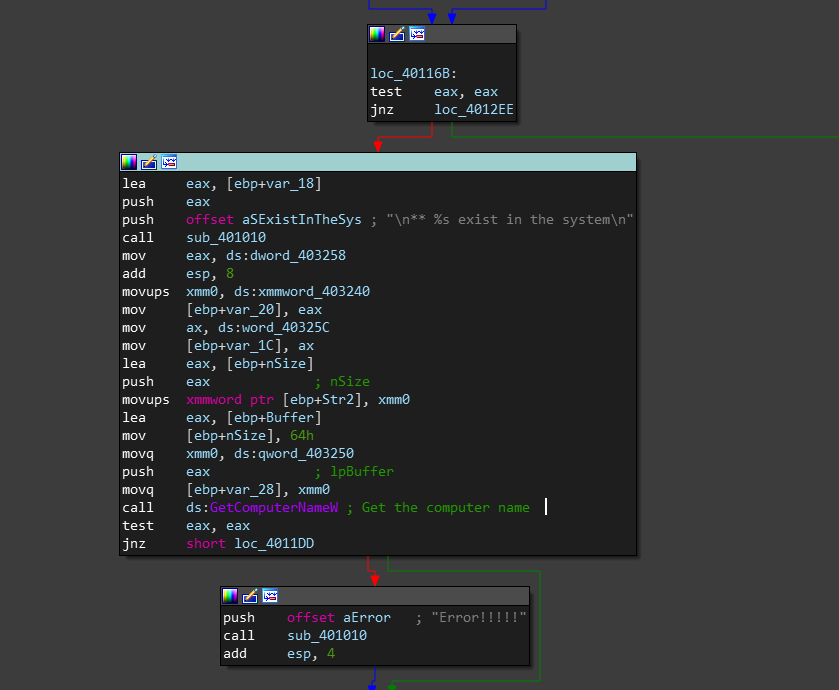
and what i understand here that while enumerating the running processes it checks for a specific process name and if exists will print ** PROCNAME.EXE is exists in the system and then getting the machine pc name NetBIOS name by calling GetComputerNameW function, and then making a short jump if not equal something to print Error!!!!!.
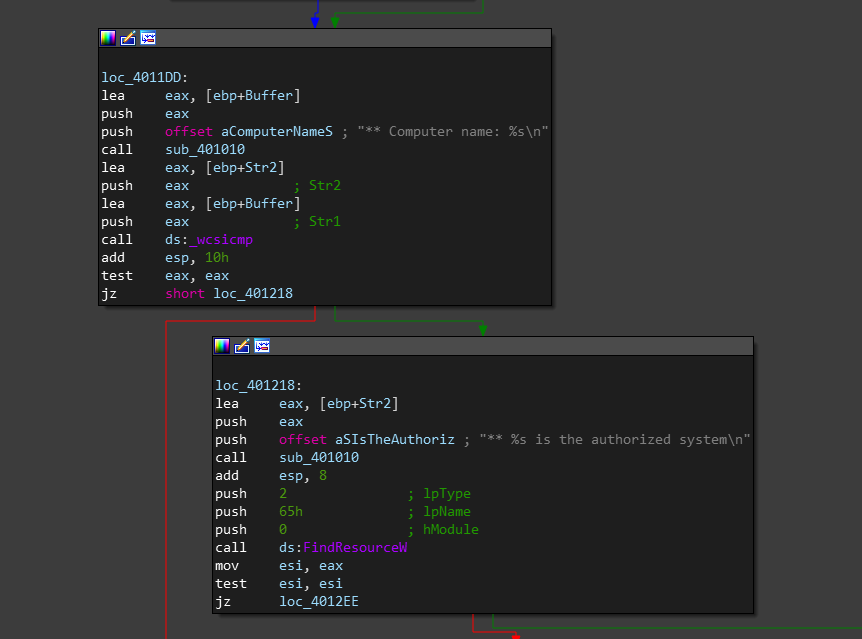
if the requirements are met it will print ** Computer name: NAME and it’s comparing two strings and then short jump if true to instructions that prints ** SOMETHING is the authorized system

and after that it goes to a set of instructions that leads to our flag.
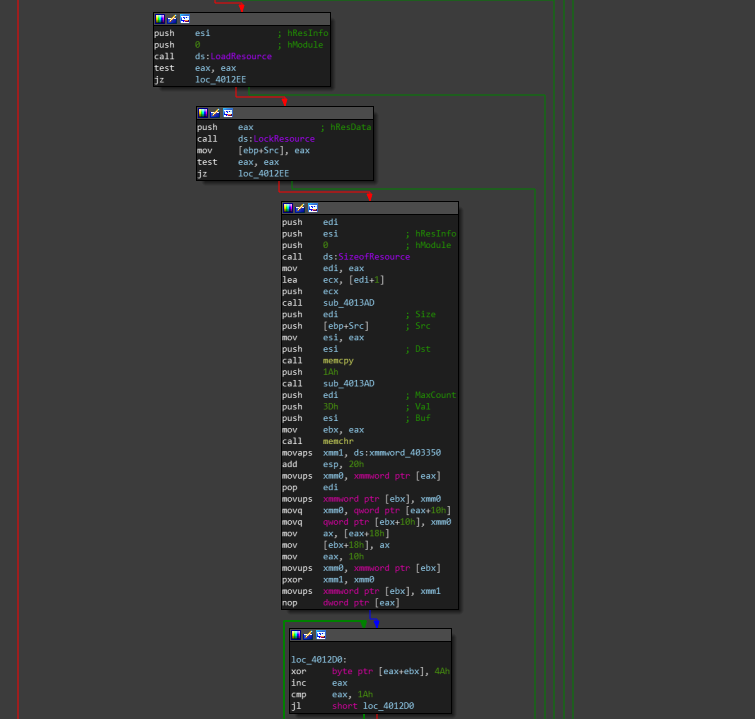
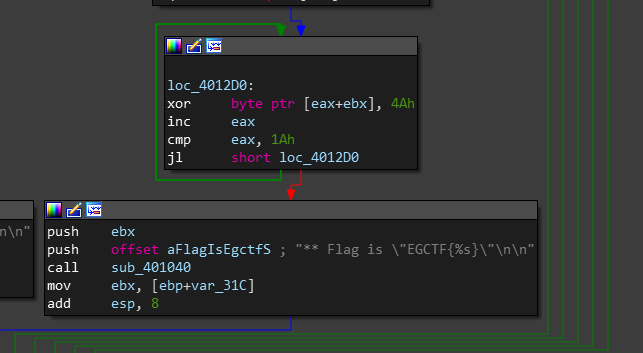
so i have to debug that binary for better understanding, In this case i will use x64dbg debugger.
Debugging
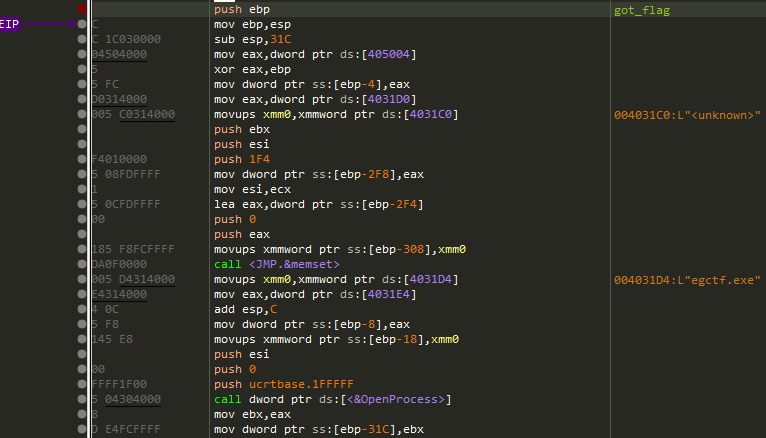
While debugging i see that when the executable enumerating the processes it checks for egctf.exe.
so what i have done is renaming the binary itself to egctf.exe
and running it again.
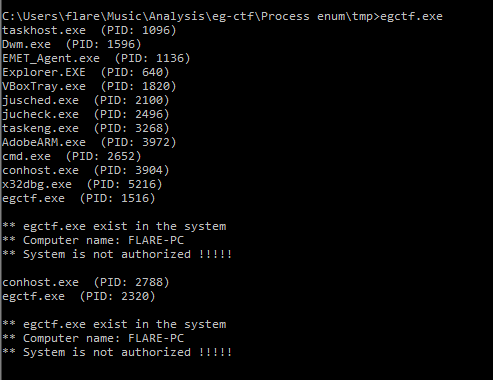
it has printed more information after checking for egctf.exe process and it looks like it is checking for computer name ** Computer name: FLARE-PC.
While analyzing the executable in IDA we saw a string ** %s is the authorized system which explain that ** System is not authorized !!!!! string is printed because it checks for the current user privilages to see it has SYSTEM privilages or not.
Alright, let us debug the new renamed executable file.
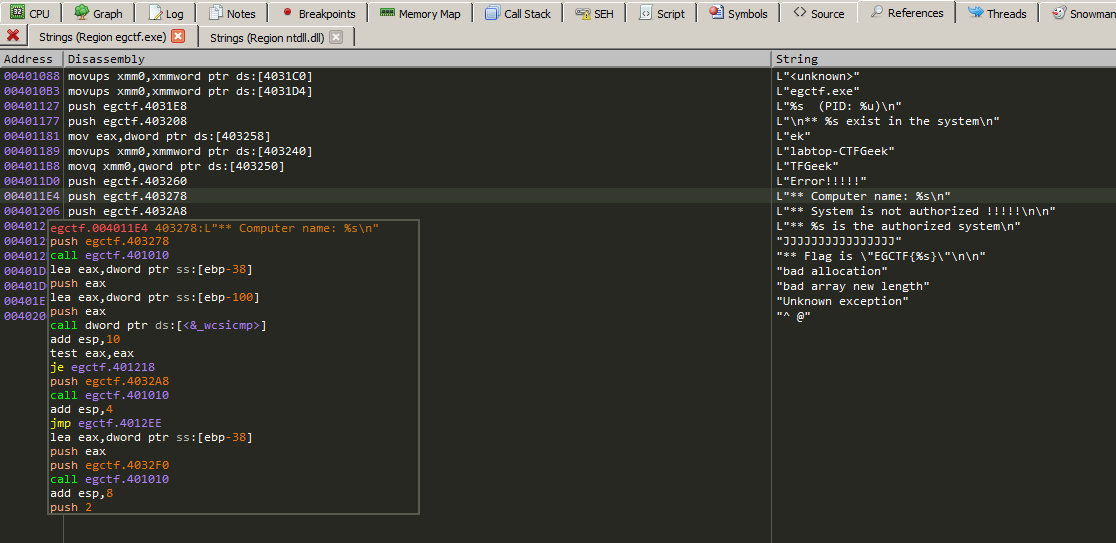
And double clicking the ** Computer name: %s string
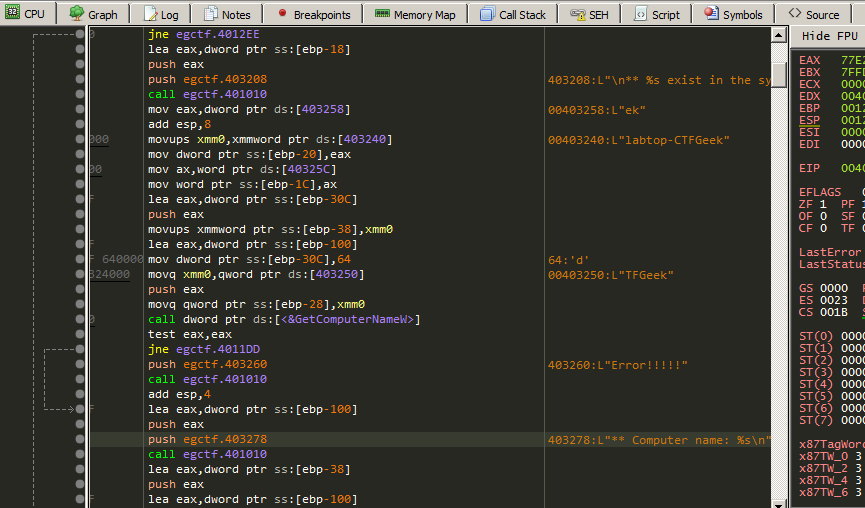
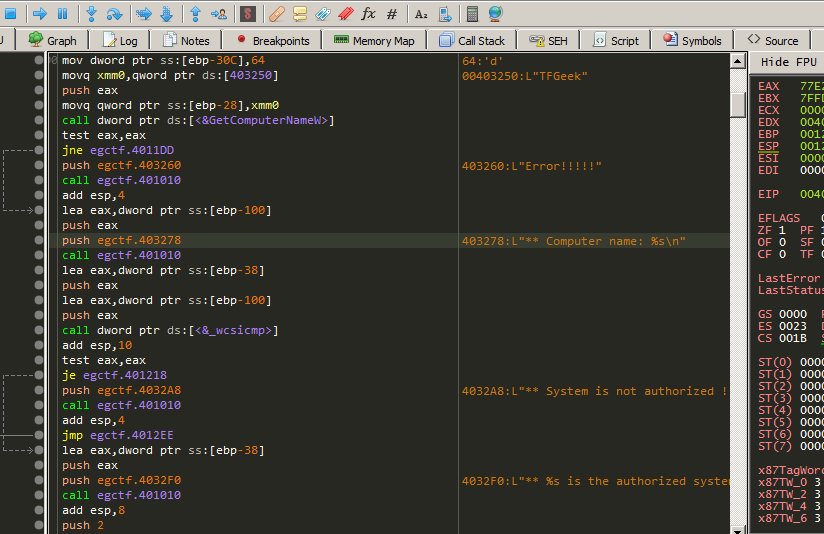
And i have set a breakpoint on it and pressed F9 to run.
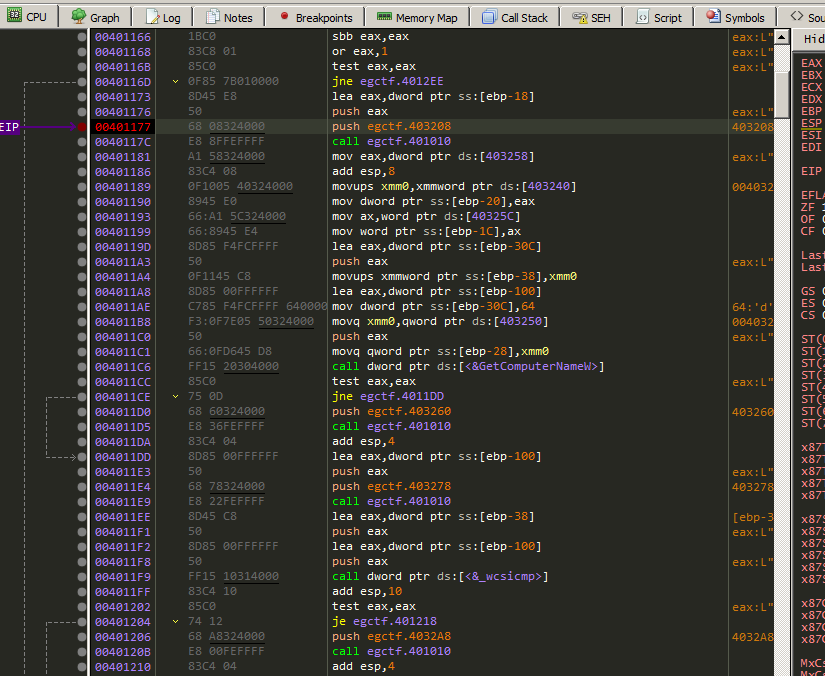
Steping through some instructions and it’s setting a value to EAX labtop-CTFGeek and pushing to the stack and then calling wciscmp to compare it with the local machine name from GetComputerNameW function.
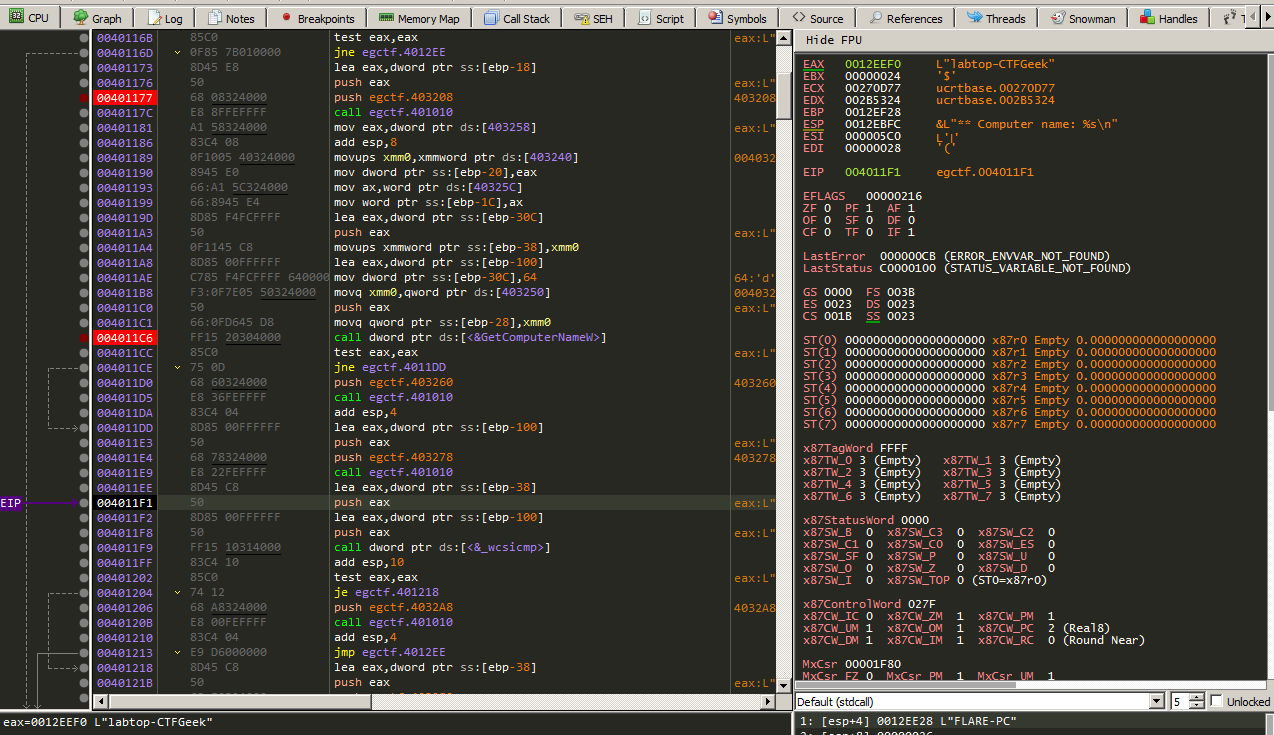
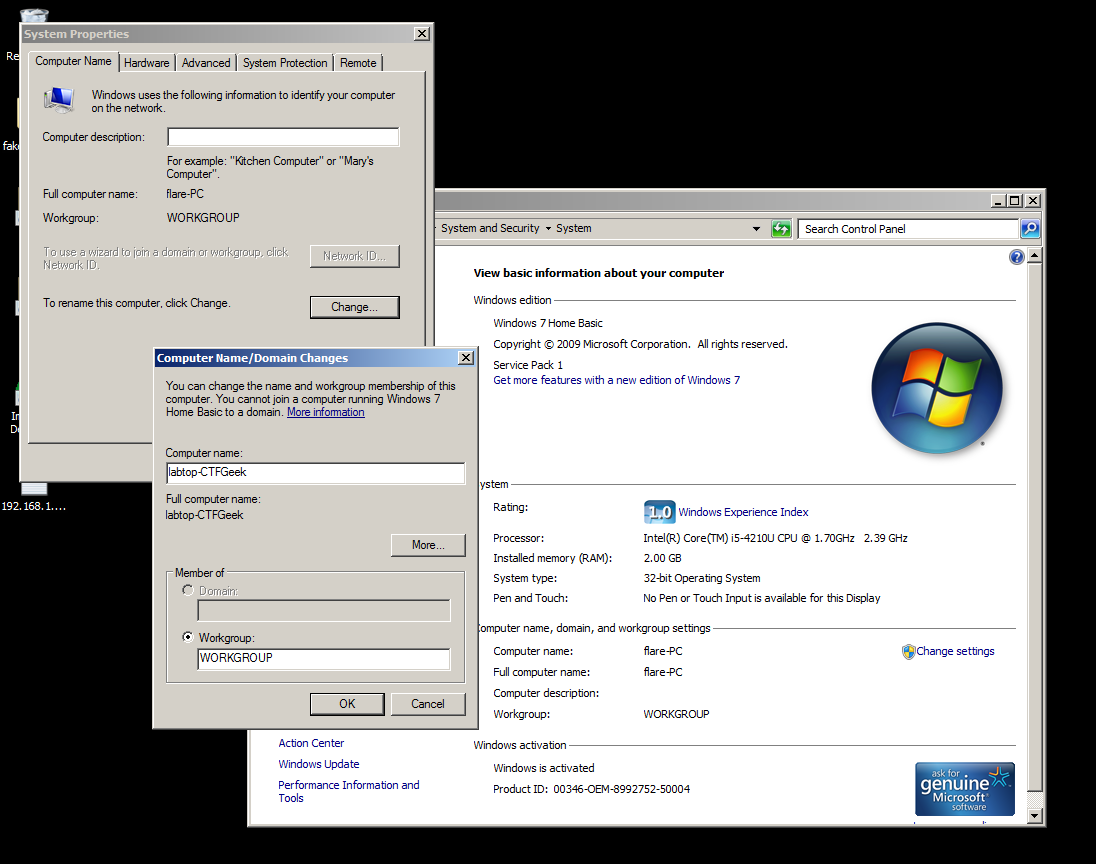
So what to do now is to rename the computer name to labtop-CTFGeek
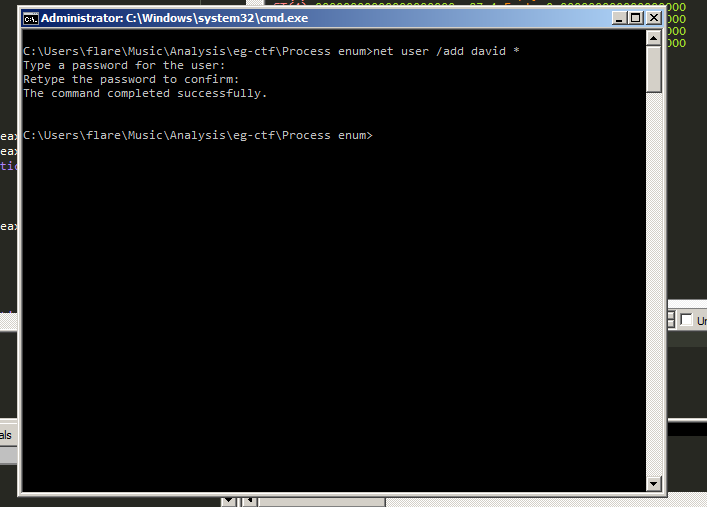
And adding a user with low privilage
Then restarting the machine and login to our new user

And run the renamed executable file
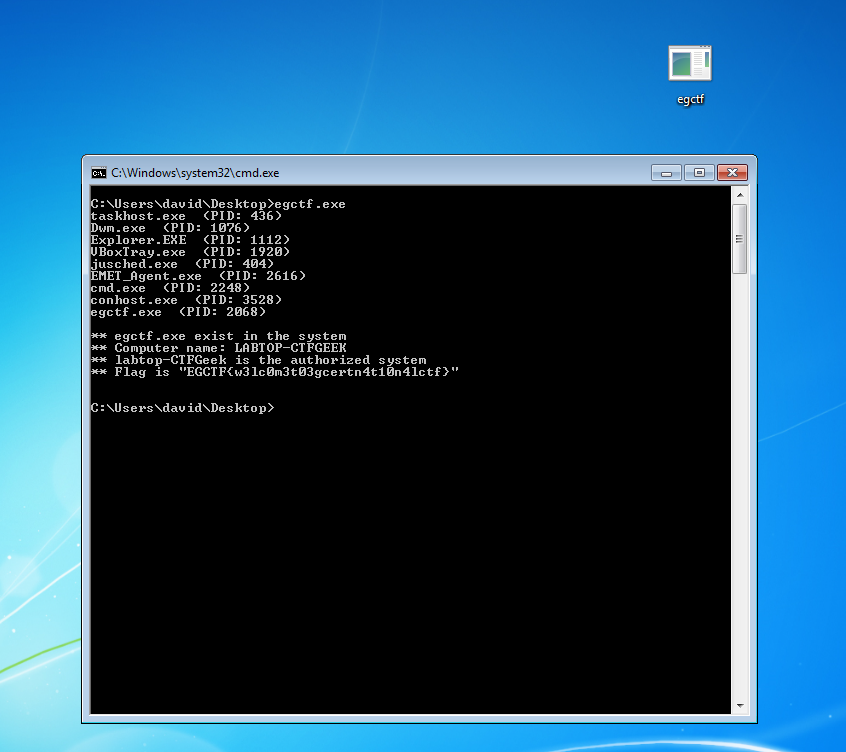
And here is the flag xD
EGCTF{w3lc0m3t03gecertn4t10n4lctf}
Hope u enjoyed this post.