I have participated in EG-CTF which is organized by EG-CERT and this a writeup for snowball, a reverse engineering CTF challenge.
Download CTF binary executable Here
Enumeration
First I checked the file type and extract some info about that binary, it’s ELF x64 stripped binary executable.
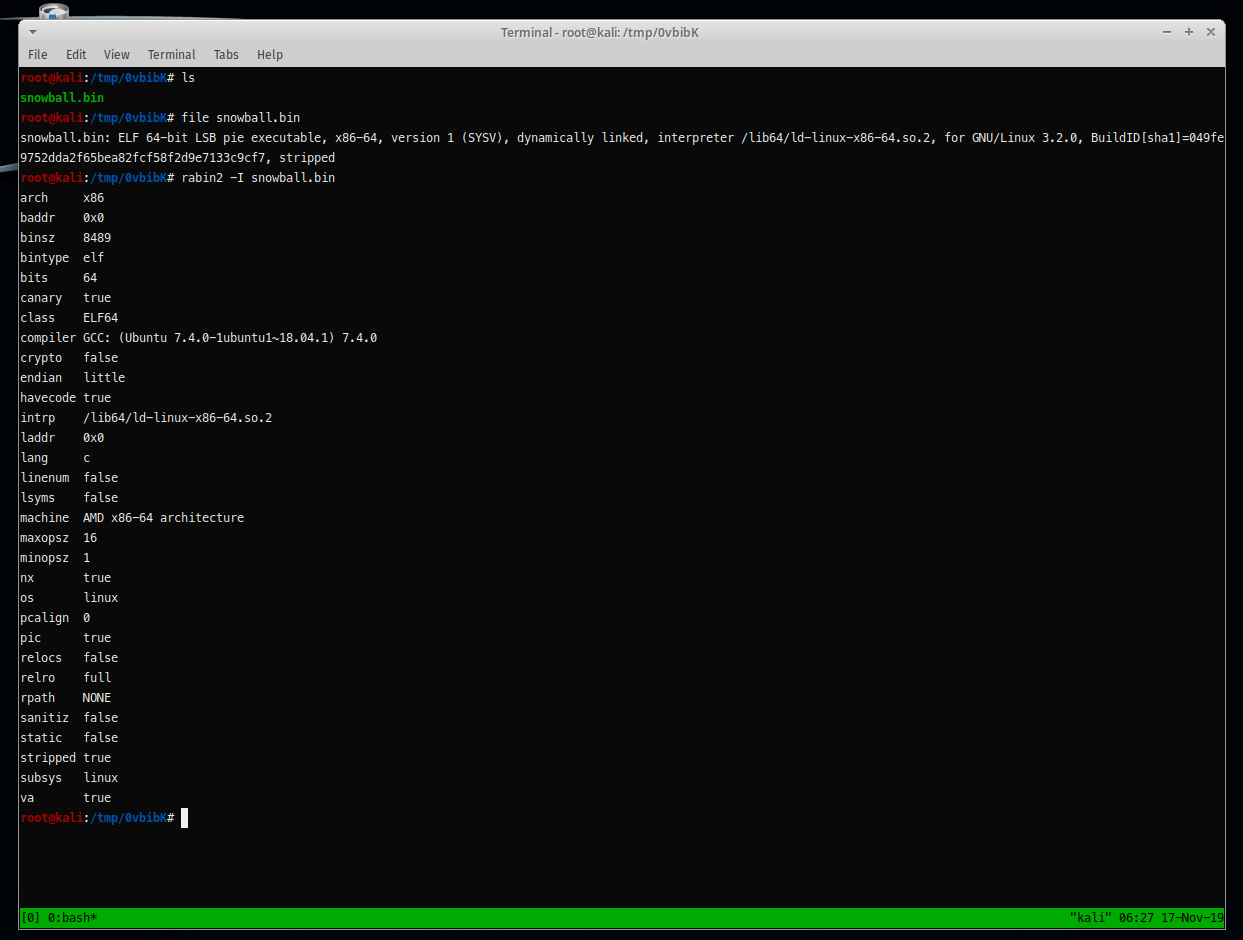
Then I tried the to extract the binary strings and got some interesting strings.
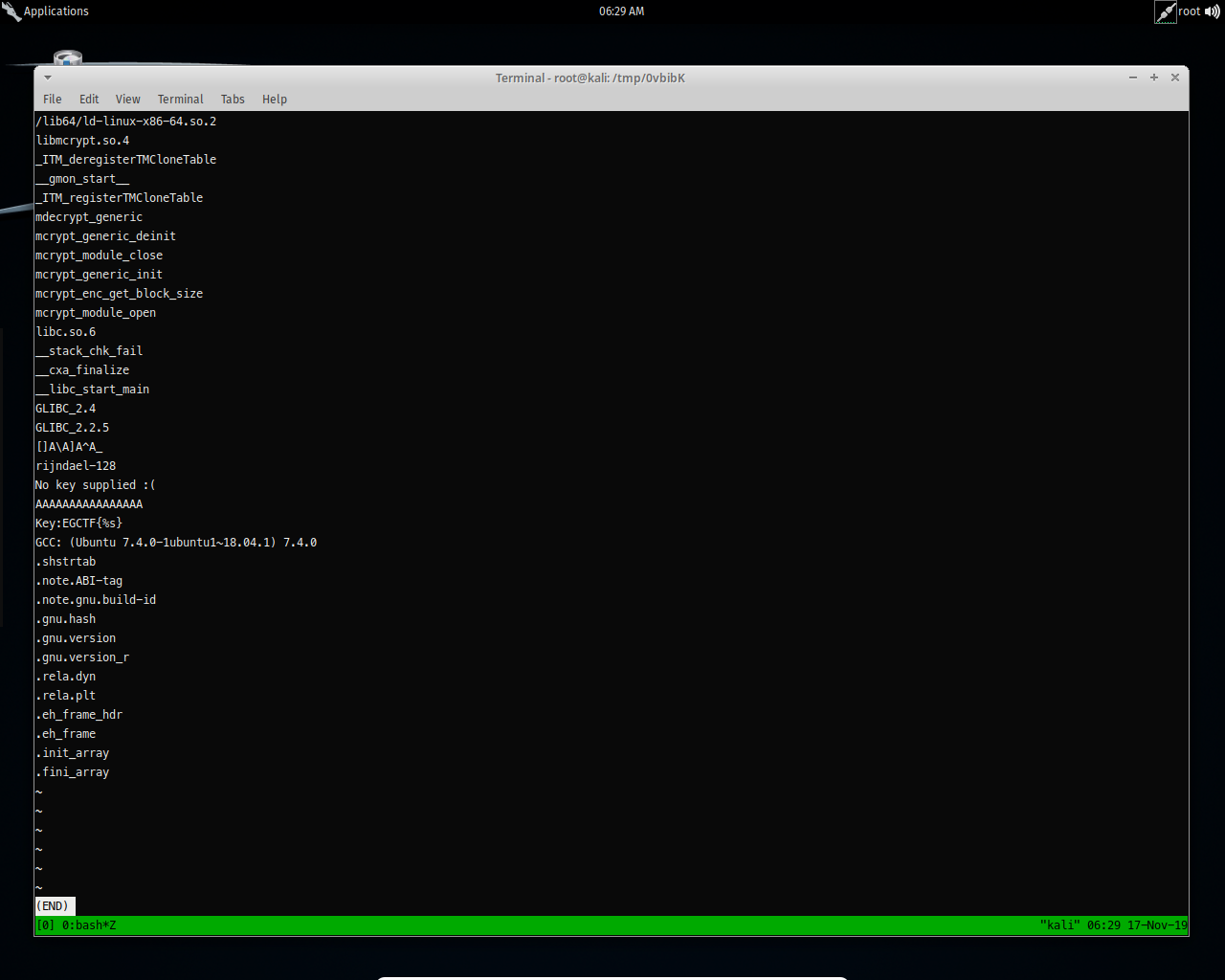
And then running the binary.

Lets open the binary in radare2 to analyze it and see what it actually does.
Analysis
First I have opened the binary in radare2 and analyzing its functions.
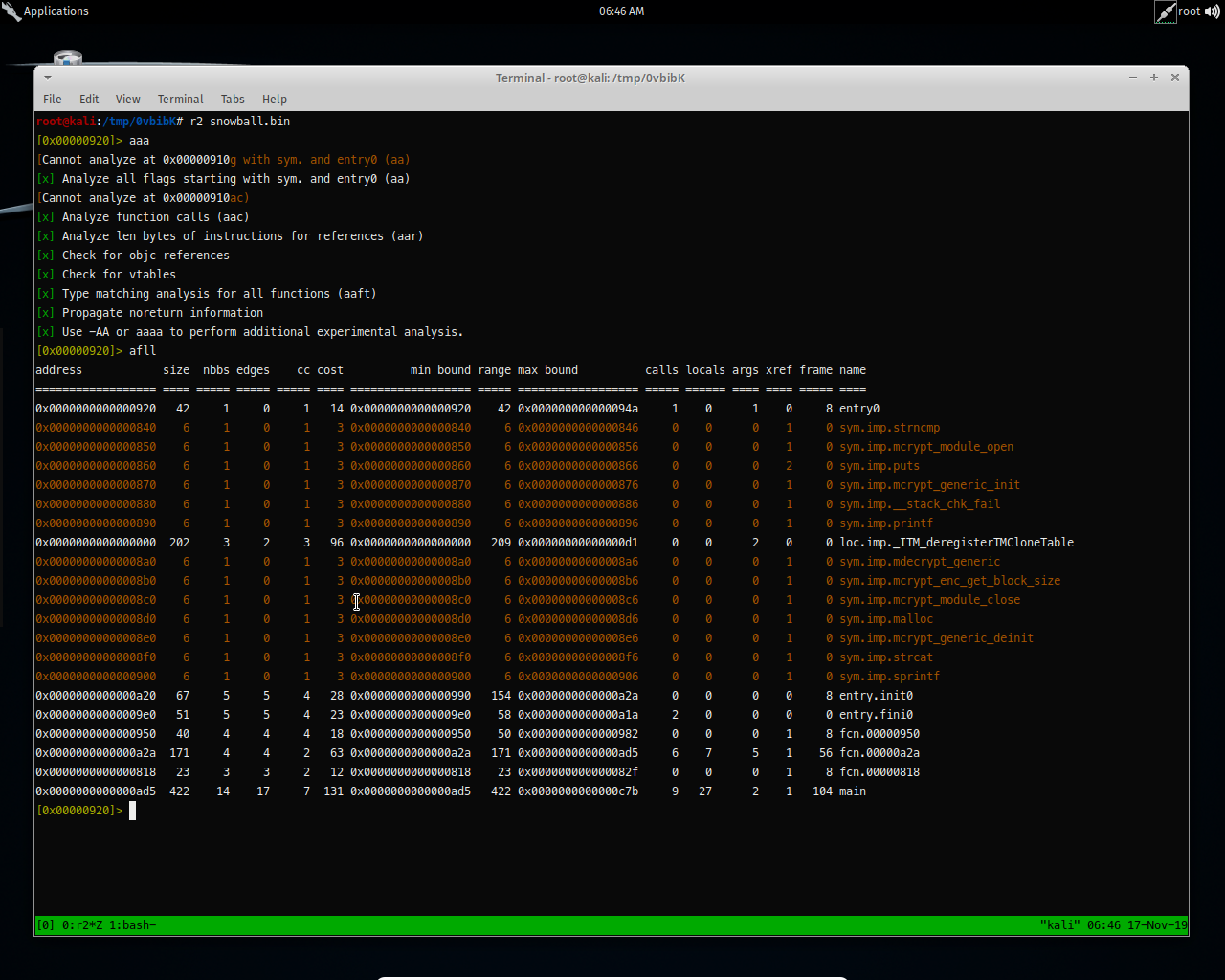
I got main function right there, let us analyzing it.
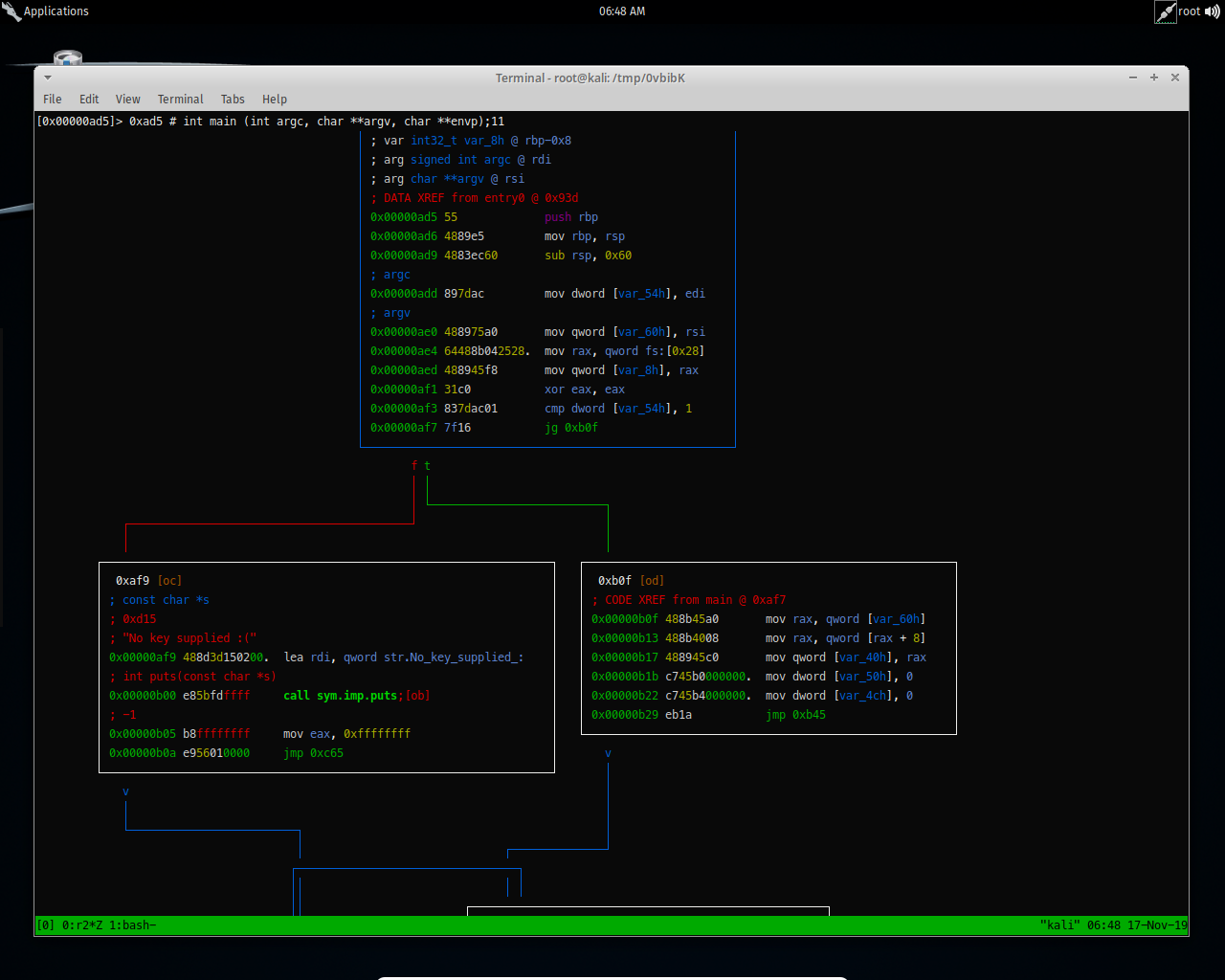
It’s checking for the for the key supplied by counting the arguments, if no argument specified it will print No key supplied then exit.
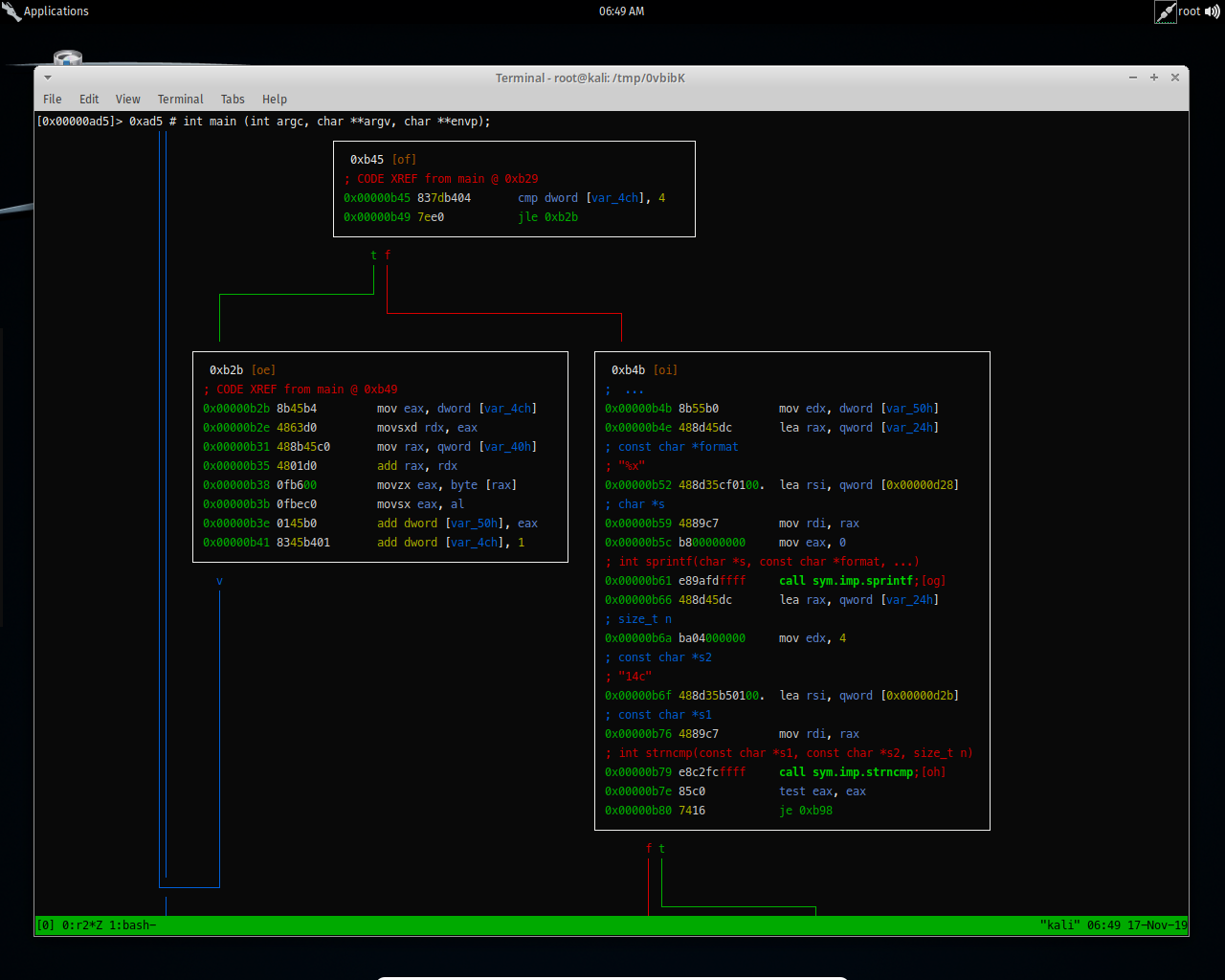
And here it’s comparing the given argument with 14c.
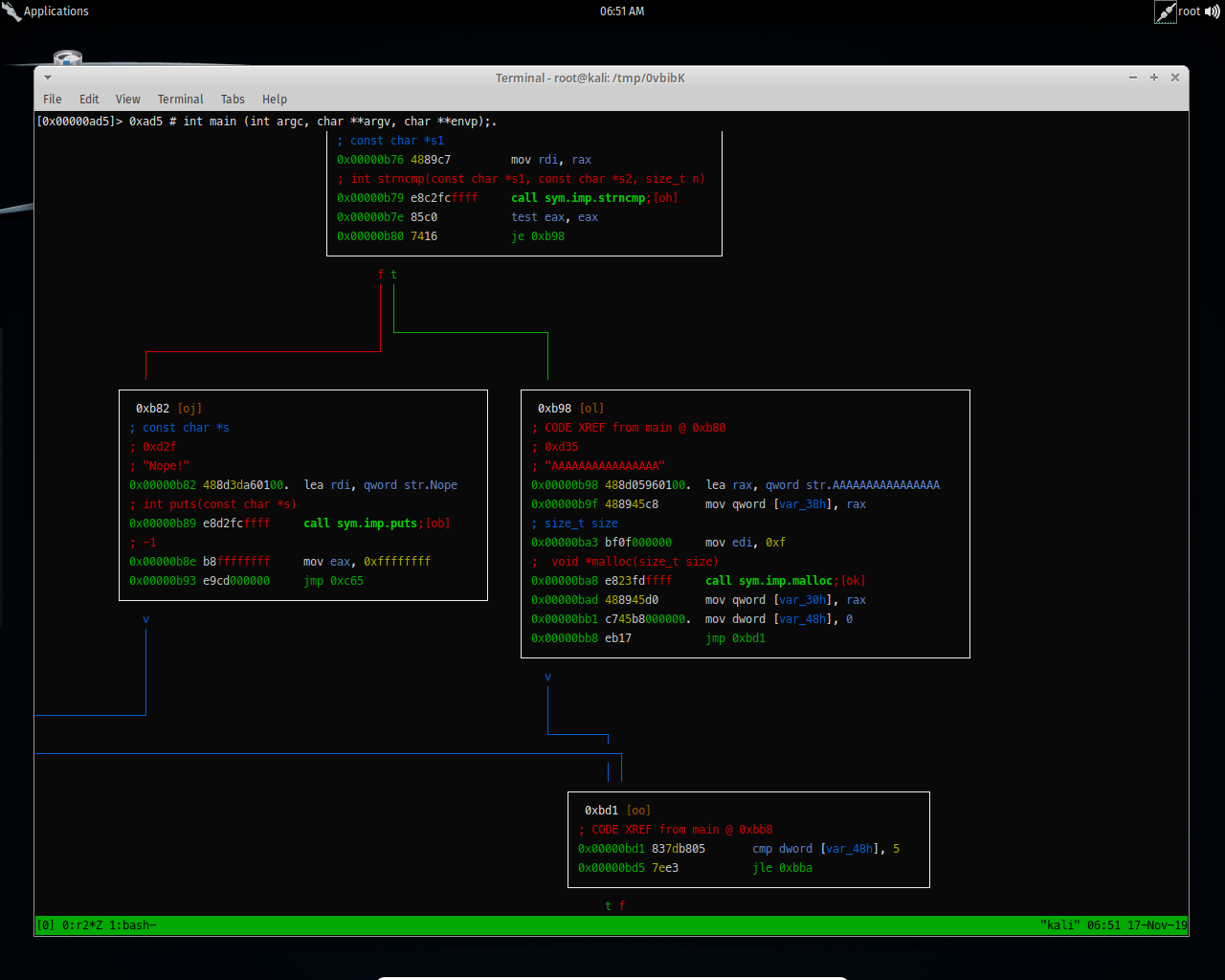
So if it’s false, it will print Nope! and exit.
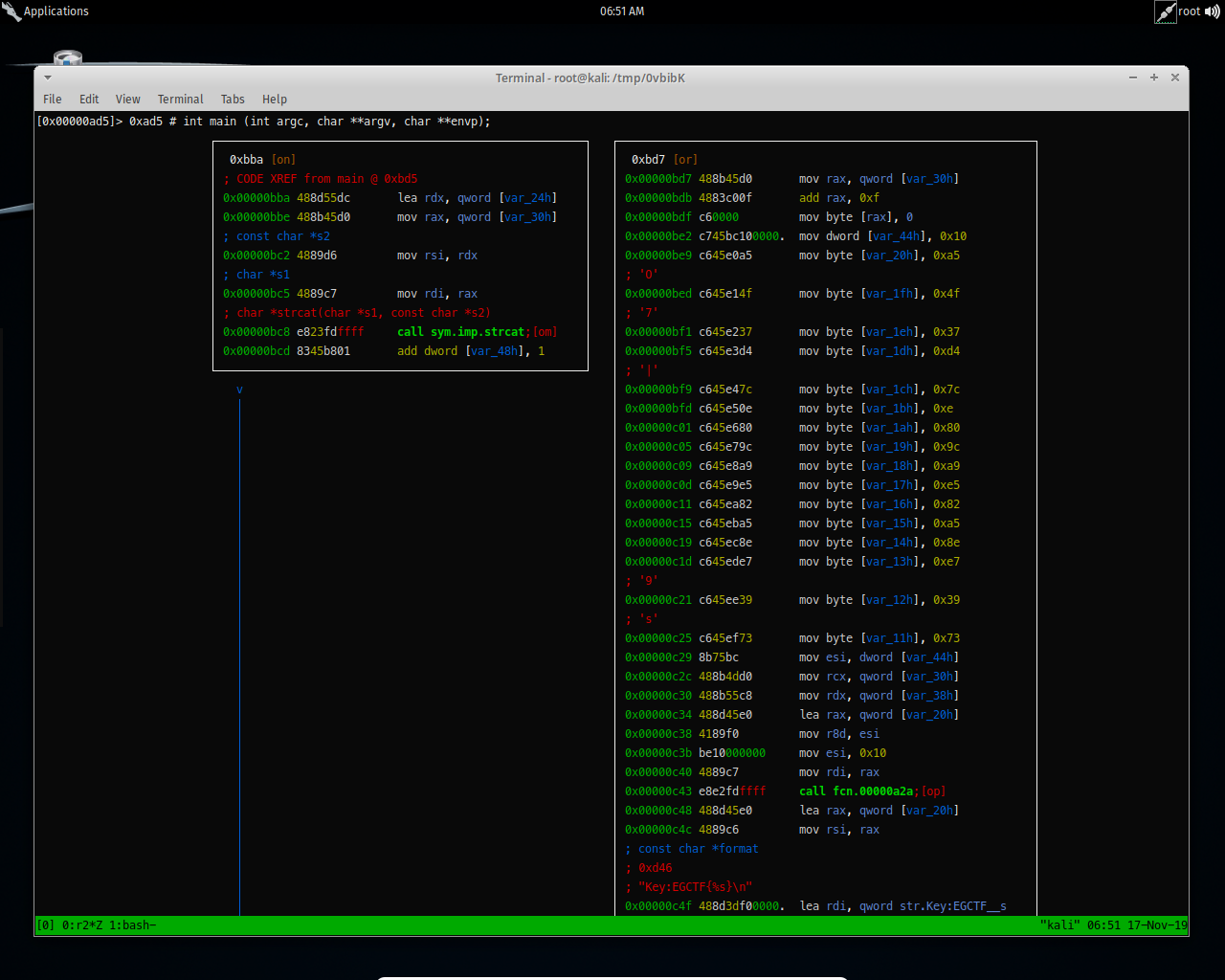
And if it’s true, it will go to these set of instructions and print the flag, what i see here interesting also is that function call fcn.00000a2a, so lets analyze this.
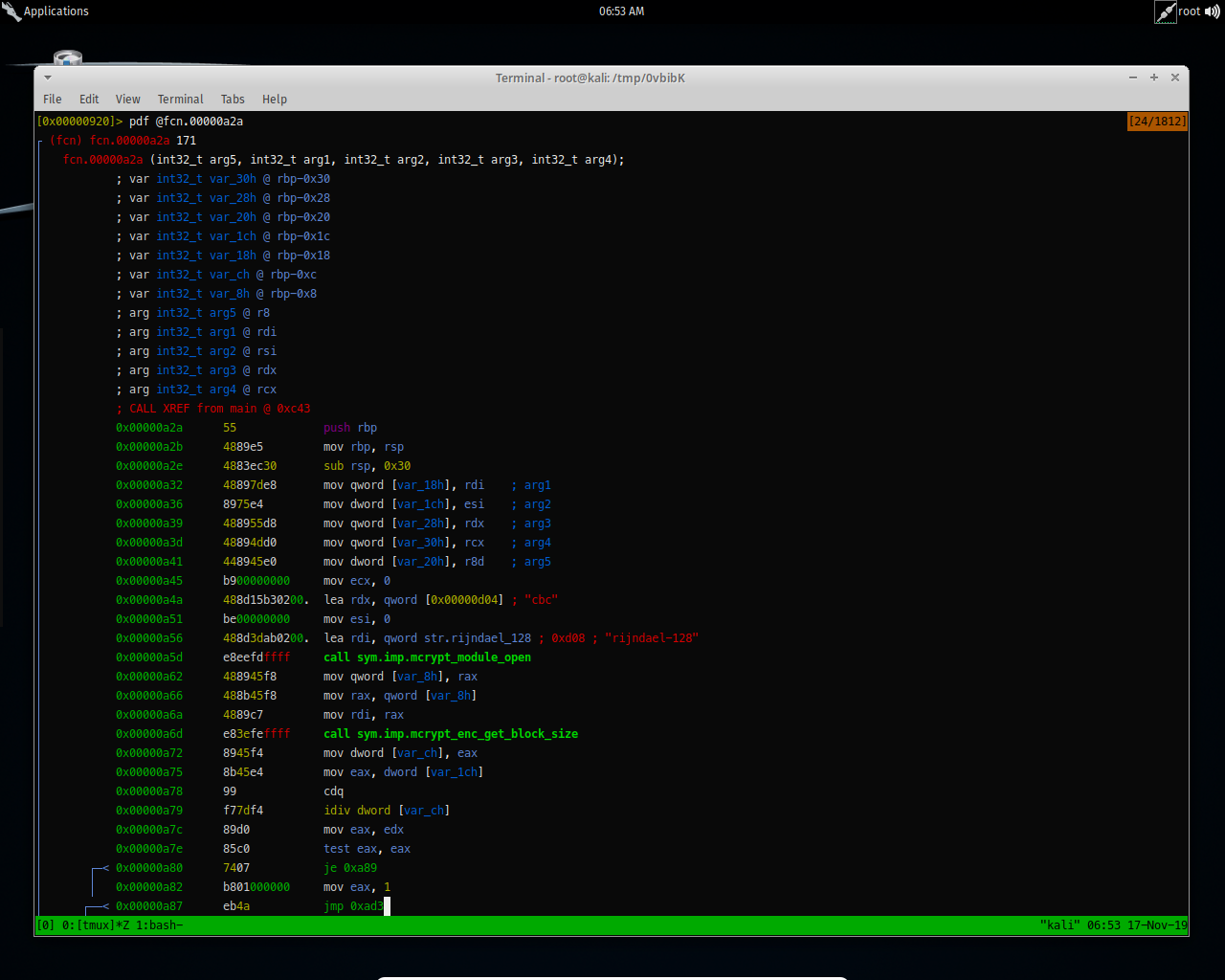
So it’s using mcrypt module which is an encryption/decryption liberary and it’s using CBC Mode and Rijndael-128 algorithm to decrypt the flag.
Solving
Now lets run the binary again and tracing the library call by using ltrace
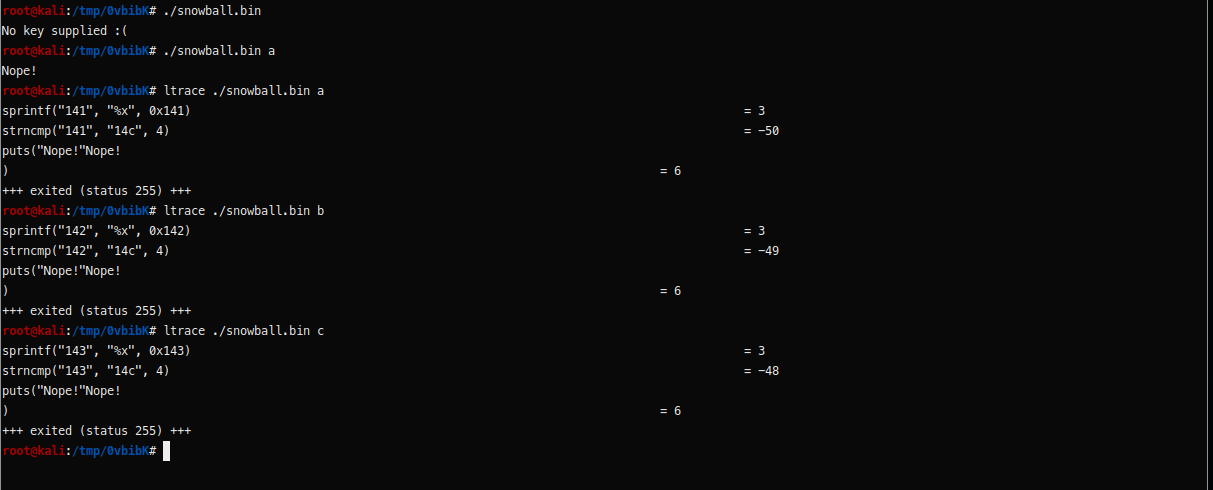
Looks like it’s counting by hex value of the ascii character given to the binary and comparing to a hex value 14c, so what i will do is something like bruteforcing the binary and get our flag. I have created a python script to automate this task, The script easy to understand.
#!/usr/bin/python
import subprocess
import string
from colorama import Fore
ascii_low = string.ascii_lowercase
bin_path = "/tmp/0vbibK/snowball.bin"
for i in range(len(ascii_low)):
popen = subprocess.Popen([bin_path, ascii_low[i]], stdout=subprocess.PIPE)
output = popen.stdout.read()
if "EGCTF" in output:
print(Fore.GREEN + output.strip('\n'))
Now run our script..
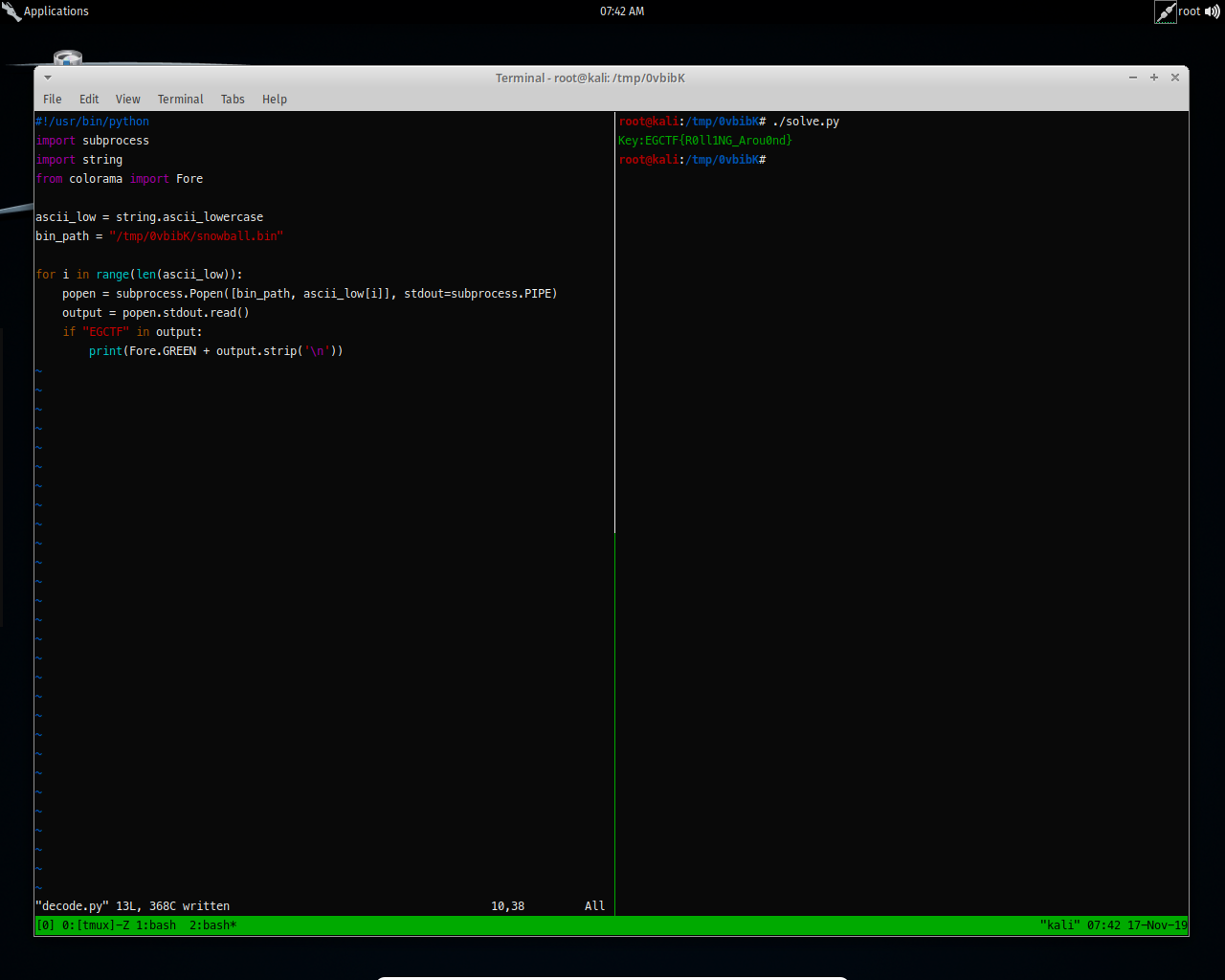
And here it is, the flag.
EGCTF{R0ll1NG_Arou0nd}